
Best Practices for Inter-Service Communication in Microservices Architectures
Microservices architecture presents a significant challenge: effective inter-service communication. This article delves into the crucial aspects of ma...
167 posts in this category

Microservices architecture presents a significant challenge: effective inter-service communication. This article delves into the crucial aspects of ma...

Infrastructure as Code (IaC) is transforming modern IT by allowing infrastructure management through code, automating processes and enhancing efficien...

This article provides a comprehensive introduction to Kubernetes, the leading platform for container orchestration. It demystifies the complexities of...
Kubernetes excels at orchestrating container lifecycles, providing the foundation for efficient application deployment, management, and scaling. This...

This comprehensive guide delves into the crucial process of establishing a CI/CD pipeline for microservices, a key strategy for boosting software deve...

This comprehensive guide explores the essential best practices for creating effective API documentation, crucial for developer adoption and success. F...

This article provides a comprehensive guide to building custom Docker images from scratch, empowering developers to precisely tailor their containeriz...

This article provides a comprehensive overview of the Event Sourcing pattern, delving into its core principles, architecture, and benefits compared to...

Successfully scaling Factor VIII production requires innovative strategies, and this article explores how the process model for concurrency can revolu...

This guide provides a comprehensive roadmap for organizations seeking to adopt a DevOps culture, emphasizing streamlined processes, improved collabora...
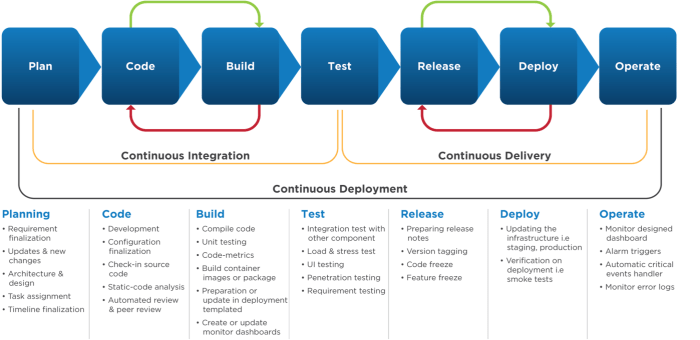
This comprehensive guide delves into the world of CI/CD pipelines, explaining their core concepts and outlining the significant advantages they offer...
This article dives into the crucial concept of disposability within the framework of 12-factor applications, highlighting its importance in modern clo...