
Policy as Code for Cloud Governance: A Comprehensive Guide
Cloud governance is essential for successful cloud adoption, and "policy as code" is revolutionizing how organizations manage and secure their environ...
152 posts in this category

Cloud governance is essential for successful cloud adoption, and "policy as code" is revolutionizing how organizations manage and secure their environ...
This comprehensive guide provides a roadmap for understanding and implementing the National Institute of Standards and Technology (NIST) Cybersecurity...

Enhance your cybersecurity strategy by learning how to set up a honeypot, a valuable tool designed to attract and analyze potential attackers. This gu...

Managing third-party contractor access is a crucial element of robust cybersecurity. This guide outlines essential strategies for securely granting ac...
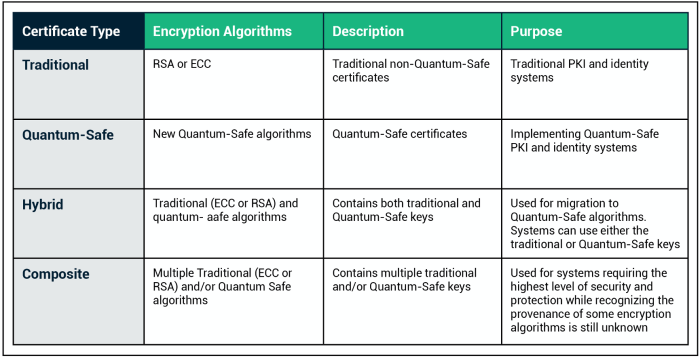
Explore the groundbreaking field of quantum cryptography and its revolutionary impact on cybersecurity in this comprehensive article. From fundamental...

Data classification is a fundamental practice in information security, involving the categorization of data based on its sensitivity and importance. T...

Handling Data Subject Access Requests (DSARs) is a critical component of GDPR compliance. This comprehensive guide offers a clear and detailed roadmap...
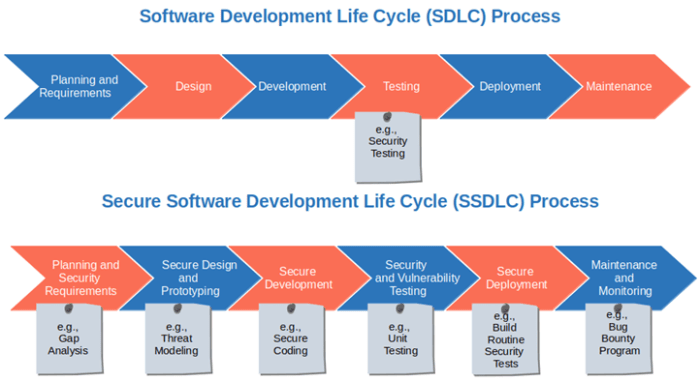
Protecting your software from vulnerabilities is paramount in today's digital world, and this guide provides a comprehensive approach to implementing...
In the world of interconnected microservices, secure service-to-service communication is critical. Mutual Transport Layer Security (mTLS) provides a p...

This article comprehensively explores the "Right to Be Forgotten," a critical aspect of data privacy laws, detailing its origins, legal frameworks, an...

This comprehensive guide to Cloud Identity and Access Management (IAM) explores core concepts, best practices, and emerging trends to secure your clou...
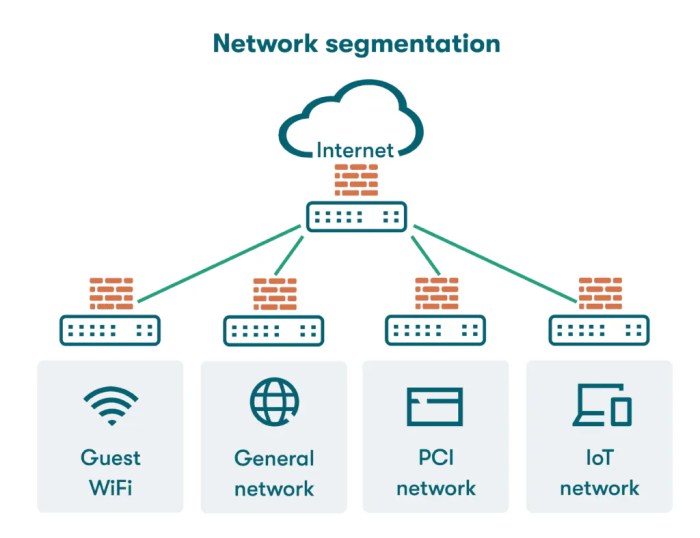
This comprehensive guide provides a deep dive into network segmentation, a crucial strategy for bolstering your organization's security posture. From...