
Legal Hold and eDiscovery in the Cloud: A Comprehensive Guide
This article delves into the intricacies of legal hold and eDiscovery, focusing on the significant advantages of leveraging cloud technology for these...
152 posts in this category

This article delves into the intricacies of legal hold and eDiscovery, focusing on the significant advantages of leveraging cloud technology for these...
This article provides a thorough exploration of phishing attacks, outlining their deceptive tactics and potential impact on your digital security. Lea...

In today's evolving digital landscape, cloud security certifications are crucial for professionals seeking to validate their expertise and advance the...
This comprehensive guide provides a detailed roadmap for implementing Single Sign-On (SSO) across your enterprise applications. From understanding the...
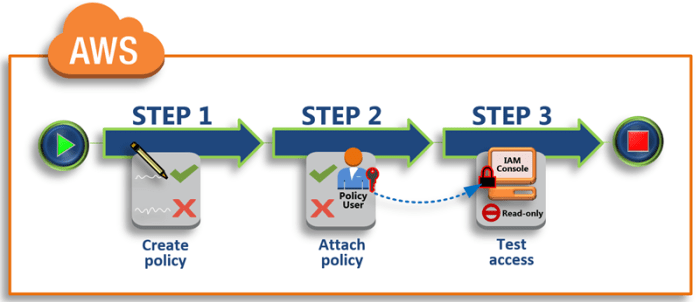
This comprehensive guide delves into the world of Identity and Access Management (IAM) policies, explaining their crucial role in securing access to y...
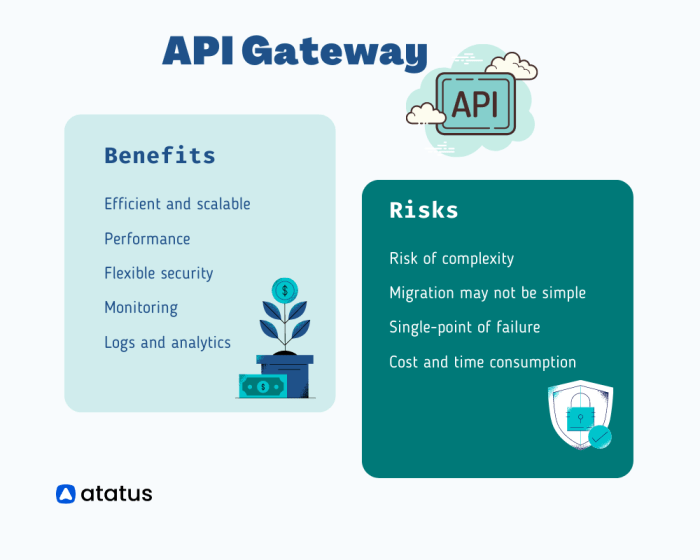
API gateways are vital components of modern application architectures, acting as the primary point of entry and security for all API traffic. Understa...

Organizations face increasing cyber threats, making robust security awareness training for employees crucial. This comprehensive guide provides a step...
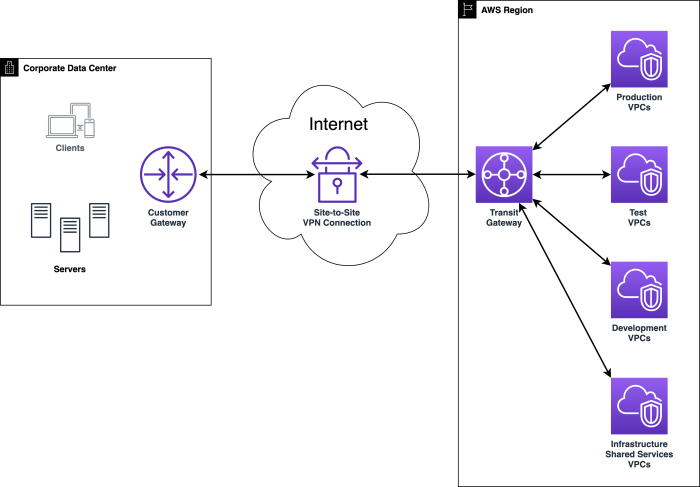
Understand the critical role of Virtual Private Networks (VPNs) in securing modern corporate communications. This article explores the core functional...
This comprehensive guide delves into the critical aspects of secure logging and monitoring within cloud environments, exploring its fundamental concep...

Prepare for the future of cybersecurity with a comprehensive guide to Post-Quantum Cryptography (PQC). This article delves into the fundamental concep...

This article provides a comprehensive overview of Static Application Security Testing (SAST), exploring its core principles, role within the Software...

This article provides a comprehensive guide to Tactics, Techniques, and Procedures (TTPs), crucial elements for understanding and combating cyber thre...