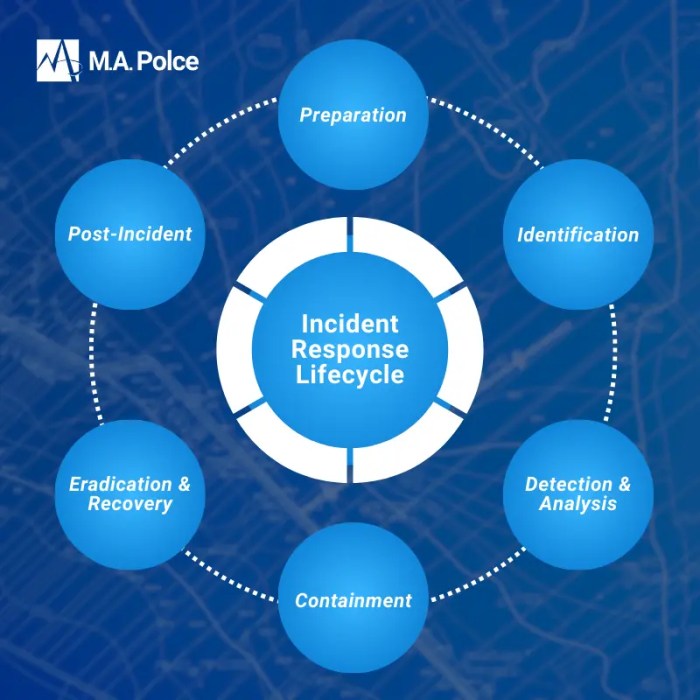
Tabletop Exercises for Incident Response: Definition, Benefits, and Best Practices
In the face of ever-evolving cyber threats, tabletop exercises are vital for strengthening an organization's incident response capabilities. These dyn...
152 posts in this category

In the face of ever-evolving cyber threats, tabletop exercises are vital for strengthening an organization's incident response capabilities. These dyn...

This article explores the pivotal role of service meshes in securing modern, microservices-based application architectures. It highlights how service...

This article delves into the critical process of de-provisioning user accounts, explaining its definition, triggers, and the vital role it plays in bo...

This comprehensive article explores the evolving landscape of cloud security, addressing current threats and vulnerabilities while examining the impac...

Safeguarding your cloud environment begins with a thorough vulnerability assessment. This guide provides a structured approach to identifying and miti...

This article delves into the critical practice of Continuous Compliance Monitoring (CCM) in cloud environments, explaining its core concepts and showc...
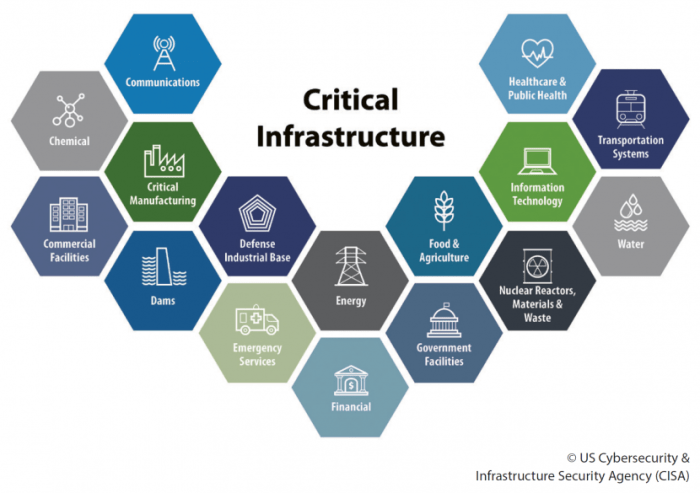
This article provides a comprehensive guide to implementing CIS Benchmarks for cloud hardening, covering crucial aspects from understanding the benchm...

This article provides a comprehensive guide to managing secrets and encryption keys in the cloud, a critical aspect of cloud security. It explores fun...
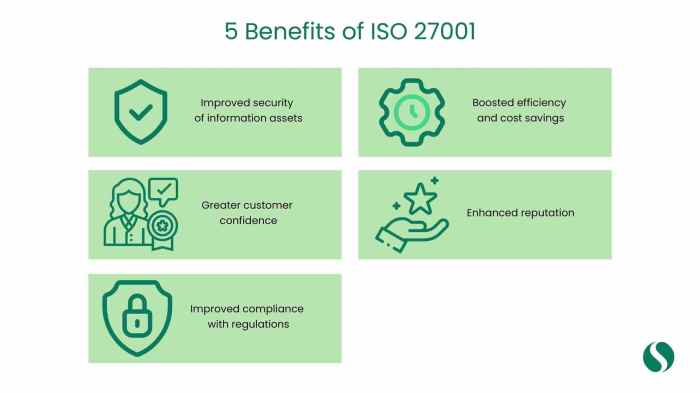
This comprehensive guide provides a detailed roadmap for achieving ISO 27001 certification, covering everything from understanding the core principles...
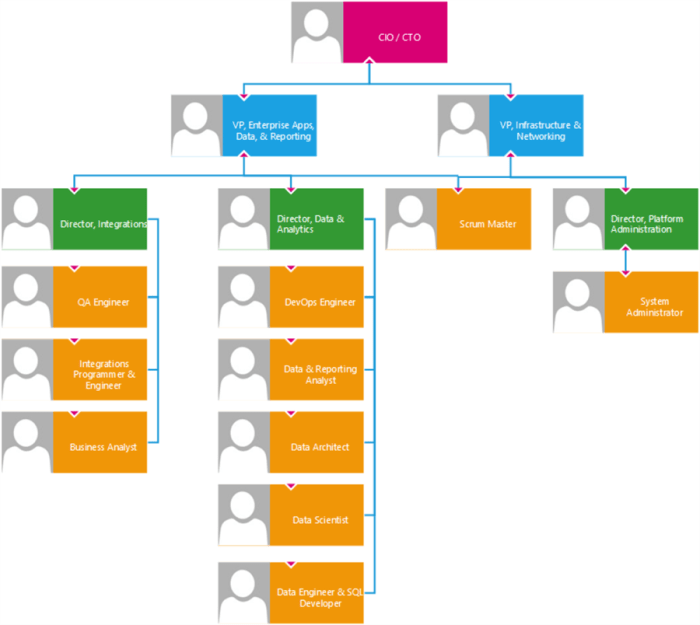
Cloud computing's scalability demands stringent security measures, making clear role and responsibility definitions for cloud access paramount. This a...

Organizations leveraging multi-cloud environments face a complex landscape of security risks, including data breaches, identity and access management...

This article delves into the OWASP Top 10, the definitive guide to web application security risks. It provides a comprehensive overview of the most c...