Cyber Insurance: Coverage, Benefits, and What You Need to Know
In an era defined by digital interconnectedness, cyber insurance has become a critical safeguard for businesses facing persistent online threats. This...
152 posts in this category

In an era defined by digital interconnectedness, cyber insurance has become a critical safeguard for businesses facing persistent online threats. This...
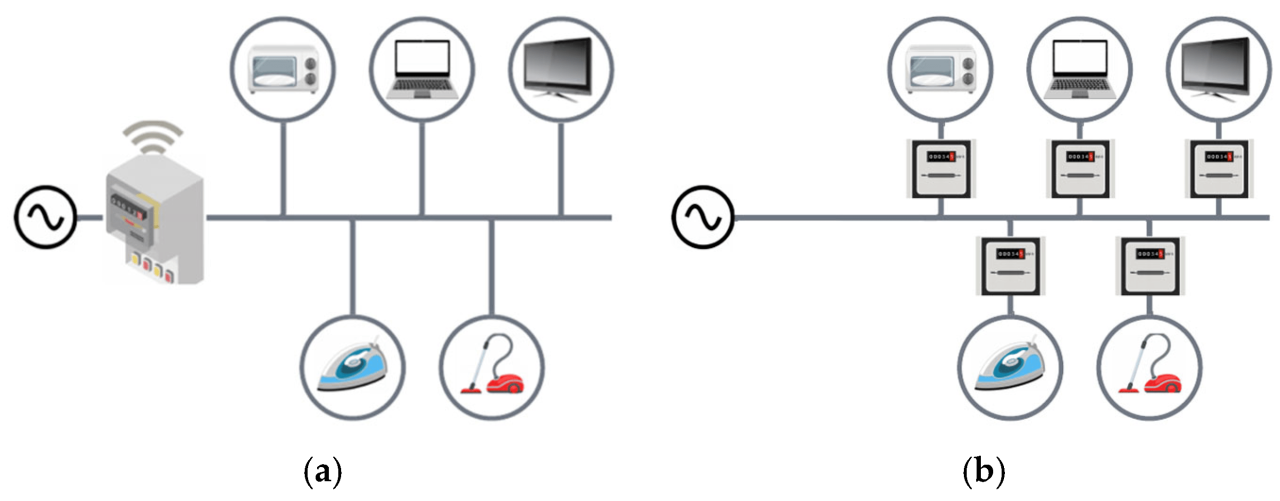
Facing an increasingly complex cyber threat landscape, security operations teams need efficient solutions. This article explores how Security Orchestr...
This article explores the critical technical controls necessary for organizations to comply with GDPR regulations concerning data residency and sovere...

In today's dynamic digital landscape, Cloud Security Posture Management (CSPM) is essential for securing your cloud environments. CSPM offers a compre...
Software supply chain security is crucial in today's digital world, safeguarding every phase of software development from planning to deployment. This...

This comprehensive guide provides a roadmap for building a robust Security Operations Center (SOC) specifically designed for the cloud environment. Fr...

This article provides a comprehensive overview of Software Bill of Materials (SBOMs), explaining their definition, purpose, and benefits for various s...

This article provides a comprehensive overview of the roles and responsibilities within a Security Operations Center (SOC), crucial for modern cyberse...
Managing resources across multiple cloud providers like AWS, Azure, and GCP introduces complex challenges for consistent security and access control d...

A security baseline serves as the foundation for robust cybersecurity, providing a standardized configuration for systems and applications to ensure a...
This article provides a comprehensive guide to implementing a Zero Trust security model within cloud environments, covering key principles, asset iden...

Protect your organization from the potential pitfalls of cloud service provider failures with a robust third-party vendor risk assessment program. Thi...