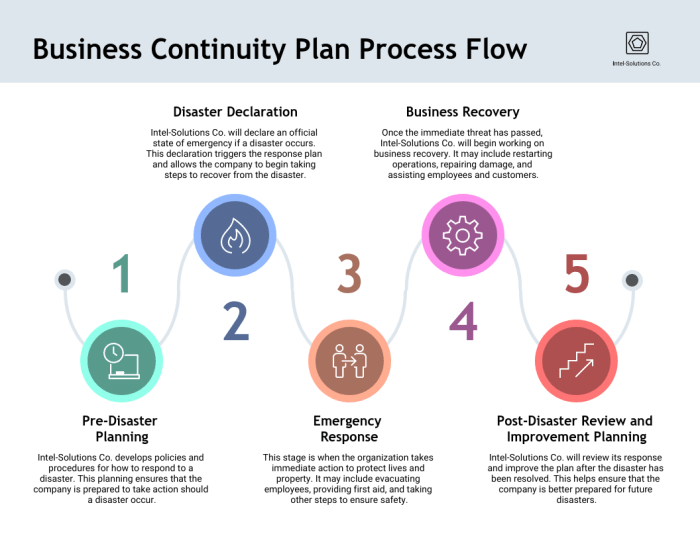
Integrating BCP into Your Disaster Recovery Plan: A Practical Guide
This comprehensive guide explores the essential integration of Business Continuity Planning (BCP) and Disaster Recovery (DR), providing a roadmap to e...
152 posts in this category

This comprehensive guide explores the essential integration of Business Continuity Planning (BCP) and Disaster Recovery (DR), providing a roadmap to e...
In an increasingly cloud-dependent business environment, establishing a strong cloud security team is crucial for protecting valuable data and applica...
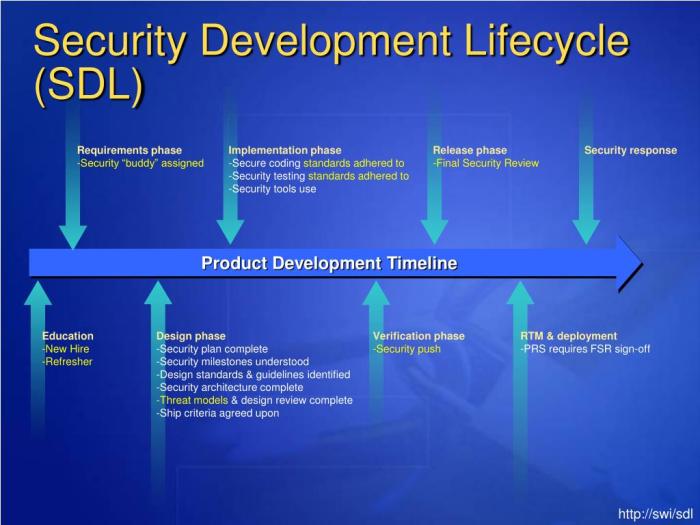
"Shifting security left" is a critical strategy for modern software development, emphasizing the integration of security practices early in the develo...
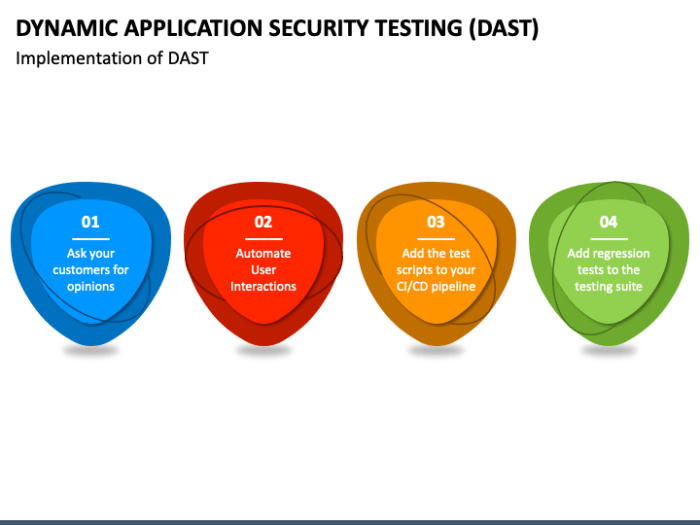
This comprehensive guide explores Dynamic Application Security Testing (DAST), providing a deep dive into its core concepts, functionality, and practi...

This article provides a comprehensive overview of the Common Vulnerabilities and Exposures (CVE) database, detailing its purpose, structure, and the r...
Configuration drift in security settings poses a significant threat, potentially weakening your defenses through unnoticed changes. Proactively monito...

This article provides an introduction to threat modeling using the STRIDE methodology, a critical practice for enhancing software security. Learn how...

This comprehensive guide details the essential skills required to excel as a Cloud Security Engineer, covering core technical competencies like networ...
This article provides a comprehensive overview of endpoint security specifically tailored for cloud workloads, outlining its core concepts, essential...

Effectively securing your cloud infrastructure requires a deep understanding of both Security Groups and Network ACLs. This comprehensive guide delves...
In the face of escalating cyber threats, protecting web applications is more critical than ever. This article delves into the essential function of We...

Protecting sensitive data within big data platforms demands a comprehensive approach encompassing encryption, access control, data governance, and rob...