
Securing Your Data Lake: Best Practices and Strategies
Safeguarding a data lake environment requires a multi-faceted approach. This article provides a comprehensive guide to securing your data lake, coveri...
152 posts in this category

Safeguarding a data lake environment requires a multi-faceted approach. This article provides a comprehensive guide to securing your data lake, coveri...

Securing your critical digital assets starts with effective Privileged Access Management (PAM). This article provides a comprehensive, practical guide...

Kubernetes Pod Security Policies (PSPs) are crucial for bolstering the security of your containerized applications within a Kubernetes cluster. These...

This article provides a comprehensive overview of User and Entity Behavior Analytics (UEBA), exploring its core concepts, components, and practical ap...

Navigate the complex legal landscape of cloud computing with this comprehensive guide. This article delves into critical areas like data privacy regul...

This comprehensive guide provides a detailed overview of FedRAMP, the critical security authorization program for cloud services used by the U.S. gove...

Navigating the complexities of cloud security requires a proactive approach, beginning with a comprehensive incident response plan. This guide highlig...

A Business Continuity Plan (BCP) is essential for any organization seeking to minimize disruption and maintain operational resilience in the face of u...

Cloud environments present unique challenges for security forensics, but understanding the core principles is crucial for effective investigation. Thi...
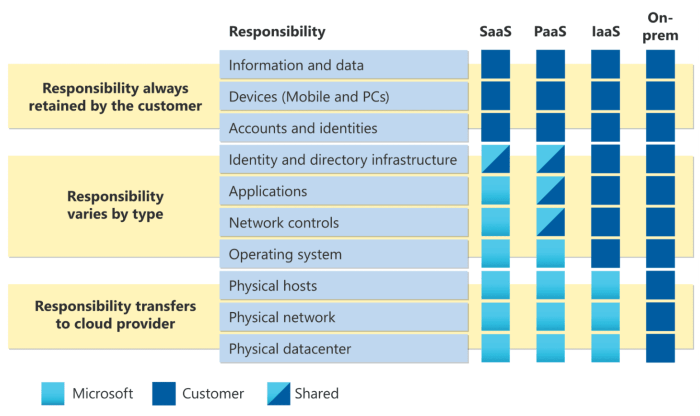
This article explores the critical need to protect "data in use," delving into the inherent security risks and challenges associated with active compu...
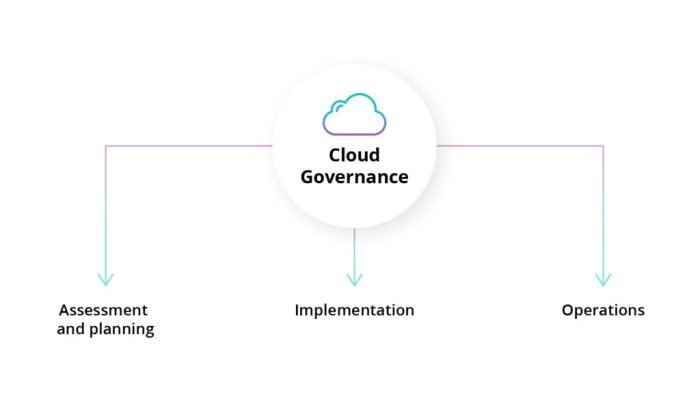
Establishing a formal cloud security governance framework is crucial for protecting valuable assets and maintaining compliance in the cloud. This fram...
The proliferation of Internet of Things (IoT) devices necessitates robust security measures to protect against increasingly sophisticated cyber threat...