AI's Transformation of Cybersecurity: Challenges and Opportunities
Artificial intelligence is rapidly transforming the cybersecurity landscape, offering powerful new tools for threat detection, incident response, and...
152 posts in this category

Artificial intelligence is rapidly transforming the cybersecurity landscape, offering powerful new tools for threat detection, incident response, and...

This guide provides a comprehensive roadmap for establishing robust threat hunting capabilities, essential for proactively identifying and mitigating...

This comprehensive guide explores the critical importance of securing your software dependencies, outlining potential risks from supply chain attacks...

This article provides a comprehensive guide to preventing SQL injection attacks specifically within cloud application environments. It covers critical...

This article provides a comprehensive overview of runtime security for containers, emphasizing its critical role in protecting containerized applicati...

Privacy-preserving computation offers a groundbreaking approach to data security, enabling the processing of encrypted data without the need for decry...
This article offers a comprehensive guide to negotiating robust security provisions within your cloud service level agreement (SLA). It covers critica...

This comprehensive guide explores the critical concepts of data anonymization and pseudonymization, essential practices for protecting sensitive infor...
Protecting sensitive data in the digital age demands robust security measures. This guide provides a detailed overview of enforcing strong authenticat...
This comprehensive guide delves into the intricacies of OAuth 2.0 and OpenID Connect, explaining their roles in modern authentication and authorizatio...
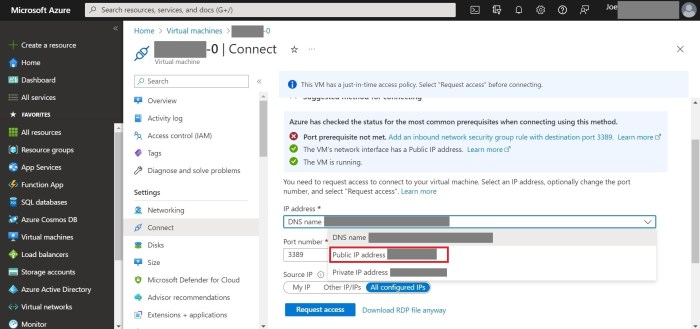
This article delves into the critical concept of Just-in-Time (JIT) access for cloud resources, exploring its core principles and the significant secu...
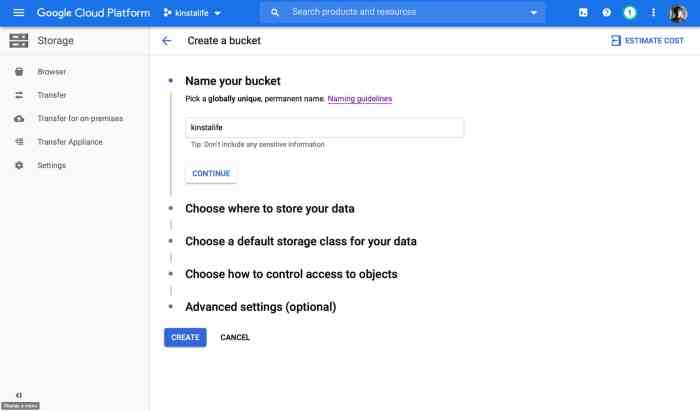
With the increasing reliance on cloud storage, securing your buckets from misconfiguration is crucial. This article delves into the unique security ch...