
Using the MITRE ATT&CK Framework: A Practical Guide
This comprehensive guide delves into the MITRE ATT&CK framework, providing a roadmap for understanding its structure and leveraging its capabilities t...
152 posts in this category

This comprehensive guide delves into the MITRE ATT&CK framework, providing a roadmap for understanding its structure and leveraging its capabilities t...
Protecting your organization from internal cybersecurity risks is paramount. This guide, "How to Detect and Respond to Insider Threats," offers a comp...

This comprehensive guide provides a detailed overview of securing the Kubernetes control plane, covering essential aspects from authentication and aut...
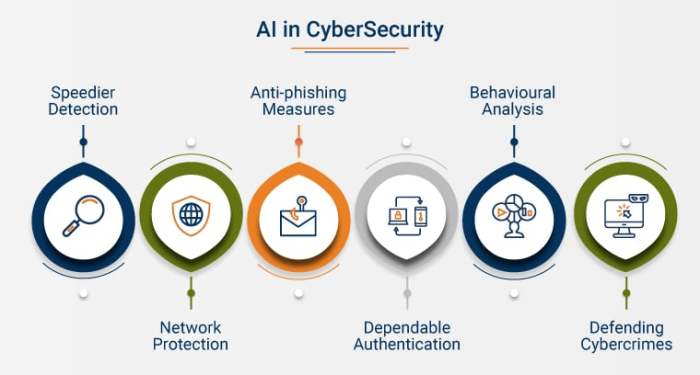
This article explores the vital integration of threat intelligence into cloud security operations, a crucial step in defending against modern cyber th...
This comprehensive guide outlines the crucial steps for conducting regular cloud security risk assessments, ensuring the protection of your valuable a...

This comprehensive guide provides a crucial roadmap for securing Infrastructure as Code (IaC) templates, addressing the inherent security challenges o...

This comprehensive article delves into the emerging field of Confidential Computing, defining its core concepts, key technologies, and significant ben...

Navigating HIPAA compliance in the cloud requires a strategic approach that addresses data security, access controls, and disaster recovery. This comp...
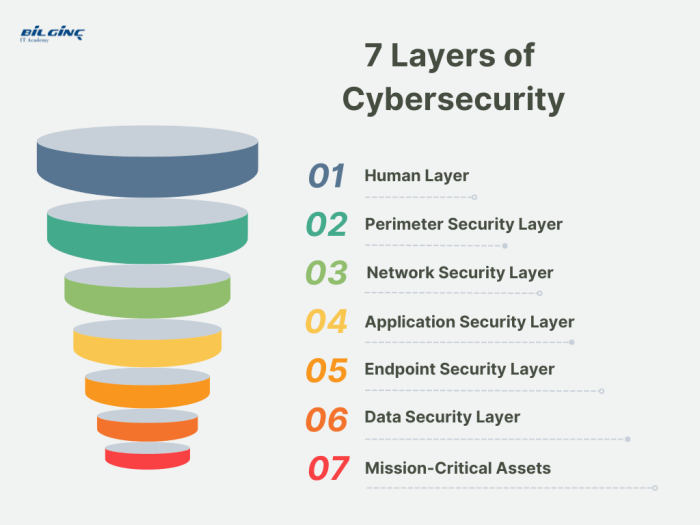
Defense in depth is a critical cybersecurity principle that emphasizes a layered approach to security, acknowledging that no single measure is impenet...

Data security is crucial for modern businesses, highlighting the need for effective backup and disaster recovery (BDR) strategies. This guide provides...

This comprehensive guide explores the ISO 27001 standard, a globally recognized framework for information security management. From its core principl...

In the modern cloud-centric business environment, robust data and infrastructure security is critical. Security Information and Event Management (SIEM...