
SOC 2 Compliance in the Cloud: A Comprehensive Guide
Navigating SOC 2 compliance in a cloud environment requires a strategic approach, and this article provides a comprehensive guide. It covers essential...
152 posts in this category

Navigating SOC 2 compliance in a cloud environment requires a strategic approach, and this article provides a comprehensive guide. It covers essential...
This article provides a comprehensive guide to preventing Cross-Site Scripting (XSS) attacks, detailing the fundamental concepts, various attack types...

In today's data-driven world, protecting sensitive information is critical, and Key Management Services (KMS) are essential for achieving this. This a...

This comprehensive guide explores the multifaceted landscape of container security, outlining critical best practices to protect your deployments from...

This comprehensive guide explores the critical aspects of securing serverless applications and functions, covering everything from authentication and...

This guide provides a comprehensive overview of how to launch a successful career in the dynamic field of cloud security. It offers practical advice a...
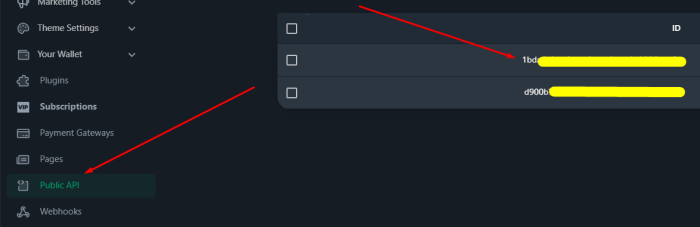
Protecting sensitive API keys and tokens is crucial for maintaining application security and preventing costly data breaches. This article provides a...
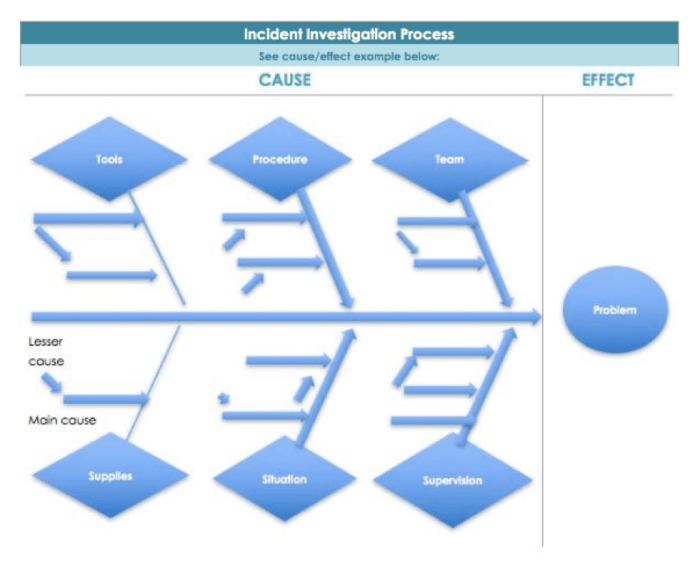
This article provides a comprehensive guide to performing a Root Cause Analysis (RCA) following a security incident, a crucial skill in today's digita...
Cybersecurity is a dynamic field, and bolstering your security posture requires a proactive, ongoing approach. This article outlines a strategic frame...

Discover insights and practical tips in this comprehensive guide about What Are The Compliance Requirements For Data Breach Notifications.

This comprehensive guide delves into the critical role of Cloud Workload Protection Platforms (CWPP) in modern cloud security, exploring its core conc...

Safeguarding your digital assets requires vigilant monitoring for unauthorized file changes. This article explores the critical importance of detectin...