
Key Management Service (KMS): Definition, Benefits, and Best Practices
In today's data-driven world, protecting sensitive information is critical, and Key Management Services (KMS) are essential for achieving this. This a...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

In today's data-driven world, protecting sensitive information is critical, and Key Management Services (KMS) are essential for achieving this. This a...
This article provides a comprehensive guide to preventing Cross-Site Scripting (XSS) attacks, detailing the fundamental concepts, various attack types...
This comprehensive article delves into the transformative technology of homomorphic encryption, exploring its core functionality, diverse types, and u...
This article provides a comprehensive overview of Bring Your Own License (BYOL) in the cloud, exploring its core concepts, benefits, and potential cha...

Creating a compelling business case is essential for successful cloud migration projects. This strategic shift requires articulating the value proposi...

This comprehensive guide delves into the Saga pattern, a critical architectural approach for managing distributed transactions in microservices enviro...
This article delves into the critical concept of graceful degradation, exploring how to design systems that maintain functionality and user experience...
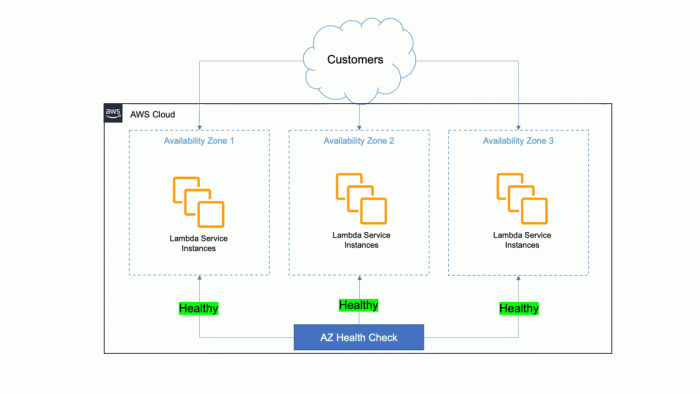
This comprehensive article delves into the distinctions between AWS Lambda and Fargate, two prominent serverless computing options. Through detailed a...
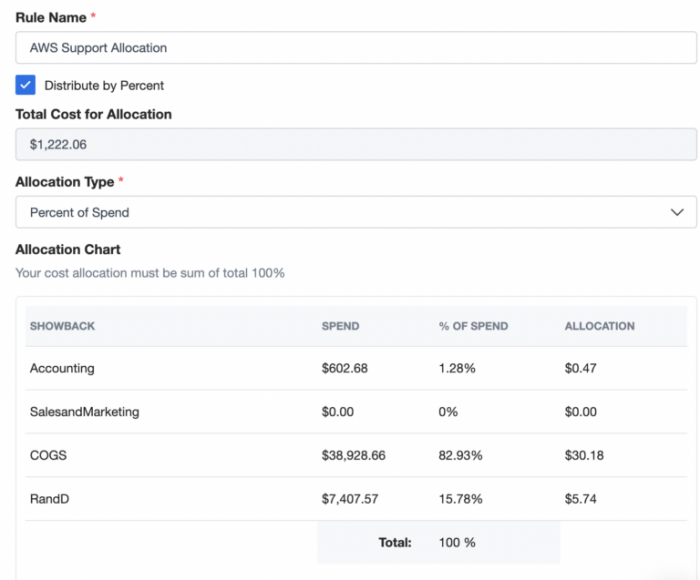
Transitioning from showback to chargeback can significantly improve cost transparency and accountability within your organization. This article provid...

Prepare for the future of cybersecurity with a comprehensive guide to Post-Quantum Cryptography (PQC). This article delves into the fundamental concep...

This comprehensive guide delves into the critical practice of container vulnerability scanning, explaining its core concepts and importance in securin...

This article delves into the critical topic of leader election in distributed systems, exploring various algorithms, from centralized to decentralized...