
Cloud Migration ROI: Measuring the Value of Your Move
This article provides a comprehensive guide to understanding and calculating the Return on Investment (ROI) of cloud migration. It delves into cost an...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

This article provides a comprehensive guide to understanding and calculating the Return on Investment (ROI) of cloud migration. It delves into cost an...

This article explores the critical role of automation in modern migration factories, detailing how it streamlines complex processes. From automated da...
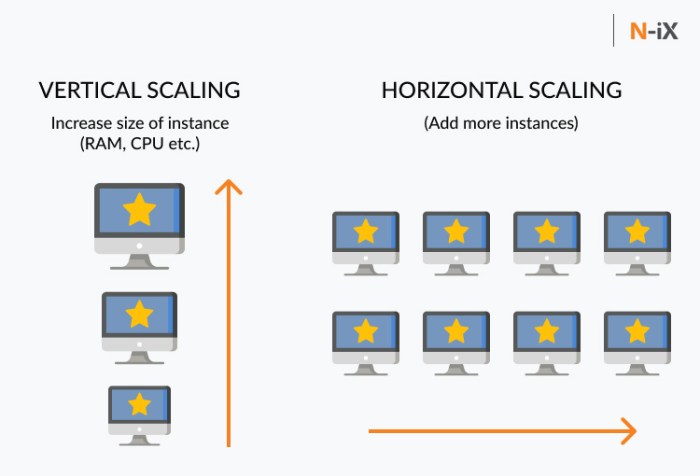
This article delves into the world of serverless databases, exploring their core concepts, evolution, and advantages over traditional systems. You'll...
Building a centralized FinOps team is essential for effectively managing cloud costs and maximizing efficiency. This comprehensive guide offers a prac...
This comprehensive guide delves into the essential practice of end-to-end (E2E) testing for web applications, a critical step in ensuring application...
This comprehensive guide delves into the world of webhooks and their critical role within event-driven architectures. From fundamental concepts and te...

Cloud-based database schema transformation is a vital process for optimizing database structures, ensuring they align with evolving business needs and...
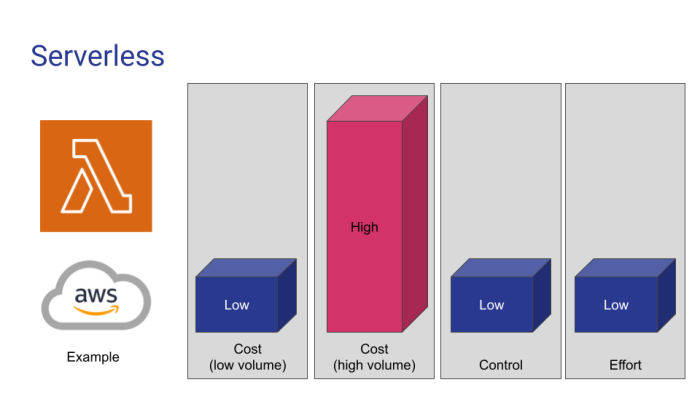
Serverless architecture presents unique debugging challenges due to its cloud-based nature, often requiring time-consuming deployments for issue ident...
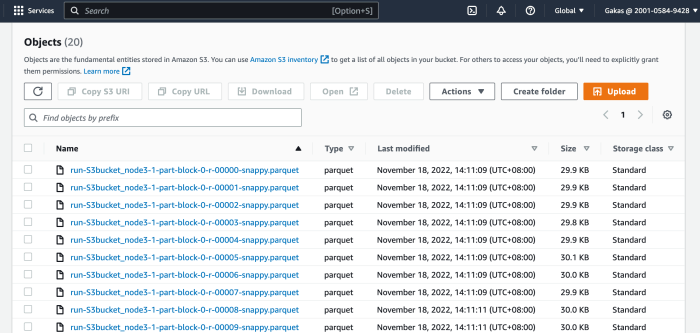
Modern data management requires efficient and scalable solutions, and serverless computing is revolutionizing how we ingest data into data lakes. This...

Cloud computing financial strategies are largely defined by the distinction between Capital Expenditure (CAPEX) and Operational Expenditure (OPEX) mod...

Serverless API gateway proxy integration is a fundamental concept in modern serverless architecture, acting as a critical link between client applicat...

This article provides a comprehensive analysis of proactive versus reactive security strategies, detailing their core principles, advantages, and limi...