
Security Baseline: Definition and a Step-by-Step Guide to Implementation
A security baseline serves as the foundation for robust cybersecurity, providing a standardized configuration for systems and applications to ensure a...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

A security baseline serves as the foundation for robust cybersecurity, providing a standardized configuration for systems and applications to ensure a...
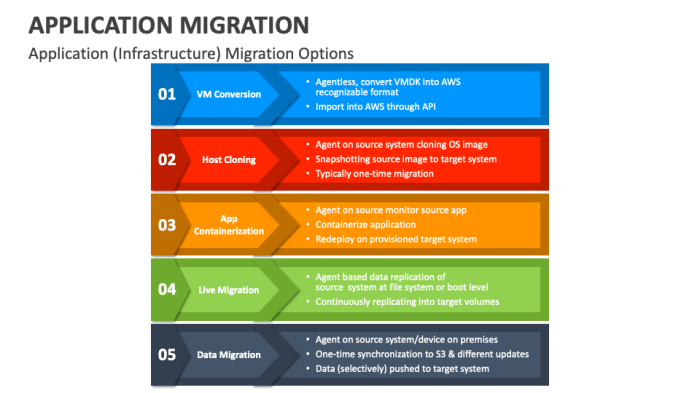
Organizations are increasingly migrating applications to optimize resources and drive operational efficiency. This process necessitates a thorough ass...
Embarking on a cloud migration requires a thorough understanding of your organization's readiness. This comprehensive guide provides a step-by-step ap...
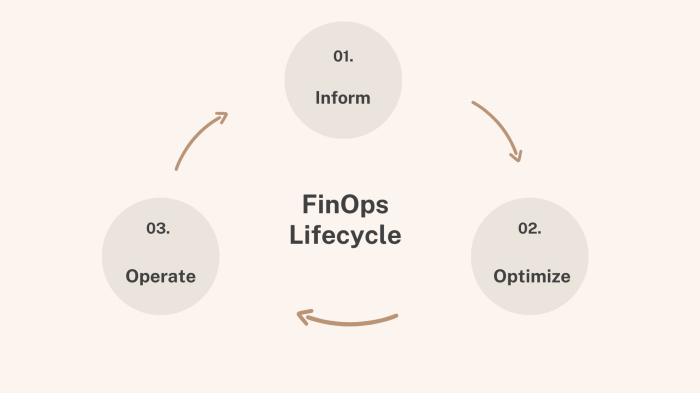
This article explores the innovative application of gamification within the FinOps framework to drive cloud cost savings. Learn how to design engagin...

This article explores the concept of a FinOps playbook, a crucial framework for optimizing cloud spending through collaboration between technology, fi...
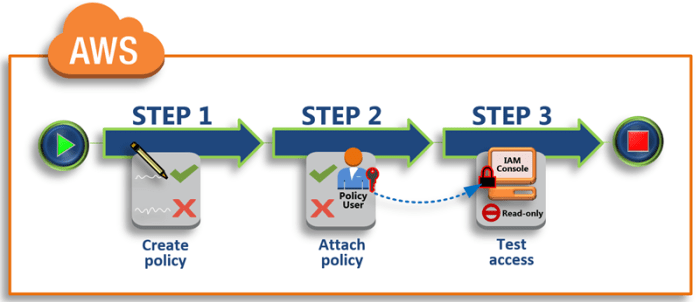
This comprehensive guide delves into the world of Identity and Access Management (IAM) policies, explaining their crucial role in securing access to y...
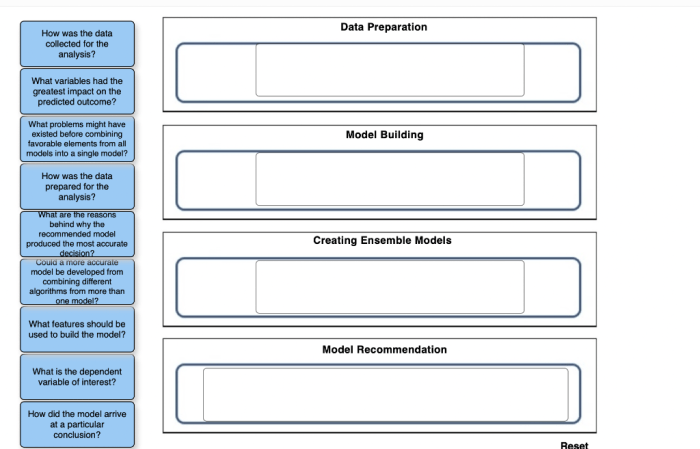
Automated rightsizing, powered by machine learning, is transforming cloud computing by dynamically optimizing resource allocation for peak performance...
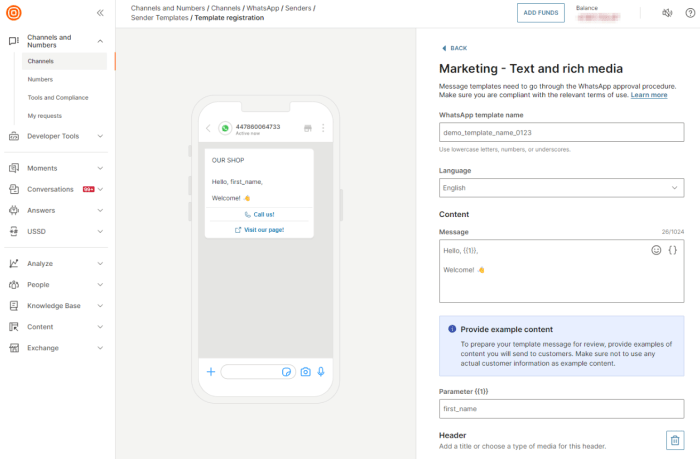
This comprehensive guide provides a step-by-step approach to designing a robust cloud storage backup strategy, covering crucial aspects from defining...

Hexagonal architecture leverages ports and adapters to isolate the core application logic from external concerns. This design pattern enhances softwar...
This article delves into the core concept of a FinOps iteration, providing a practical guide to navigating the dynamic world of cloud financial manage...

In the ever-demanding digital world, maintaining constant access to online services is crucial for businesses and users. This article explores the vit...

Organizations leveraging multi-cloud environments face a complex landscape of security risks, including data breaches, identity and access management...