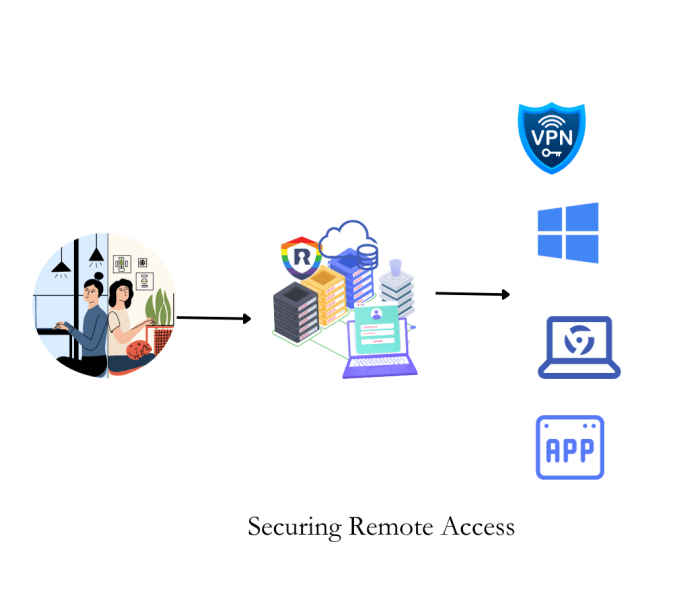
Securing Remote Access to Cloud Environments: Best Practices & Strategies
Securing remote access to cloud environments is paramount in today's interconnected landscape, yet presents significant security challenges. This guid...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

Securing remote access to cloud environments is paramount in today's interconnected landscape, yet presents significant security challenges. This guid...
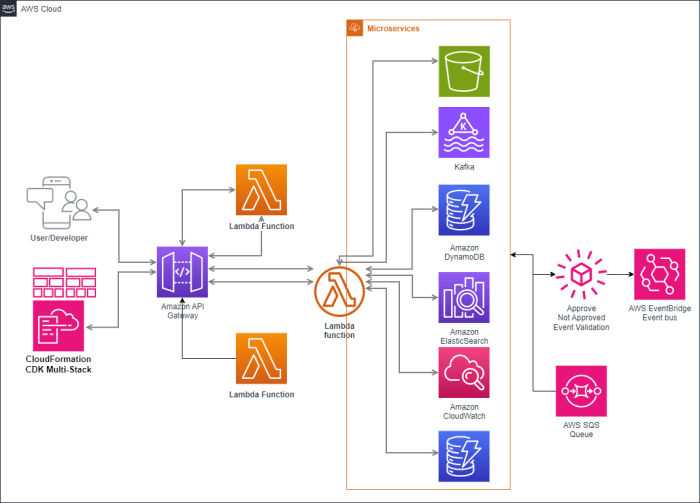
This comprehensive guide explores the power of the AWS Cloud Development Kit (CDK) for infrastructure provisioning, offering a deep dive into its bene...
DevSecOps fundamentally transforms software development by embedding security practices throughout the entire lifecycle, from inception to deployment....

This article delves into the critical practice of Continuous Compliance Monitoring (CCM) in cloud environments, explaining its core concepts and showc...
This article provides a comprehensive overview of stream processing architecture, exploring its core concepts, components, and applications. From unde...
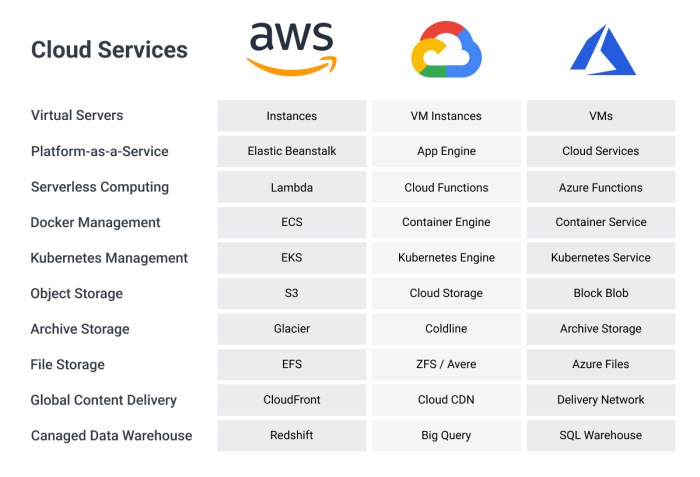
Migrating to the cloud requires careful planning and selection of the right provider. This comprehensive guide walks you through the critical consider...

Gaining control over your organization's finances begins with understanding cost categories. This article explores how grouping expenditures into logi...

This article provides a comprehensive guide to tracking the business value of cloud investments, moving beyond simple cost savings to explore broader...
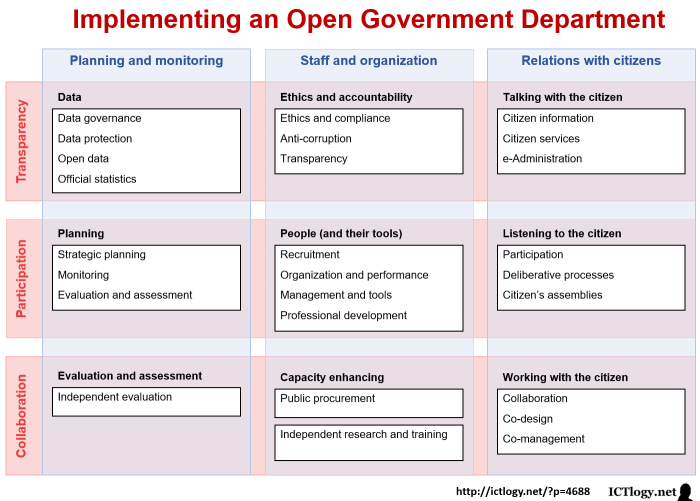
This comprehensive guide explores the transformative power of Zero Trust Network Access (ZTNA) in modern cybersecurity, outlining its core principles...
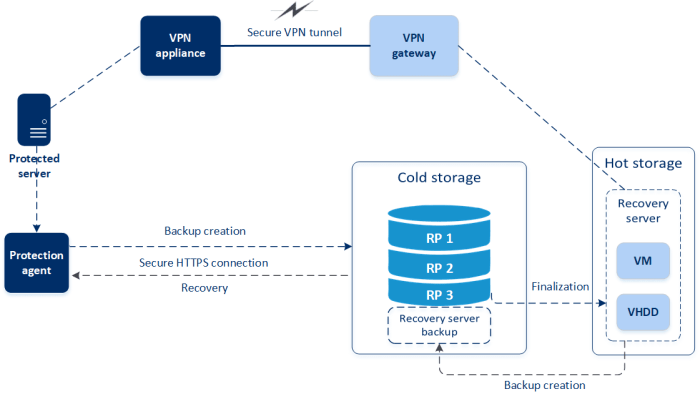
Ensuring the reliability of your systems post-migration necessitates rigorous testing of failover and redundancy mechanisms. This article provides a c...
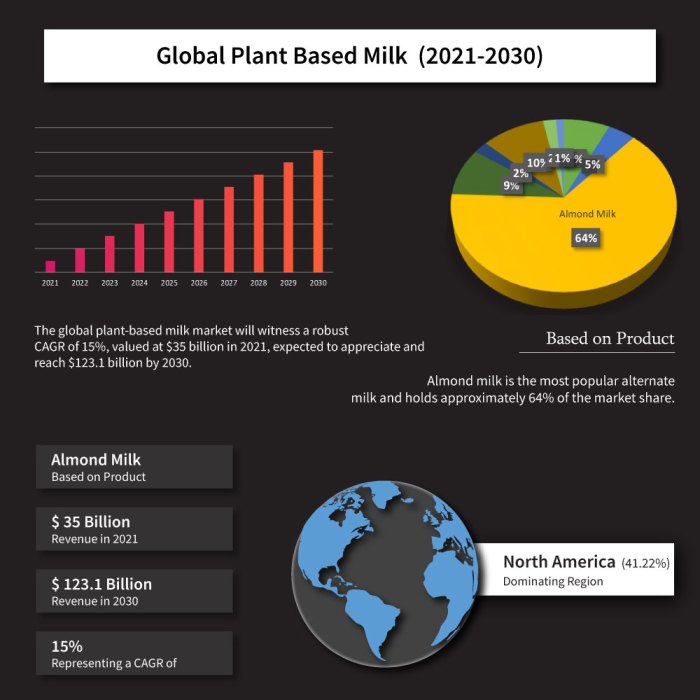
Cybersecurity is a dynamic field, and bolstering your security posture requires a proactive, ongoing approach. This article outlines a strategic frame...
In the world of interconnected microservices, secure service-to-service communication is critical. Mutual Transport Layer Security (mTLS) provides a p...