Designing a secure and compliant landing zone is paramount for organizations migrating to or operating within the cloud. It represents the foundational environment upon which all cloud-based workloads are built, dictating security posture, compliance adherence, and operational efficiency. This guide provides a structured approach to establishing a robust landing zone, covering key aspects from initial planning to ongoing management and optimization.
This guide will navigate the complexities of cloud security, focusing on essential elements such as network architecture, identity and access management, data protection, and automation. We will explore compliance frameworks, disaster recovery strategies, and the practical application of Infrastructure as Code (IaC). The goal is to equip readers with the knowledge and tools to create a landing zone that meets stringent security requirements and industry-specific compliance mandates, ensuring the confidentiality, integrity, and availability of critical data and systems.
Defining a Secure and Compliant Landing Zone
A secure and compliant landing zone is a foundational element of cloud infrastructure, representing a well-architected and controlled environment for deploying and managing workloads. It serves as the entry point for all cloud resources, establishing the necessary security, governance, and compliance controls. The goal is to provide a consistent and secure foundation that aligns with organizational policies and regulatory requirements.
Core Principles of a Secure Landing Zone
The design of a secure landing zone is governed by several core principles, each playing a critical role in establishing a robust and compliant cloud environment. Adherence to these principles ensures a strong security posture and facilitates effective governance.
- Identity and Access Management (IAM): Centralized management of user identities, roles, and permissions is paramount. This includes the use of multi-factor authentication (MFA), role-based access control (RBAC), and the principle of least privilege. For example, in AWS, IAM users, groups, and roles define access rights, and policies restrict actions based on the user’s identity.
- Network Security: Implementing robust network segmentation, firewalls, and intrusion detection/prevention systems (IDS/IPS) is crucial. This isolates workloads, controls traffic flow, and protects against unauthorized access. Consider the use of Virtual Private Clouds (VPCs) with security groups and network access control lists (NACLs) to control network traffic.
- Data Protection: Data encryption, both in transit and at rest, is essential to protect sensitive information. Regular backups, disaster recovery plans, and data loss prevention (DLP) measures are also necessary. For example, in Azure, services like Azure Key Vault manage encryption keys, and Azure Storage offers encryption at rest.
- Governance and Compliance: Establishing clear governance policies, automating compliance checks, and maintaining detailed audit logs are vital. This includes the use of infrastructure-as-code (IaC) for consistent deployments and automated compliance scanning tools.
- Monitoring and Logging: Comprehensive monitoring of all resources, coupled with centralized logging, is crucial for detecting security incidents, performance issues, and compliance violations. Log data should be analyzed for security threats and used for auditing purposes.
Compliance Requirements for Various Industries
Different industries face specific compliance requirements, dictating the security and governance measures required within their landing zones. These requirements are driven by regulations, industry standards, and best practices.
- Healthcare (HIPAA): The Health Insurance Portability and Accountability Act (HIPAA) mandates the protection of Protected Health Information (PHI). Compliance requires implementing strict access controls, encryption of data at rest and in transit, regular security audits, and business associate agreements (BAAs) with cloud providers. For instance, cloud providers must offer HIPAA-compliant services and have a BAA in place to be used in the US healthcare sector.
- Finance (PCI DSS): The Payment Card Industry Data Security Standard (PCI DSS) applies to organizations that process, store, or transmit credit card information. Compliance necessitates implementing strong network security, access controls, vulnerability management, and regular security assessments. This includes, for example, segmenting the network to isolate cardholder data environments (CDEs).
- Government (FedRAMP): The Federal Risk and Authorization Management Program (FedRAMP) provides a standardized approach to security assessment, authorization, and continuous monitoring for cloud products and services used by the U.S. federal government. Compliance requires meeting specific security controls and obtaining an authorization to operate (ATO).
- Other Industries: Industries like retail (e.g., GDPR, CCPA), manufacturing (e.g., NIST Cybersecurity Framework), and energy (e.g., NERC CIP) also have specific compliance needs. These regulations and standards require organizations to address data privacy, cybersecurity, and operational resilience.
Critical Security Objectives a Landing Zone Must Achieve
A well-designed landing zone must achieve specific security objectives to protect cloud resources and data. These objectives are fundamental to ensuring a secure and resilient cloud environment.
- Confidentiality: Protecting sensitive data from unauthorized access is a primary objective. This involves implementing encryption, access controls, and data loss prevention measures. For instance, using encryption keys managed by a hardware security module (HSM) provides strong protection for sensitive data.
- Integrity: Ensuring the accuracy and reliability of data and systems is critical. This includes implementing integrity checks, intrusion detection systems, and version control for code and configurations.
- Availability: Maintaining the accessibility of resources and services is essential for business continuity. This involves implementing high availability architectures, disaster recovery plans, and redundancy measures.
- Authentication and Authorization: Verifying user identities and controlling access to resources are fundamental. This includes using multi-factor authentication, role-based access control, and strong password policies.
- Auditability and Accountability: Maintaining comprehensive audit logs and ensuring accountability for all actions are crucial for security and compliance. This involves logging all activities, establishing clear roles and responsibilities, and implementing regular security audits.
Planning and Design Considerations
The planning and design phase is foundational to a secure and compliant landing zone. It establishes the blueprint for cloud infrastructure, defining security postures, governance frameworks, and operational models. This phase demands careful consideration of organizational needs, regulatory requirements, and cloud provider capabilities. The decisions made here significantly impact the long-term security, scalability, and manageability of the cloud environment.
Initial Planning Steps
The initial planning steps involve a systematic approach to define the scope, objectives, and constraints of the landing zone. This process ensures that the design aligns with business goals and mitigates potential risks.
- Define Business Requirements: This involves understanding the organization’s strategic objectives, application portfolios, and anticipated workloads. Identify key performance indicators (KPIs) and service level agreements (SLAs) that the landing zone must support. Consider the specific needs of different business units and their applications. For instance, a financial services organization might prioritize data residency and stringent compliance requirements, while a media company might focus on content delivery network (CDN) performance and scalability.
- Assess Regulatory and Compliance Needs: Determine the relevant industry regulations (e.g., HIPAA, GDPR, PCI DSS) and internal compliance policies that the landing zone must adhere to. This assessment guides the selection of security controls, data protection mechanisms, and audit logging configurations. For example, organizations handling Protected Health Information (PHI) in the United States must implement specific security measures as Artikeld in the HIPAA Security Rule, including access controls, audit trails, and data encryption.
- Choose a Cloud Provider and Region(s): Select the cloud provider (AWS, Azure, GCP, or a multi-cloud strategy) based on factors like service offerings, pricing, geographic availability, and existing skillsets. Define the geographic regions to be used, considering data residency requirements, latency considerations, and disaster recovery strategies. For instance, a European company subject to GDPR might choose to deploy its landing zone in the European Union to ensure data is stored and processed within the region.
- Develop a Security Strategy: Establish a comprehensive security strategy that encompasses identity and access management (IAM), network security, data protection, and threat detection and response. This strategy should Artikel the security controls, policies, and procedures that will be implemented within the landing zone. It is crucial to align the security strategy with the organization’s overall risk management framework.
- Define Governance Framework: Establish a governance framework that defines roles and responsibilities, policies, and procedures for managing the cloud environment. This framework should address areas like cost management, resource provisioning, change management, and incident response. A well-defined governance framework promotes consistency, accountability, and operational efficiency.
- Create a High-Level Architecture: Develop a high-level architectural design that Artikels the core components of the landing zone, including network infrastructure, identity and access management, security controls, and logging and monitoring systems. This architecture serves as a blueprint for the subsequent detailed design and implementation phases.
Comparison of Cloud Provider Services for Landing Zone Implementation
Cloud providers offer a range of services that can be leveraged to build a secure and compliant landing zone. Understanding the strengths and weaknesses of each provider’s services is crucial for making informed design decisions.
| Feature | AWS | Azure | GCP |
|---|---|---|---|
| Identity and Access Management | AWS IAM, AWS Organizations, AWS SSO | Azure Active Directory (Azure AD), Azure AD B2C, Azure AD B2B | Cloud Identity, Cloud IAM, Cloud Identity-Aware Proxy |
| Network Security | Amazon VPC, AWS Network Firewall, AWS Shield | Azure Virtual Network, Azure Firewall, Azure DDoS Protection | Google Cloud VPC, Cloud Armor, Cloud DDoS Protection |
| Data Protection | AWS KMS, AWS CloudHSM, AWS S3, AWS Glacier | Azure Key Vault, Azure Storage, Azure Information Protection | Cloud KMS, Cloud Storage, Cloud DLP |
| Logging and Monitoring | Amazon CloudWatch, AWS CloudTrail, AWS Config | Azure Monitor, Azure Security Center, Azure Policy | Cloud Monitoring, Cloud Logging, Cloud Audit Logs |
| Governance and Compliance | AWS Control Tower, AWS Config, AWS CloudFormation | Azure Blueprints, Azure Policy, Azure Resource Manager | Cloud Foundation Toolkit, Cloud Asset Inventory, Cloud Resource Manager |
| Key Strengths | Mature services, vast ecosystem, global presence | Strong integration with Microsoft ecosystem, hybrid cloud capabilities, enterprise-grade security | Data analytics and machine learning capabilities, innovative services, competitive pricing |
| Key Weaknesses | Complex service offerings, potential for vendor lock-in, cost management challenges | Steeper learning curve, limited availability in some regions, reliance on Microsoft technologies | Newer services, less mature ecosystem compared to AWS, potential for price fluctuations |
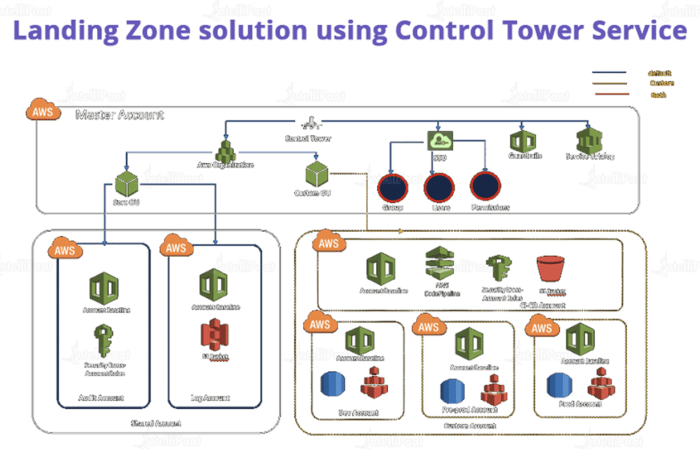
AWS: AWS provides a comprehensive suite of services and a mature ecosystem. AWS Control Tower automates the setup of a multi-account environment, providing a baseline for security and governance. Services like AWS Config enable continuous compliance monitoring. However, the vastness of AWS can lead to complexity, and cost management requires careful planning. For example, a company utilizing AWS might leverage AWS Organizations to manage multiple accounts, apply security policies across all accounts using AWS Config, and use AWS CloudTrail for audit logging.
Azure: Azure excels in hybrid cloud capabilities and integration with the Microsoft ecosystem. Azure Blueprints and Azure Policy facilitate consistent deployment and enforcement of policies. Azure Security Center provides a centralized view of security posture. Azure’s learning curve can be steeper for those unfamiliar with Microsoft technologies. For instance, a company with an existing on-premises Active Directory infrastructure might seamlessly integrate it with Azure Active Directory to manage identities in the cloud.
GCP: GCP is known for its innovative services and strong data analytics and machine learning capabilities. The Cloud Foundation Toolkit provides a framework for building a secure and compliant landing zone. GCP’s pricing can be competitive, but it is important to monitor costs. A company leveraging GCP might utilize Cloud Armor for web application security, Cloud Logging for centralized logging, and Cloud KMS for key management.
Importance of a Well-Defined Organizational Structure within the Landing Zone
A well-defined organizational structure is crucial for managing resources, enforcing security policies, and ensuring accountability within the landing zone. This structure should reflect the organization’s business units, application portfolios, and security requirements.
- Multi-Account Strategy: Implement a multi-account strategy, where each application or business unit operates within its own isolated account. This approach provides logical separation of resources, enhances security by limiting the blast radius of security incidents, and simplifies cost management.
- Organizational Units (OUs): Within a multi-account environment, use organizational units (OUs) to group accounts based on their function or business unit. This allows for applying policies and controls consistently across related accounts. For example, all accounts belonging to the “Finance” department could be grouped under a specific OU.
- Centralized Account Management: Establish a centralized account management strategy for creating, managing, and deleting accounts. This ensures consistency and reduces the risk of misconfigurations. Utilize Infrastructure as Code (IaC) tools to automate account provisioning.
- Role-Based Access Control (RBAC): Implement RBAC to define user roles and assign permissions based on the principle of least privilege. This limits access to only the resources and actions necessary for a user’s job function. Regularly review and update roles and permissions to maintain security.
- Resource Tagging: Utilize resource tagging to categorize and organize resources within the landing zone. Tags enable cost allocation, resource discovery, and automated policy enforcement. For instance, you could tag resources with the application name, cost center, and environment (e.g., “Production,” “Development”).
- Centralized Logging and Monitoring: Implement centralized logging and monitoring to collect and analyze security events and operational metrics across all accounts. This enables proactive threat detection, incident response, and performance optimization. Use security information and event management (SIEM) tools to correlate logs and identify potential security threats.
Example: A company deploying a landing zone on AWS could utilize AWS Organizations to create a multi-account structure. They might establish OUs for different business units (e.g., Marketing, Engineering, Finance) and apply service control policies (SCPs) to restrict actions within each OU. Within each account, they would implement RBAC using AWS IAM, ensuring that users only have the necessary permissions to perform their tasks. Furthermore, they would use AWS CloudTrail to log all API calls and AWS CloudWatch to monitor the health and performance of their resources.
Network Architecture and Security
Implementing a robust network architecture is crucial for establishing a secure and compliant landing zone. This involves meticulous planning and execution, ensuring the confidentiality, integrity, and availability of resources within the cloud environment. A well-designed network architecture acts as the primary line of defense against unauthorized access, data breaches, and service disruptions.
Design of a Secure Network Architecture
The network architecture design must incorporate several key elements to ensure security and operational efficiency. This involves careful consideration of subnets, firewalls, VPNs, and other network components.
- Subnet Design: A well-defined subnet structure is fundamental to network segmentation. Subnets should be organized based on function, sensitivity, and security requirements. For instance, separate subnets can be created for web servers, application servers, and database servers. Each subnet should have its own designated IP address range and should be sized appropriately to accommodate the expected number of resources. The use of private IP address ranges (e.g., 10.0.0.0/8, 172.16.0.0/12, 192.168.0.0/16) is recommended to minimize exposure to the public internet.
- Firewall Configuration: Firewalls act as gatekeepers, controlling network traffic based on predefined rules. They should be deployed at strategic points within the network architecture to inspect and filter traffic. The firewall rules should be based on the principle of least privilege, allowing only necessary traffic and blocking all other traffic by default. For example, a firewall rule might permit HTTP (port 80) and HTTPS (port 443) traffic to a web server subnet while blocking all other incoming traffic.
Regular review and updates of firewall rules are essential to maintain security posture.
- Virtual Private Network (VPN) Implementation: VPNs provide secure connections between the landing zone and other networks, such as on-premises environments or other cloud regions. VPNs encrypt network traffic, protecting it from eavesdropping and unauthorized access. Two main types of VPNs are commonly used: site-to-site VPNs, which connect entire networks, and client-to-site VPNs, which allow individual users to connect securely. VPN configurations should incorporate strong authentication mechanisms and encryption protocols to ensure the confidentiality and integrity of the data transmitted.
- Network Address Translation (NAT): NAT can be used to translate private IP addresses within the landing zone to public IP addresses, enabling outbound internet access for resources within the private subnets. This can enhance security by hiding the internal IP addresses from the public internet. NAT gateways or instances should be configured to manage this translation process efficiently.
- Intrusion Detection and Prevention Systems (IDS/IPS): Integrating IDS/IPS into the network architecture helps detect and prevent malicious activities. These systems monitor network traffic for suspicious patterns and anomalies. Upon detection, they can generate alerts or take automated actions, such as blocking the malicious traffic. IDS/IPS should be deployed strategically to cover critical network segments and protect against various types of attacks.
Process for Implementing Network Segmentation
Network segmentation is a crucial security practice that divides a network into isolated segments. This approach limits the impact of security breaches by preventing attackers from moving laterally across the network. Implementing network segmentation requires a systematic process.
- Identification of Workloads: The first step involves identifying all workloads that will be deployed within the landing zone. Workloads should be categorized based on their function, sensitivity, and compliance requirements. For instance, web applications, databases, and storage services might be considered different workload types.
- Network Segmentation Planning: Based on the identified workloads, a network segmentation plan is developed. This plan defines the subnets, security groups, and access control rules that will be implemented. The plan should consider the principle of least privilege, ensuring that each workload has only the necessary network access.
- Subnet Creation: Create subnets based on the network segmentation plan. Each subnet should be designed to host a specific type of workload or a group of related resources.
- Security Group Configuration: Security groups act as virtual firewalls, controlling inbound and outbound traffic for resources within a subnet. Security groups should be configured to allow only necessary traffic between different subnets and the outside world.
- Network Access Control List (ACL) Implementation: Network ACLs provide an additional layer of security by controlling traffic at the subnet level. ACLs can be used to filter traffic based on source/destination IP addresses, ports, and protocols.
- Testing and Validation: After implementing the network segmentation, rigorous testing and validation are crucial. This involves verifying that the segmentation rules are correctly enforced and that unauthorized traffic is blocked. Penetration testing and vulnerability assessments can be performed to identify any security gaps.
- Monitoring and Maintenance: Continuous monitoring and maintenance are essential to ensure the effectiveness of network segmentation. Network traffic should be monitored for any suspicious activity, and security rules should be reviewed and updated regularly to adapt to evolving threats.
Guide for Configuring Security Groups and Network ACLs
Security groups and network ACLs are fundamental tools for controlling network traffic within a cloud environment. They work together to provide a layered approach to network security. A well-defined configuration is essential to protect the landing zone.
- Security Group Configuration: Security groups are stateful firewalls, meaning they track the state of network connections. When a security group allows inbound traffic, it automatically allows the corresponding outbound traffic.
- Creating Security Groups: Create a security group for each workload or group of related resources. Assign meaningful names to security groups to reflect their purpose (e.g., “web-servers-sg,” “database-servers-sg”).
- Defining Inbound Rules: Define inbound rules to specify the allowed incoming traffic. For example, to allow HTTP traffic to a web server, create a rule that allows traffic on port 80 from the appropriate source IP addresses or security groups.
- Defining Outbound Rules: Define outbound rules to specify the allowed outgoing traffic. By default, security groups typically allow all outbound traffic. However, it’s good practice to restrict outbound traffic to only necessary destinations.
- Network ACL Configuration: Network ACLs are stateless firewalls, meaning they do not track the state of network connections. They evaluate traffic based on source/destination IP addresses, ports, and protocols.
- Creating Network ACLs: Create a network ACL for each subnet. By default, network ACLs typically allow all inbound and outbound traffic.
- Defining Rules: Define rules to control traffic entering and leaving the subnet. ACL rules are evaluated in order, so the order of rules matters. It is recommended to use the “deny all” rule at the end of the list as the default.
- Rule Priorities: ACL rules have priorities, and the rule with the lowest number is evaluated first. For example, a rule allowing SSH traffic (port 22) might have a higher priority than a rule denying all traffic.
- Testing and Verification: After configuring security groups and network ACLs, test the configurations to verify that traffic is being allowed or blocked as expected. Use network diagnostic tools, such as `ping` and `traceroute`, to troubleshoot any connectivity issues.
Identity and Access Management (IAM)
Effective Identity and Access Management (IAM) is crucial for securing a landing zone. It governs user authentication, authorization, and access control, minimizing the attack surface and ensuring only authorized individuals and systems can interact with resources. A robust IAM strategy protects sensitive data and workloads, meeting compliance requirements and preventing unauthorized access that could lead to data breaches or service disruptions.
IAM Best Practices for User Access Management
Implementing IAM best practices ensures secure and efficient user access management within the landing zone. These practices are designed to minimize risk, improve operational efficiency, and maintain compliance with industry standards.
- Principle of Least Privilege: Grant users only the minimum necessary permissions to perform their required tasks. Regularly review and adjust permissions as job roles and responsibilities evolve. For example, a developer should not have administrative access to production systems unless absolutely necessary.
- Strong Authentication: Enforce the use of strong passwords and multi-factor authentication (MFA) to verify user identities. Regularly update password policies and monitor for compromised credentials. Consider integrating with identity providers (IdPs) for centralized authentication.
- Role-Based Access Control (RBAC): Define roles based on job functions and assign users to these roles. This simplifies access management and ensures consistency. For instance, a ‘database administrator’ role would have specific permissions to manage database instances, while a ‘network administrator’ role would have different permissions related to network configurations.
- Regular Access Reviews: Conduct periodic reviews of user access rights to ensure they remain appropriate. This helps identify and remediate any excessive or inappropriate permissions. These reviews should involve both automated tools and manual verification processes.
- Automated Provisioning and Deprovisioning: Automate the process of creating, modifying, and deleting user accounts and access rights. This reduces manual errors and ensures timely access changes based on employee onboarding, transfers, and terminations. Utilize tools that integrate with HR systems for automated workflows.
- Monitoring and Auditing: Implement comprehensive monitoring and auditing of user access and activities. Log all access attempts, successful logins, and permission changes. Analyze these logs for suspicious activity and security incidents.
Implementing Multi-Factor Authentication (MFA)
Multi-factor authentication (MFA) significantly enhances security by requiring users to provide multiple verification factors before granting access. This adds an extra layer of protection against unauthorized access, even if a user’s password is compromised. The following steps detail the implementation of MFA within the landing zone.
- Choose an MFA Solution: Select an MFA solution that integrates with the chosen cloud provider or identity provider. Popular options include hardware tokens, software-based authenticator apps (like Google Authenticator or Microsoft Authenticator), and biometric authentication. Evaluate factors like cost, ease of use, and compatibility with existing infrastructure.
- Enable MFA for All Users: Enforce MFA for all user accounts, especially those with privileged access. This should be a mandatory requirement, not an optional setting. Implement MFA for administrative accounts first, as these accounts have the highest risk profile.
- Configure MFA Methods: Configure the MFA methods that users will use. This may include setting up authenticator apps on mobile devices, registering security keys, or configuring email or SMS-based verification. Provide clear instructions and support for users to set up their MFA methods.
- Test MFA Implementation: Thoroughly test the MFA implementation to ensure it functions correctly. Verify that users can successfully log in using MFA and that the system denies access if MFA fails. Test various scenarios, including lost devices or incorrect codes.
- Monitor MFA Usage: Monitor MFA usage to identify any issues or anomalies. Review logs to track the number of successful and failed MFA attempts. Investigate any suspicious activity, such as repeated MFA failures from the same IP address.
- Provide User Training: Educate users on how to use MFA and the importance of protecting their authentication methods. Provide clear guidelines on what to do if they lose their device or suspect their account has been compromised. Offer ongoing training and support to address user questions and concerns.
Setting Up Role-Based Access Control (RBAC)
Role-Based Access Control (RBAC) simplifies access management by assigning permissions based on job roles. This approach ensures consistency, reduces the risk of human error, and simplifies auditing. Implementing RBAC involves defining roles, assigning permissions to those roles, and assigning users to the appropriate roles.
- Identify Roles: Analyze the organization’s structure and identify the distinct roles required within the landing zone. Roles should reflect job functions and responsibilities. Examples include:
- Administrator: Full access to all resources and services.
- Developer: Access to development environments, code repositories, and deployment tools.
- Security Analyst: Access to security tools, logs, and monitoring systems.
- Network Engineer: Access to network configuration and management tools.
- Define Permissions: Determine the specific permissions required for each role. This includes the actions that users in that role can perform (e.g., create, read, update, delete) on specific resources (e.g., virtual machines, databases, storage buckets). Document these permissions clearly.
- Create Roles in the IAM System: Create the defined roles within the chosen IAM system (e.g., AWS IAM, Azure Active Directory, Google Cloud IAM). Assign the appropriate permissions to each role. Use a principle of least privilege when assigning permissions.
- Assign Users to Roles: Assign users to the appropriate roles based on their job functions. Ensure that users are only assigned to the roles that they need to perform their tasks. Regularly review role assignments to ensure they remain accurate and up-to-date.
- Test RBAC Implementation: Test the RBAC implementation to verify that users have the correct access and that they cannot access resources they are not authorized to use. Conduct user acceptance testing (UAT) to validate the implementation.
- Monitor and Audit RBAC: Monitor the RBAC implementation to ensure that it is functioning correctly and that access controls are being enforced. Regularly audit user access and permissions to identify any anomalies or potential security risks.
Data Protection and Encryption
Data protection and encryption are fundamental pillars of a secure and compliant landing zone. They safeguard sensitive information from unauthorized access, modification, or disclosure, ensuring data integrity and confidentiality. Implementing robust data protection measures is crucial for meeting regulatory requirements and maintaining trust with users and stakeholders.
Encryption Methods for Data Protection
Encryption methods are essential for securing data at rest and in transit. These methods transform data into an unreadable format, requiring a decryption key for access. The choice of encryption method depends on the specific security requirements and the environment in which the data resides.
- Data at Rest Encryption: This protects data stored on physical or virtual devices. Several methods are available:
- Symmetric Encryption: Uses the same key for both encryption and decryption. It is generally faster than asymmetric encryption but requires secure key management. Examples include Advanced Encryption Standard (AES) and Triple DES (3DES). AES is widely used due to its efficiency and strong security.
For instance, an organization might use AES-256 to encrypt sensitive customer data stored on hard drives within their landing zone, protecting it from unauthorized access if the drives are physically stolen.
- Asymmetric Encryption: Uses a pair of keys: a public key for encryption and a private key for decryption. Public keys can be shared, while private keys must be kept secret. Examples include Rivest-Shamir-Adleman (RSA) and Elliptic-Curve Cryptography (ECC). RSA is commonly used for digital signatures and key exchange.
- Database Encryption: Encrypts data within a database system. This can be implemented at the column level, table level, or database level. Database encryption protects against unauthorized access to the database itself.
- File-Level Encryption: Encrypts individual files or directories. This can be useful for securing specific sensitive documents or data sets.
- Symmetric Encryption: Uses the same key for both encryption and decryption. It is generally faster than asymmetric encryption but requires secure key management. Examples include Advanced Encryption Standard (AES) and Triple DES (3DES). AES is widely used due to its efficiency and strong security.
- Data in Transit Encryption: Protects data as it travels between systems or networks. Several methods are available:
- Transport Layer Security (TLS)/Secure Sockets Layer (SSL): Provides secure communication channels over the internet. TLS/SSL encrypts data exchanged between a client and a server, ensuring confidentiality and integrity. This is crucial for protecting data transmitted over public networks. For example, when users access a web application within the landing zone, TLS/SSL encrypts the communication between the user’s browser and the web server, protecting sensitive data like login credentials and personal information.
- Virtual Private Network (VPN): Creates a secure, encrypted connection over a public network. VPNs are commonly used to secure remote access to resources within the landing zone. Employees can securely connect to the landing zone network from remote locations using a VPN, ensuring that all data transmitted between their devices and the landing zone is encrypted.
- IPsec: A suite of protocols used to secure IP communications. IPsec can be used to encrypt traffic between network devices, such as routers and firewalls.
Implementing Data Loss Prevention (DLP) Strategies
Data Loss Prevention (DLP) strategies are designed to prevent sensitive data from leaving the organization’s control. These strategies involve identifying, monitoring, and preventing data breaches, either accidental or malicious.
- Data Identification and Classification: The first step is to identify and classify sensitive data. This involves determining the types of data that need protection (e.g., Personally Identifiable Information (PII), financial data, intellectual property). Data can be classified based on sensitivity levels (e.g., public, internal, confidential, restricted). This can be done manually or through automated tools that scan data and apply tags based on content or metadata.
- Policy Definition and Enforcement: Develop and enforce policies that govern how sensitive data is handled. These policies should define rules for data storage, access, and transmission. Examples of policies include:
- Data Storage Policies: Define where data can be stored (e.g., approved storage locations within the landing zone) and how it should be encrypted.
- Access Control Policies: Specify who can access sensitive data and under what circumstances. Implement role-based access control (RBAC) and least privilege principles.
- Data Transmission Policies: Define how data can be transmitted (e.g., using encrypted channels like TLS/SSL or VPN) and what data can be sent outside the organization.
- Monitoring and Alerting: Implement monitoring tools to track data movement and detect potential data breaches. These tools can generate alerts when policy violations occur. For example, if an employee attempts to upload a file containing sensitive data to a public cloud storage service, a DLP system would detect this and generate an alert.
- Incident Response: Establish a clear incident response plan to address data breaches. This plan should include steps for containing the breach, investigating the cause, notifying affected parties, and taking corrective actions.
- DLP Tools: Utilize DLP tools that can scan data at rest, in use, and in motion. These tools can identify sensitive data, enforce policies, and prevent data loss. Common features include content inspection, data discovery, and data encryption.
Automated Data Backup and Recovery Solutions
Automated data backup and recovery solutions are essential for ensuring data availability and business continuity. These solutions create regular backups of data and provide a mechanism for restoring data in case of data loss or system failure.
- Backup Strategies: Define a backup strategy that aligns with the organization’s recovery time objective (RTO) and recovery point objective (RPO).
- Full Backups: Copy all data at a specific point in time. This provides the most complete backup but can be time-consuming.
- Incremental Backups: Back up only the data that has changed since the last backup (full or incremental). This is faster than full backups but requires restoring a chain of backups.
- Differential Backups: Back up only the data that has changed since the last full backup. This is faster than full backups but slower than incremental backups.
- Backup Location: Choose appropriate backup locations.
- On-Premises Backup: Back up data to local storage devices within the landing zone. This provides fast recovery but may be vulnerable to local disasters.
- Offsite Backup: Back up data to a remote location, such as a cloud storage service. This provides protection against local disasters but may have slower recovery times.
- Hybrid Backup: Combines on-premises and offsite backups. This provides a balance of speed and protection.
- Backup Automation: Automate the backup process to ensure that backups are performed regularly and consistently. This can be achieved using backup software or cloud-based backup services. For example, a scheduled backup job could be configured to automatically back up critical databases and virtual machines within the landing zone every night.
- Data Recovery Testing: Regularly test the data recovery process to ensure that backups are working correctly and that data can be restored successfully. This involves simulating a data loss scenario and verifying that data can be recovered within the RTO.
- Disaster Recovery Planning: Develop a disaster recovery plan that Artikels the steps to be taken in the event of a major outage or disaster. This plan should include procedures for restoring data, recovering systems, and resuming business operations.
- Encryption of Backups: Encrypt backup data to protect it from unauthorized access. This is particularly important if backups are stored offsite or in the cloud.
Logging, Monitoring, and Auditing
A robust logging, monitoring, and auditing strategy is crucial for maintaining the security posture and compliance of a landing zone. It provides the necessary visibility to detect and respond to security incidents, track system performance, and demonstrate adherence to regulatory requirements. This section details the design and implementation of such a strategy.
Designing a Comprehensive Logging and Monitoring Strategy
A well-designed logging and monitoring strategy requires careful consideration of data sources, storage, analysis, and alerting mechanisms. It aims to capture relevant events, analyze them for anomalies, and provide timely notifications of critical issues.
- Data Sources: Identify all relevant data sources within the landing zone. These include:
- Virtual Machine (VM) operating system logs (e.g., Windows Event Logs, Linux system logs).
- Network device logs (e.g., firewall, intrusion detection/prevention systems (IDS/IPS), routers).
- Application logs (e.g., web servers, database servers, custom applications).
- Identity and Access Management (IAM) logs (e.g., authentication attempts, permission changes).
- Security Information and Event Management (SIEM) system logs.
- Cloud provider audit logs (e.g., AWS CloudTrail, Azure Activity Log, Google Cloud Audit Logs).
- Log Aggregation and Storage: Establish a centralized log aggregation and storage solution. This facilitates efficient analysis and long-term retention.
- Choose a scalable and secure log management system (e.g., Splunk, ELK Stack (Elasticsearch, Logstash, Kibana), Azure Sentinel, AWS CloudWatch Logs).
- Implement data retention policies based on compliance requirements and business needs. Consider tiered storage solutions for cost optimization (e.g., short-term storage for real-time analysis, long-term archival storage).
- Ensure log data is encrypted both in transit and at rest to protect confidentiality.
- Log Analysis and Correlation: Implement methods for analyzing and correlating log data to identify security threats and operational issues.
- Define specific search queries, filters, and dashboards to monitor key metrics and events.
- Use security analytics and threat intelligence feeds to identify malicious activity patterns.
- Employ machine learning (ML) and artificial intelligence (AI) for anomaly detection and predictive analysis.
- Monitoring and Alerting: Configure proactive monitoring and alerting based on the analysis of log data.
- Define thresholds and alert rules for critical events, such as failed login attempts, unauthorized access, and suspicious network traffic.
- Configure alerts to be sent to relevant stakeholders (e.g., security operations center (SOC), system administrators) via email, SMS, or other notification channels.
- Establish escalation procedures to ensure timely response to security incidents.
Creating a System for Alerting on Security Events and Anomalies
Effective alerting is critical for a timely response to security threats. The system should be designed to identify and notify the appropriate personnel of any security incidents or anomalies.
- Event Detection and Rule Creation: Define specific rules and thresholds for identifying security events and anomalies.
- Use SIEM or log management tools to create rules based on various event types (e.g., failed login attempts, unauthorized access attempts, suspicious network traffic).
- Leverage threat intelligence feeds to identify known malicious indicators of compromise (IOCs).
- Monitor system performance metrics to detect unusual activity.
- Alerting Mechanisms: Implement multiple alerting mechanisms to ensure timely notification.
- Configure alerts to be sent to relevant personnel via email, SMS, or other notification channels.
- Integrate alerts with incident management systems to facilitate incident response.
- Use dashboards and real-time visualizations to monitor security events and anomalies.
- Alert Prioritization and Escalation: Prioritize alerts based on severity and impact.
- Define alert severity levels (e.g., critical, high, medium, low) based on the potential impact of the event.
- Establish escalation procedures to ensure that critical alerts are addressed promptly.
- Implement a process for false positive identification and remediation.
- Automation: Automate alert responses where possible.
- Use security orchestration, automation, and response (SOAR) tools to automate tasks such as incident triage, containment, and remediation.
- Integrate alerting with security tools (e.g., firewalls, IDS/IPS) to automatically block malicious activity.
Organizing the Steps for Implementing Regular Security Audits and Compliance Checks
Regular security audits and compliance checks are essential to ensure the landing zone meets security standards and regulatory requirements. This involves establishing a schedule, defining scope, and conducting assessments.
- Audit Planning and Scope Definition: Define the scope and objectives of the security audits and compliance checks.
- Identify the applicable compliance frameworks (e.g., PCI DSS, HIPAA, GDPR).
- Define the scope of the audit, including the systems, applications, and data that will be assessed.
- Establish a schedule for regular audits and compliance checks (e.g., quarterly, annually).
- Audit Execution: Conduct the security audits and compliance checks according to the defined scope.
- Use automated tools and manual assessments to evaluate the security controls in place.
- Review log data, configuration settings, and security policies.
- Conduct vulnerability scans and penetration tests to identify security vulnerabilities.
- Reporting and Remediation: Generate reports and address any identified findings.
- Document the audit findings, including any vulnerabilities, weaknesses, and non-compliance issues.
- Prioritize the remediation of findings based on their severity and impact.
- Track the progress of remediation efforts.
- Continuous Improvement: Continuously improve the security posture of the landing zone based on the results of audits and compliance checks.
- Update security policies and procedures based on the audit findings.
- Implement new security controls to address identified vulnerabilities.
- Regularly review and update the audit and compliance program.
Automation and Infrastructure as Code (IaC)
Implementing Automation and Infrastructure as Code (IaC) is crucial for efficiently deploying, managing, and maintaining a secure and compliant landing zone. IaC allows organizations to define their infrastructure in code, automating the provisioning and configuration of resources, thereby reducing manual errors, increasing consistency, and accelerating deployment cycles. This approach promotes repeatability and enables version control, facilitating easier management of infrastructure changes and audits.
Benefits of IaC for Landing Zone Deployment and Management
Employing IaC offers numerous advantages in the context of a landing zone. These benefits contribute to improved security, efficiency, and overall manageability.
- Increased Consistency and Reduced Errors: IaC ensures that infrastructure is deployed consistently across environments. Since the infrastructure is defined as code, it eliminates the potential for human error that can occur during manual configuration. This reduces the risk of misconfigurations that could lead to security vulnerabilities or compliance violations.
- Faster Deployment and Scalability: IaC automates the infrastructure provisioning process. This allows for faster deployments, as resources can be created and configured automatically. Furthermore, IaC facilitates scalability by enabling the easy replication of infrastructure components as needed to meet changing demands.
- Improved Version Control and Rollback Capabilities: IaC allows for version control of infrastructure configurations, using tools like Git. This enables tracking of changes, facilitates rollbacks to previous states in case of issues, and provides a clear audit trail of infrastructure modifications.
- Enhanced Security and Compliance: IaC allows security best practices and compliance requirements to be codified directly into the infrastructure definition. This ensures that security configurations are consistently applied and helps to meet compliance mandates. Furthermore, IaC enables the automated enforcement of security policies and the detection of configuration drifts.
- Cost Optimization: By automating the provisioning and de-provisioning of resources, IaC helps optimize resource utilization. This can lead to cost savings by eliminating the need for manual resource management and by ensuring that resources are only provisioned when needed.
Examples of IaC Tools and Their Application
Several IaC tools are available, each with its strengths and specific use cases. Understanding these tools and their application is essential for effective landing zone implementation.
- Terraform: Terraform is a popular open-source IaC tool that supports multiple cloud providers. It uses a declarative configuration language to define infrastructure as code. Terraform is widely used for creating and managing infrastructure across various platforms, including AWS, Azure, and Google Cloud Platform. For example, a Terraform configuration might define the creation of a virtual private cloud (VPC), subnets, security groups, and instances, all managed through a single configuration file.
- AWS CloudFormation: AWS CloudFormation is a service provided by Amazon Web Services (AWS) that enables the modeling and setup of AWS resources. CloudFormation uses templates written in YAML or JSON to define infrastructure. CloudFormation is tightly integrated with AWS services, making it easy to provision and manage resources within the AWS ecosystem. A CloudFormation template could be used to create an entire landing zone, including the network configuration, identity and access management (IAM) roles, and security controls.
- Azure Resource Manager (ARM) Templates: Azure Resource Manager (ARM) templates are the IaC solution for Microsoft Azure. ARM templates use JSON or Bicep (a declarative language) to define infrastructure resources. ARM templates are used to deploy and manage resources such as virtual machines, storage accounts, and networking components within Azure. An ARM template could define the creation of a virtual network, subnets, and security groups, along with the necessary access control policies.
- Google Cloud Deployment Manager: Google Cloud Deployment Manager is Google Cloud’s IaC tool, enabling the definition and deployment of infrastructure using YAML or Python templates. Deployment Manager supports a wide range of Google Cloud services and is well-suited for managing complex deployments. A Deployment Manager configuration could be used to provision a landing zone including networking, compute, and storage resources, as well as managing IAM policies.
Script to Automate the Creation of a Basic Landing Zone Environment
The following example script (using Terraform) provides a simplified illustration of automating a basic landing zone setup. This script focuses on creating a VPC, a subnet, and an internet gateway. Note: This is a simplified example and does not include all necessary security and compliance configurations for a production environment.
# terraform.tfterraform required_providers aws = source = "hashicorp/aws" version = "~> 5.0" # Configure the AWS Providerprovider "aws" region = "us-east-1" # Replace with your desired region# Create a VPCresource "aws_vpc" "main" cidr_block = "10.0.0.0/16" tags = Name = "LandingZone-VPC" # Create a public subnetresource "aws_subnet" "public" vpc_id = aws_vpc.main.id cidr_block = "10.0.1.0/24" availability_zone = "us-east-1a" # Replace with your desired AZ tags = Name = "LandingZone-Public-Subnet" # Create an internet gatewayresource "aws_internet_gateway" "gw" vpc_id = aws_vpc.main.id tags = Name = "LandingZone-InternetGateway" # Create a route table for the public subnetresource "aws_route_table" "public" vpc_id = aws_vpc.main.id route cidr_block = "0.0.0.0/0" gateway_id = aws_internet_gateway.gw.id tags = Name = "LandingZone-Public-RouteTable" # Associate the route table with the public subnetresource "aws_route_table_association" "public" subnet_id = aws_subnet.public.id route_table_id = aws_route_table.public.id
This script demonstrates the basic principles of IaC.
To use this script:
- Install Terraform on your local machine.
- Configure your AWS credentials.
- Save the script as `terraform.tf`.
- Run `terraform init` to initialize the Terraform configuration.
- Run `terraform plan` to preview the changes.
- Run `terraform apply` to create the resources.
This example shows how to automate the creation of fundamental network infrastructure. Real-world implementations will include additional resources such as IAM roles, security groups, and other configurations, all defined within the IaC code. Furthermore, best practices include the use of modules to encapsulate reusable components and the implementation of version control to track changes and manage infrastructure deployments effectively.
Compliance Frameworks and Regulations
Implementing a secure and compliant landing zone is fundamentally about aligning technical infrastructure with the mandates of various regulatory frameworks. These frameworks dictate specific security controls and practices to protect sensitive data, ensuring confidentiality, integrity, and availability. Adhering to these regulations is not merely a technical exercise; it is a critical business requirement that mitigates legal, financial, and reputational risks.
Understanding the nuances of each framework and how they interrelate is crucial for effective landing zone design.
Common Compliance Frameworks and Their Impact
Several compliance frameworks are prevalent in modern IT environments, each with a distinct scope and set of requirements. Failure to comply with these frameworks can result in significant penalties, including hefty fines, legal action, and damage to brand reputation.
- Payment Card Industry Data Security Standard (PCI DSS): PCI DSS applies to any organization that stores, processes, or transmits cardholder data. Its primary focus is on securing cardholder data to prevent credit card fraud. The impact of PCI DSS is substantial for businesses handling payment card transactions. Compliance requires rigorous security measures, including network segmentation, encryption of cardholder data, access control, and regular security assessments. Non-compliance can lead to fines, loss of processing privileges, and damage to customer trust.
For example, a merchant found to be non-compliant with PCI DSS might face penalties ranging from $5,000 to $100,000 per month, depending on the severity of the violation and the number of affected cardholders.
- Health Insurance Portability and Accountability Act (HIPAA): HIPAA regulates the protection of Protected Health Information (PHI) in the healthcare industry. It mandates the safeguarding of electronic PHI from unauthorized access, use, or disclosure. The impact of HIPAA compliance extends to healthcare providers, health plans, and their business associates. Requirements include implementing administrative, physical, and technical safeguards, such as access controls, audit trails, and data encryption. Non-compliance can result in significant financial penalties, ranging from $100 to $50,000 per violation, and can lead to criminal charges in severe cases.
- General Data Protection Regulation (GDPR): GDPR is a comprehensive data privacy regulation that applies to organizations processing the personal data of individuals within the European Union (EU), regardless of the organization’s location. GDPR’s impact is global, as it affects any organization that interacts with EU citizens’ data. Compliance necessitates obtaining explicit consent for data processing, providing individuals with rights to access and control their data, and implementing robust security measures to protect data from breaches.
Penalties for non-compliance can reach up to 4% of a company’s global annual turnover or €20 million, whichever is higher.
- Federal Information Security Management Act (FISMA): FISMA is a U.S. federal law that mandates security requirements for information systems used by federal agencies and those that support them. Its impact lies in ensuring the confidentiality, integrity, and availability of federal information and systems. Compliance involves establishing security programs, conducting risk assessments, implementing security controls, and regularly monitoring and evaluating the effectiveness of these controls. Non-compliance can lead to sanctions, including funding restrictions and potential legal action.
Comparison of Compliance Framework Requirements
While each compliance framework has unique requirements, they share common goals: protecting sensitive data and ensuring its confidentiality, integrity, and availability. However, the specific controls and the level of detail required vary considerably.
A comparative table highlights key differences:
| Framework | Scope | Data Focus | Key Requirements | Geographic Focus |
|---|---|---|---|---|
| PCI DSS | Organizations handling cardholder data | Cardholder data (PAN, cardholder name, expiration date, etc.) | Network segmentation, encryption, access control, vulnerability management | Global |
| HIPAA | Healthcare providers, health plans, business associates | Protected Health Information (PHI) | Administrative, physical, and technical safeguards; access controls; audit trails; data encryption | United States |
| GDPR | Organizations processing personal data of EU residents | Personal data (name, address, email, IP address, etc.) | Consent, data subject rights, data minimization, data breach notification | European Union |
| FISMA | U.S. federal agencies and their contractors | Federal information | Security program, risk assessments, security controls, continuous monitoring | United States |
The table demonstrates that while PCI DSS is concerned with securing cardholder data, HIPAA focuses on protecting PHI, and GDPR emphasizes the protection of personal data. FISMA provides a comprehensive framework for securing federal information and systems. The geographic scope also varies, with GDPR having a global reach and HIPAA primarily impacting the United States.
Mapping Landing Zone Security Controls to Compliance Requirements
Designing a landing zone with compliance in mind requires a systematic approach to mapping security controls to the requirements of relevant frameworks. This process ensures that the implemented security measures directly address the regulatory mandates.
The mapping process typically involves the following steps:
- Identify Applicable Frameworks: Determine which compliance frameworks apply based on the organization’s business activities, data types handled, and geographic locations. For instance, a healthcare provider in the United States would likely need to comply with HIPAA.
- Understand Framework Requirements: Thoroughly review the requirements of each identified framework. This includes understanding the specific security controls, policies, and procedures mandated.
- Assess Existing Security Controls: Evaluate the existing security controls implemented in the landing zone. This involves identifying the current security posture and determining how well it aligns with the framework requirements.
- Map Controls to Requirements: Create a mapping matrix or table that links the landing zone’s security controls to the specific requirements of each compliance framework. This helps visualize the coverage and identify any gaps.
- Address Gaps: Identify any gaps in security controls where the landing zone does not meet the framework requirements. Develop a remediation plan to address these gaps. This may involve implementing new controls, modifying existing ones, or updating policies and procedures.
- Document and Maintain: Document the mapping process, including the mapping matrix, remediation plans, and any changes made to the landing zone. Regularly review and update the mapping as compliance requirements evolve and the landing zone infrastructure changes.
Example:
Consider a landing zone designed to process credit card transactions. The organization must comply with PCI DSS. A mapping exercise would identify the following:
- PCI DSS Requirement: Protect stored cardholder data.
- Landing Zone Security Control: Encrypt all cardholder data at rest using AES-256 encryption.
- Mapping: The encryption control directly addresses the PCI DSS requirement to protect stored cardholder data.
This example illustrates how a specific security control within the landing zone directly supports a compliance requirement. By systematically mapping controls to requirements, organizations can ensure that their landing zone is designed and operated in a compliant manner, minimizing risks and fostering trust.
Disaster Recovery and Business Continuity
Implementing robust disaster recovery (DR) and business continuity (BC) strategies is crucial for a secure and compliant landing zone. These strategies ensure minimal downtime and data loss in the event of a disruptive event, safeguarding business operations and maintaining regulatory compliance. Effective DR and BC planning involves proactive measures to prevent disruptions and reactive measures to restore services swiftly.
Design a Disaster Recovery Plan for the Landing Zone
A comprehensive disaster recovery plan for a landing zone requires careful consideration of potential threats, recovery objectives, and the resources needed to achieve them. This plan should be a living document, regularly updated and tested to ensure its effectiveness.The DR plan should encompass the following key elements:
- Risk Assessment: Identifying potential threats, such as natural disasters, cyberattacks, and human error, and assessing their likelihood and impact. For instance, a financial institution might prioritize protection against ransomware attacks, which have become increasingly prevalent.
- Recovery Objectives: Defining Recovery Point Objectives (RPOs) and Recovery Time Objectives (RTOs) for critical systems and data. These objectives determine the acceptable data loss (RPO) and the maximum downtime (RTO) that the business can tolerate.
- Recovery Strategies: Selecting appropriate recovery strategies based on the RPOs and RTOs. Common strategies include:
- Backup and Restore: Regularly backing up data and applications to a separate location, enabling restoration in case of a failure. This is often the most cost-effective approach for less critical systems.
- Pilot Light: Maintaining a minimal version of the production environment in a secondary location, ready to be scaled up in case of a disaster.
- Warm Standby: Maintaining a fully operational, but scaled-down, version of the production environment in a secondary location, ready to take over quickly.
- Hot Standby: Maintaining a fully operational, identical copy of the production environment in a secondary location, ensuring minimal downtime.
- Infrastructure and Technology: Specifying the infrastructure and technologies needed for recovery, including compute, storage, networking, and software. This might involve using cloud-based services for their inherent resilience and scalability.
- Processes and Procedures: Documenting detailed steps for initiating the recovery process, including roles and responsibilities, communication protocols, and escalation procedures.
- Testing and Validation: Regularly testing the DR plan through simulated disaster scenarios to validate its effectiveness and identify areas for improvement. Testing frequency should be aligned with the criticality of the systems.
Elaborate on the Steps for Implementing a Business Continuity Strategy
Implementing a business continuity (BC) strategy builds upon the DR plan, extending its scope to address broader operational disruptions. The BC strategy aims to ensure that critical business functions can continue operating, even during a prolonged outage.The implementation steps involve:
- Business Impact Analysis (BIA): Identifying critical business functions, their dependencies, and the impact of their disruption. This analysis helps prioritize recovery efforts. A BIA might reveal that order processing and customer support are critical functions for an e-commerce business.
- BC Plan Development: Creating a detailed BC plan that Artikels the actions required to maintain or restore critical business functions during a disruption. This plan should include:
- Crisis Management: Establishing a crisis management team and defining procedures for managing the response to a disruptive event.
- Communication Plan: Defining communication protocols to keep stakeholders informed during a crisis.
- Alternate Workspaces: Identifying alternative workspaces and resources for employees to continue working.
- Data Recovery: Ensuring the availability of critical data and applications.
- Implementation and Training: Implementing the BC plan, including acquiring necessary resources and training employees on their roles and responsibilities. Regular training and awareness programs are essential.
- Testing and Maintenance: Regularly testing and updating the BC plan to ensure its effectiveness and relevance. This involves conducting drills and simulations to validate the plan’s procedures.
Recovery Point Objectives (RPOs) and Recovery Time Objectives (RTOs) for Various Scenarios
Defining RPOs and RTOs is essential for tailoring disaster recovery strategies to the specific needs of a landing zone’s applications and data. The following table illustrates different scenarios with corresponding RPOs and RTOs:
| Scenario | Application/Data | RPO (Maximum Data Loss) | RTO (Maximum Downtime) |
|---|---|---|---|
| Critical Financial Transactions | Core Banking System | Near Real-time (seconds to minutes) | Minutes to Hours |
| Customer Relationship Management (CRM) | Customer Data and Interactions | Hours | Hours |
| Reporting and Analytics | Historical Data | Days | Days |
| Development and Testing Environments | Development Code and Test Data | Days | Days |
In the context of financial transactions, where the integrity of data is paramount, an RPO measured in seconds or minutes is crucial. For reporting and analytics, where historical data is less volatile, a less stringent RPO is acceptable. The chosen RPOs and RTOs will directly influence the choice of recovery strategy and the associated costs.
Ending Remarks
In conclusion, designing a secure and compliant landing zone is not a one-time project but an ongoing process of planning, implementation, and refinement. By adhering to the principles Artikeld in this guide, organizations can establish a resilient and compliant cloud foundation. Regular audits, continuous monitoring, and proactive security measures are essential to maintain a strong security posture and adapt to evolving threats and regulatory landscapes.
The successful implementation of a well-designed landing zone provides a secure, scalable, and compliant environment for cloud-based operations, enabling organizations to leverage the full potential of cloud computing while mitigating associated risks.
Answers to Common Questions
What is the primary benefit of using Infrastructure as Code (IaC) for a landing zone?
IaC enables automated, consistent, and repeatable deployments, reducing manual errors and accelerating the setup and maintenance of the landing zone.
How does a landing zone improve an organization’s security posture?
A landing zone provides a centralized and controlled environment for security configurations, enforcing consistent security policies, and facilitating the implementation of security best practices across all cloud resources.
What are the key differences between a landing zone and a cloud environment?
A landing zone is a pre-configured, secure, and compliant foundation for a cloud environment, while a cloud environment is the broader infrastructure where applications and services are deployed. The landing zone provides the necessary security controls and governance to ensure the environment operates securely and in compliance with regulations.
How often should security audits be performed on a landing zone?
Regular security audits should be conducted, ideally at least annually, or more frequently if there are significant changes to the environment, compliance requirements, or security threats.
What is the role of network segmentation in a secure landing zone?
Network segmentation isolates workloads, limiting the impact of security breaches and enabling granular control over network traffic, improving security posture.