Navigating the complex landscape of cybersecurity can be daunting, but understanding how to meet NIST cybersecurity framework guidelines provides a robust roadmap for organizations of all sizes. This framework, developed by the National Institute of Standards and Technology (NIST), offers a flexible and adaptable approach to managing cybersecurity risks, ensuring that critical assets are protected and that organizations can respond effectively to threats.
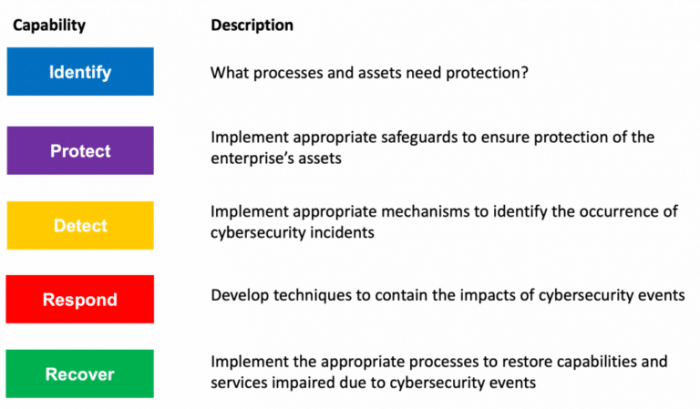
This guide will delve into the core functions of the NIST Cybersecurity Framework: Identify, Protect, Detect, Respond, and Recover. We’ll explore practical steps for implementing these functions, from identifying and assessing risks to implementing security controls, detecting incidents, and planning for recovery. By following this comprehensive approach, organizations can significantly enhance their cybersecurity posture and resilience.
Understanding the NIST Cybersecurity Framework

The NIST Cybersecurity Framework (CSF) provides a flexible, risk-based approach to managing cybersecurity risk. It’s a widely adopted framework designed to help organizations understand, manage, and reduce their cybersecurity risk. This framework is not a one-size-fits-all solution, but rather a set of guidelines that can be tailored to fit the specific needs of an organization, regardless of its size or industry.
The Five Core Functions of the NIST Cybersecurity Framework
The NIST CSF is organized around five core functions: Identify, Protect, Detect, Respond, and Recover. These functions provide a high-level, strategic view of cybersecurity risk management and are interconnected. Successful implementation of the framework requires addressing all five functions in a continuous cycle of improvement.
- Identify: This function focuses on developing an organizational understanding of cybersecurity risk. It involves identifying assets, data, systems, and capabilities that need protection.
- Asset Management: Inventorying and categorizing all organizational assets, including hardware, software, and data. For example, a hospital would identify its patient records database, medical devices, and network infrastructure.
- Business Environment: Understanding the organization’s mission, objectives, and stakeholders. This includes identifying legal and regulatory requirements relevant to cybersecurity. A financial institution, for example, must comply with regulations like PCI DSS.
- Governance: Establishing policies, procedures, and roles to manage and support cybersecurity risk. This involves defining responsibilities and accountability.
- Risk Assessment: Identifying and analyzing cybersecurity threats and vulnerabilities to assess the likelihood and impact of potential incidents. A manufacturing company might assess the risk of a ransomware attack disrupting its production line.
- Risk Management Strategy: Developing a strategy to manage cybersecurity risk, including risk tolerance and acceptance criteria.
- Protect: This function Artikels the safeguards necessary to ensure the delivery of critical infrastructure services. It involves implementing appropriate security measures to limit or contain the impact of a potential cybersecurity event.
- Access Control: Implementing measures to restrict access to systems and data based on the principle of least privilege. For example, using multi-factor authentication for sensitive systems.
- Awareness and Training: Providing cybersecurity awareness training to employees to educate them about threats and best practices. Regular phishing simulations can be a part of this.
- Data Security: Protecting data throughout its lifecycle, including encryption, data loss prevention (DLP), and data backups. A law firm would encrypt client data stored on laptops and servers.
- Information Protection Processes and Procedures: Developing and implementing security policies, procedures, and standards. This includes change management processes.
- Maintenance: Maintaining and repairing IT infrastructure and equipment to ensure it is up-to-date and secure. This involves patching vulnerabilities.
- Protective Technology: Implementing technical security solutions such as firewalls, intrusion detection systems, and anti-malware software.
- Detect: This function focuses on the activities necessary to identify the occurrence of a cybersecurity event. Timely detection is crucial for minimizing the impact of incidents.
- Anomalies and Events: Establishing baseline performance metrics and monitoring systems for unusual activity.
- Security Continuous Monitoring: Implementing continuous monitoring of security controls to ensure they are functioning effectively.
- Detection Processes: Implementing processes for detecting and analyzing security events. This includes log analysis and incident response planning.
- Respond: This function Artikels the activities to take when a cybersecurity event is detected. It includes containment, eradication, and recovery.
- Response Planning: Developing and implementing an incident response plan to address cybersecurity incidents. This plan should include roles, responsibilities, and communication protocols.
- Communications: Communicating with internal and external stakeholders during and after an incident. This includes notifying law enforcement and affected customers.
- Analysis: Analyzing the incident to determine its root cause and scope.
- Mitigation: Taking steps to contain and eradicate the incident.
- Improvements: Learning from the incident and making improvements to security controls and processes.
- Recover: This function focuses on restoring capabilities or services that were impaired due to a cybersecurity incident. It involves activities like disaster recovery and business continuity planning.
- Recovery Planning: Developing and implementing a recovery plan to restore systems and data after an incident.
- Improvements: Making improvements based on lessons learned from the recovery process.
- Communications: Communicating with internal and external stakeholders during the recovery process.
Benefits of Adopting the NIST Cybersecurity Framework
Adopting the NIST Cybersecurity Framework offers several significant benefits to an organization, improving its overall cybersecurity posture and resilience.
- Improved Risk Management: The framework provides a structured approach to identifying, assessing, and managing cybersecurity risks, leading to better-informed decisions.
- Enhanced Cybersecurity Posture: By implementing the framework, organizations can strengthen their security controls and reduce their vulnerability to cyberattacks.
- Increased Business Resilience: The framework helps organizations prepare for and respond to cybersecurity incidents, minimizing downtime and disruption.
- Better Communication and Collaboration: The framework provides a common language and framework for communicating about cybersecurity risks and activities, improving collaboration within the organization and with external stakeholders.
- Compliance and Regulatory Alignment: The framework helps organizations meet compliance requirements and industry best practices.
- Cost Reduction: By proactively managing cybersecurity risks, organizations can reduce the costs associated with data breaches and other security incidents.
NIST Cybersecurity Framework Tiers
The NIST Cybersecurity Framework uses tiers to describe the degree to which an organization’s cybersecurity risk management practices exhibit the characteristics of the Framework. The tiers provide a context for how an organization views cybersecurity risk and the resources it dedicates to managing that risk. The tiers are not maturity levels; rather, they describe the characteristics of an organization’s cybersecurity practices.
- Tier 1: Partial: In this tier, cybersecurity risk management practices are often ad hoc and reactive. The organization may have limited awareness of cybersecurity risks and may not have established policies or procedures. The focus is often on immediate needs rather than a proactive approach.
- Tier 2: Risk Informed: In this tier, the organization is aware of cybersecurity risks and has implemented some risk management practices. Policies and procedures may exist, but they may not be consistently applied. The organization has some awareness of cybersecurity risks, but the understanding is not fully integrated into organizational culture.
- Tier 3: Repeatable: In this tier, the organization has well-defined cybersecurity risk management practices that are consistently applied across the organization. Policies and procedures are documented and followed, and there is a focus on continuous improvement. The organization understands its cybersecurity risks and actively manages them.
- Tier 4: Adaptive: In this tier, the organization has a mature cybersecurity risk management program that is adaptive to changing threats and vulnerabilities. The organization continuously monitors and improves its security posture, and cybersecurity is fully integrated into the organizational culture. The organization is proactive in its approach to cybersecurity and anticipates emerging threats.
Identifying Assets and Assessing Risks
Understanding and managing cybersecurity risks effectively hinges on a clear understanding of your organization’s assets and the potential threats they face. This involves a systematic approach to identify, categorize, and prioritize both assets and risks, aligning with the foundational principles of the NIST Cybersecurity Framework. This process allows for the implementation of appropriate security controls, ensuring that the most critical assets are protected against the most likely and impactful threats.
Cataloging Critical Assets
A comprehensive asset inventory is the cornerstone of a robust cybersecurity posture. This involves identifying and documenting all valuable assets, including data, systems, and infrastructure. A well-maintained asset inventory provides a clear picture of the organization’s attack surface and facilitates informed decision-making regarding security investments and resource allocation. Below is an example of a four-column HTML table designed to catalog critical assets.
| Asset Type | Description | Location | Importance |
|---|---|---|---|
| Data | Customer Personally Identifiable Information (PII) database | Secure database server, accessible only via VPN | High – Required for regulatory compliance (e.g., GDPR, CCPA); significant financial impact if breached. |
| System | Web Application Server | Data center, behind a firewall and intrusion detection system (IDS) | High – Critical for online sales and customer interaction; significant reputational damage if unavailable. |
| Infrastructure | Network Router | Network operations center (NOC) | High – Essential for network connectivity and communication; service disruption if compromised. |
| Data | Financial Records | Accounting server, encrypted at rest | High – Contains sensitive financial information; significant financial loss if breached. |
| System | Email Server | On-premise server, protected by anti-spam and anti-malware solutions | Medium – Used for internal and external communications; potential for phishing attacks if compromised. |
| Infrastructure | Physical Security System (Cameras, Access Control) | Various locations within the office and data center | Medium – Protects physical assets and personnel; potential for data breaches if compromised. |
Conducting a Risk Assessment
A thorough risk assessment is crucial for identifying and evaluating potential threats and vulnerabilities. This process involves identifying threats, analyzing vulnerabilities, and determining the likelihood and impact of potential security incidents. The assessment informs the selection and implementation of appropriate security controls.
- Threat Identification: Identify potential threats that could exploit vulnerabilities in your assets. Threats can be categorized as:
- Malicious Actors: Individuals or groups with the intent to cause harm, such as hackers, insiders, and nation-state actors. Example: A disgruntled employee intentionally deleting critical data.
- Accidental Threats: Human error, such as misconfiguration or accidental data exposure. Example: An employee accidentally sending an email containing sensitive information to the wrong recipient.
- Natural Disasters: Events such as floods, fires, and earthquakes. Example: A fire damaging a server room, leading to data loss and system downtime.
- Technical Failures: Hardware or software failures, such as system crashes or software bugs. Example: A critical software vulnerability exploited by an attacker.
- Vulnerability Analysis: Determine weaknesses in your systems, applications, and infrastructure that could be exploited by identified threats. Examples include:
- Unpatched software: Software with known vulnerabilities that have not been updated.
- Weak passwords: Passwords that are easily guessed or cracked.
- Misconfigured systems: Systems that are not properly configured, leaving them open to attack.
- Lack of access controls: Insufficient controls over who can access sensitive data.
Prioritizing Risks
Risk prioritization is a critical step in risk management, allowing organizations to focus their resources on the most significant threats. This process involves assessing the likelihood of a risk occurring and the potential impact if it does occur. A risk matrix is often used to visualize and prioritize risks.
- Likelihood: The probability that a threat will exploit a vulnerability. This can be assessed qualitatively (e.g., high, medium, low) or quantitatively (e.g., a percentage). Consider factors such as:
- The attacker’s motivation and capabilities.
- The prevalence of the vulnerability.
- The effectiveness of existing security controls.
- Impact: The potential damage that could result if a threat exploits a vulnerability. This can include:
- Financial loss.
- Reputational damage.
- Legal and regulatory penalties.
- Operational disruption.
- Risk Matrix: A common tool for visualizing risk. A risk matrix typically uses a two-dimensional grid, with likelihood on one axis and impact on the other. Risks are then plotted on the grid based on their likelihood and impact, allowing for prioritization. Risks in the high-risk quadrant require immediate attention. Risks in the low-risk quadrant may be accepted or mitigated as resources allow.
Designing a Simple Risk Register Template
A risk register is a document that captures the results of the risk assessment process. It provides a centralized location for documenting identified risks, their characteristics, and planned mitigation strategies.
| Risk ID | Asset Affected | Threat | Vulnerability | Likelihood | Impact | Risk Score | Mitigation Plan | Status | Owner |
|---|---|---|---|---|---|---|---|---|---|
| R001 | Customer PII Database | Malicious Hacker | SQL Injection Vulnerability | High | High | High (Likelihood x Impact) | Implement Web Application Firewall (WAF) and patch database server. | In Progress | Security Manager |
| R002 | Web Application Server | Accidental Data Breach | Insufficient Access Controls | Medium | High | Medium | Implement role-based access control (RBAC) and conduct regular user access reviews. | Open | IT Administrator |
| R003 | Network Router | Technical Failure | Outdated Firmware | Low | Medium | Low | Upgrade router firmware. | Completed | Network Administrator |
Implementing Security Controls (Protect Function)
The Protect function within the NIST Cybersecurity Framework focuses on developing and implementing safeguards to ensure the delivery of critical infrastructure services. This involves a range of activities, from establishing access controls to implementing data security measures and conducting security awareness training. Effectively implementing the Protect function is crucial for mitigating risks identified during the Identify and Assess phases, ultimately minimizing the impact of potential cybersecurity incidents.
Access Control in the Protect Function
Access control is a fundamental element of the Protect function, serving as a primary mechanism for limiting unauthorized access to systems, data, and physical facilities. It ensures that only authorized individuals and devices can interact with sensitive resources, thereby reducing the likelihood of data breaches and other security incidents. Implementing robust access controls is a continuous process, requiring regular review and updates to adapt to evolving threats and organizational changes.
- Identity and Access Management (IAM): IAM systems manage user identities, authentication, and authorization. They provide a centralized way to control who has access to what resources. Examples include Active Directory, Azure Active Directory, and Okta.
- Authentication Methods: Strong authentication methods, such as multi-factor authentication (MFA), are essential. MFA requires users to provide multiple forms of verification, like a password and a one-time code from a mobile device.
- Authorization Policies: Define what users can do after they have been authenticated. This often involves role-based access control (RBAC), where users are assigned roles with specific permissions.
- Least Privilege: Grant users only the minimum necessary access rights to perform their job functions. This principle limits the potential damage from compromised accounts.
- Regular Access Reviews: Periodically review user access rights to ensure they remain appropriate and remove access for terminated or transferred employees.
Security Awareness Training Programs
Security awareness training is a critical component of the Protect function, aiming to educate employees about cybersecurity threats and best practices. Effective training programs empower employees to recognize and respond to potential security incidents, such as phishing attacks and social engineering attempts. The content and frequency of training should be tailored to the organization’s specific risks and the roles of its employees.
- Phishing Simulations: Simulate phishing attacks to test employees’ ability to identify and avoid phishing emails. These simulations provide valuable feedback and allow for targeted training.
- Interactive Training Modules: Use interactive modules that cover a range of topics, including password security, social engineering, malware, and data privacy.
- Regular Refreshers: Conduct regular refresher training to reinforce key concepts and keep employees informed about the latest threats.
- Role-Based Training: Tailor training to specific job roles, addressing the unique security risks associated with each role. For example, IT staff will require different training than administrative staff.
- Gamification: Incorporate gamification elements, such as quizzes and leaderboards, to make training more engaging and effective.
Data Security Measures
Data security measures are crucial for protecting sensitive information from unauthorized access, disclosure, modification, or destruction. These measures encompass a range of technologies and practices designed to safeguard data throughout its lifecycle, from creation to disposal.
- Encryption: Encryption transforms data into an unreadable format, protecting it from unauthorized access.
- Encryption at Rest: Encrypt data stored on hard drives, servers, and other storage devices. Examples include BitLocker and LUKS.
- Encryption in Transit: Encrypt data transmitted over networks using protocols like Transport Layer Security (TLS) or Secure Shell (SSH).
- Data Loss Prevention (DLP): DLP tools monitor and prevent sensitive data from leaving the organization’s control.
- Network DLP: Monitors network traffic for sensitive data and blocks unauthorized transmissions.
- Endpoint DLP: Monitors data on endpoints, such as laptops and desktops, and prevents data leakage.
- Data Masking and Tokenization: These techniques obscure sensitive data while preserving its usability.
- Data Masking: Replaces sensitive data with realistic, but fictitious, data for testing and development purposes.
- Tokenization: Replaces sensitive data with a non-sensitive token. The original data is stored securely elsewhere.
- Data Backup and Recovery: Regularly back up data to ensure business continuity in the event of a data loss incident. Implement a robust disaster recovery plan.
Endpoint Security
Endpoint security focuses on securing devices such as laptops, desktops, smartphones, and tablets that connect to an organization’s network. These devices are often targeted by attackers and serve as entry points for malware and other threats. Effective endpoint security involves a layered approach that combines various tools and techniques.
- Antivirus and Anti-Malware Software: Protect endpoints from malware infections by scanning files, monitoring system activity, and blocking malicious code.
- Endpoint Detection and Response (EDR): EDR tools provide advanced threat detection, investigation, and response capabilities. They monitor endpoint activity in real-time, detect suspicious behavior, and enable security teams to respond quickly to incidents.
- Firewalls: Firewalls control network traffic entering and leaving endpoints, blocking unauthorized access and preventing malware from communicating with command-and-control servers.
- Vulnerability Management: Regularly scan endpoints for vulnerabilities and apply security patches to address them.
- Mobile Device Management (MDM): MDM solutions manage and secure mobile devices, enforcing security policies, controlling access to corporate data, and remotely wiping devices if necessary.
Detecting Cybersecurity Incidents
Detecting cybersecurity incidents is a critical function within the NIST Cybersecurity Framework, representing the proactive measures organizations take to identify and analyze anomalous activities that may indicate a security breach. This phase is vital for minimizing the impact of incidents and ensuring business continuity. It involves continuous monitoring, analysis of security events, and timely responses to potential threats.
Key Components of a Robust Security Monitoring System
A robust security monitoring system is essential for timely incident detection. It’s a layered approach, integrating various technologies and processes to provide comprehensive visibility into an organization’s security posture.
- Centralized Logging and Log Management: This involves collecting, storing, and analyzing logs from various sources, such as servers, network devices, and applications. Centralized logging allows for correlation of events across different systems, providing a holistic view of security events. A key component is the use of a Security Information and Event Management (SIEM) system, which aggregates and analyzes log data in real-time.
- Network Intrusion Detection and Prevention Systems (IDS/IPS): These systems monitor network traffic for malicious activities and policy violations. IDS passively monitors and alerts on suspicious events, while IPS actively blocks or mitigates threats.
- Endpoint Detection and Response (EDR): EDR solutions monitor endpoint devices (e.g., laptops, desktops) for suspicious behavior, providing visibility into activities occurring on individual machines. EDR tools often incorporate threat hunting capabilities, allowing security analysts to proactively search for threats.
- Security Information and Event Management (SIEM) System: SIEM systems collect and analyze security data from various sources, providing real-time visibility into security events. They correlate data, generate alerts, and support incident investigation and response.
- Vulnerability Scanning: Regularly scanning systems and applications for known vulnerabilities helps identify potential weaknesses that attackers could exploit. Vulnerability scanning tools assess systems for common vulnerabilities and misconfigurations.
- Security Orchestration, Automation, and Response (SOAR) Platforms: SOAR platforms automate incident response workflows, allowing security teams to respond to threats more efficiently. They can integrate with various security tools to automate tasks such as threat containment and remediation.
- User and Entity Behavior Analytics (UEBA): UEBA systems analyze user and entity behavior to identify anomalies that may indicate malicious activity or compromised accounts. They establish baselines of normal behavior and flag deviations.
Different Types of Security Logs and Their Purpose
Security logs are the raw data that fuels the detection process. Understanding the different types of logs and their specific purposes is fundamental to effective incident detection.
- System Logs: These logs record events related to the operating system, such as system startup and shutdown, user logins and logouts, and system errors. They provide information about the overall health and stability of the system.
- Application Logs: Application logs capture events related to specific applications, such as user actions, errors, and security-related events. These logs are crucial for understanding application behavior and identifying potential vulnerabilities or attacks.
- Network Logs: Network logs record network traffic data, including connection attempts, data transfers, and firewall activity. They provide visibility into network communications and can be used to detect malicious activity, such as unauthorized access attempts or data exfiltration.
- Security Logs: These logs specifically focus on security-related events, such as failed login attempts, changes to security settings, and attempts to access restricted resources. They provide critical information for detecting and investigating security incidents.
- Web Server Logs: Web server logs record information about web server activity, including user requests, errors, and access attempts. They can be used to identify malicious activity, such as web application attacks or unauthorized access attempts.
- Database Logs: Database logs record events related to database activity, such as user queries, data modifications, and security-related events. They provide valuable information for detecting unauthorized access, data breaches, or malicious activity targeting the database.
Use of Intrusion Detection and Prevention Systems (IDS/IPS)
IDS/IPS are crucial components of a robust security posture, playing a key role in detecting and preventing malicious activity on a network. They function by monitoring network traffic and comparing it against a database of known attack signatures or analyzing traffic patterns for anomalies.
- Intrusion Detection System (IDS): An IDS passively monitors network traffic and generates alerts when it detects suspicious activity. It typically uses signature-based detection, anomaly-based detection, or a combination of both. Signature-based detection compares network traffic against a database of known attack signatures. Anomaly-based detection identifies unusual traffic patterns or deviations from established baselines. The primary function of an IDS is to provide visibility into potential security incidents.
- Intrusion Prevention System (IPS): An IPS actively monitors network traffic and takes actions to block or mitigate threats. In addition to the detection capabilities of an IDS, an IPS can automatically block malicious traffic, drop suspicious connections, or take other preventative measures. IPS systems are typically deployed inline, meaning they sit directly in the path of network traffic.
- Deployment Considerations: The placement of IDS/IPS devices is critical for effective monitoring and prevention. Common deployment strategies include deploying them at the network perimeter, within the internal network, and on individual hosts. The choice of deployment strategy depends on the organization’s specific security requirements and network architecture.
- Signature-Based Detection: Signature-based detection relies on a database of known attack signatures. When network traffic matches a known signature, the system generates an alert or takes action. The effectiveness of signature-based detection depends on the completeness and accuracy of the signature database.
- Anomaly-Based Detection: Anomaly-based detection identifies unusual traffic patterns or deviations from established baselines. This approach can detect zero-day attacks or other previously unknown threats. Anomaly-based detection often requires a significant amount of baseline data to establish normal network behavior.
Establishing a Process for Incident Detection and Alert Management
Establishing a well-defined process for incident detection and alert management is crucial for an effective security program. This process ensures that potential security incidents are identified, investigated, and responded to in a timely and efficient manner.
- Define Incident Categories: Categorizing incidents helps prioritize response efforts and ensures that the appropriate resources are allocated to each incident. Incident categories can include malware infections, data breaches, unauthorized access attempts, and denial-of-service attacks.
- Establish Alert Thresholds and Prioritization: Setting appropriate alert thresholds and prioritizing alerts helps security teams focus on the most critical threats. Thresholds can be based on factors such as the severity of the potential impact, the likelihood of the threat, and the sensitivity of the affected assets.
- Implement a SIEM System and Configure Alerting Rules: A SIEM system is essential for collecting and analyzing security data from various sources. Configuring appropriate alerting rules ensures that security teams are notified of potential incidents in a timely manner. Alerting rules should be based on known attack patterns, suspicious activities, and deviations from established baselines.
- Develop Incident Response Procedures: Clear and well-defined incident response procedures are essential for ensuring a consistent and effective response to security incidents. These procedures should Artikel the steps to be taken, including containment, eradication, recovery, and post-incident activities.
- Train Security Personnel: Training security personnel on incident detection, alert management, and incident response procedures is essential for ensuring that they can effectively identify, investigate, and respond to security incidents. Training should include hands-on exercises and simulations to build practical skills.
- Regularly Review and Update Procedures: Incident response procedures should be regularly reviewed and updated to reflect changes in the threat landscape, security technologies, and organizational requirements. This ensures that the procedures remain effective and relevant.
- Conduct Tabletop Exercises and Simulations: Regularly conducting tabletop exercises and simulations helps security teams practice their incident response skills and identify areas for improvement. These exercises involve simulating real-world incidents and walking through the response procedures.
Responding to Cybersecurity Incidents
Effectively responding to cybersecurity incidents is a critical component of the NIST Cybersecurity Framework. This involves having a well-defined plan, the ability to detect and analyze incidents promptly, and the capacity to contain, eradicate, and recover from breaches. A robust incident response capability minimizes damage, reduces recovery time, and preserves an organization’s reputation.
Incident Response Planning Steps
Incident response planning provides a structured approach to handling cybersecurity incidents. This planning helps organizations to prepare for, identify, contain, eradicate, recover from, and learn from incidents. The following steps are crucial in the incident response planning process:
- Preparation: This phase involves establishing policies, procedures, and a dedicated incident response team. Training, awareness programs, and the procurement of necessary tools and resources are essential.
- Identification: This step focuses on detecting potential incidents. Monitoring security systems, analyzing logs, and establishing reporting mechanisms are key to identifying incidents promptly.
- Containment: Once an incident is identified, the goal is to limit its impact. This may involve isolating affected systems, disconnecting devices from the network, or implementing temporary security measures.
- Eradication: This involves removing the root cause of the incident. This may include removing malware, patching vulnerabilities, or resetting compromised accounts.
- Recovery: The recovery phase focuses on restoring affected systems and services to normal operation. This involves data restoration, system re-imaging, and ensuring that security controls are in place to prevent future incidents.
- Post-Incident Activity: This final phase involves analyzing the incident to identify lessons learned, updating incident response plans, and improving security controls. This includes conducting a thorough review of the incident, documenting findings, and implementing corrective actions.
Incident Handling Checklist
An incident handling checklist provides a step-by-step guide for responding to a cybersecurity incident. It ensures that all necessary actions are taken in a timely and coordinated manner. The following checklist can be adapted to suit an organization’s specific needs:
- Verification: Confirm the incident and assess its severity.
- Notification: Notify the incident response team, relevant stakeholders, and, if necessary, law enforcement or regulatory bodies.
- Data Collection: Gather all relevant data, including logs, system snapshots, and network traffic captures.
- Analysis: Analyze the collected data to determine the scope, impact, and root cause of the incident.
- Containment Actions: Implement containment measures to prevent further damage, such as isolating affected systems.
- Eradication Actions: Remove the cause of the incident, such as malware or unauthorized access.
- Recovery Actions: Restore affected systems and services to their normal operating state.
- Documentation: Document all actions taken, findings, and lessons learned.
- Post-Incident Review: Conduct a post-incident review to identify areas for improvement in the incident response plan and security controls.
Procedures for Containing and Eradicating a Security Breach
Effective containment and eradication procedures are essential for minimizing the damage caused by a security breach and preventing future incidents. These procedures must be carefully planned and executed to limit the impact of the breach.
- Containment Procedures: The primary goal of containment is to prevent the spread of the incident. Containment procedures can include:
- Isolating affected systems from the network.
- Disabling compromised accounts.
- Blocking malicious IP addresses or URLs.
- Implementing temporary firewall rules.
- Eradication Procedures: Once the incident is contained, the focus shifts to removing the root cause. Eradication procedures may involve:
- Removing malware or malicious code.
- Patching vulnerabilities.
- Resetting compromised passwords.
- Re-imaging affected systems.
Post-Incident Analysis and Lessons Learned
Post-incident analysis is a crucial step in the incident response process. It provides valuable insights that can be used to improve security posture and prevent future incidents. This analysis includes reviewing the incident, identifying the root cause, and documenting the lessons learned.
- Incident Review: Conduct a thorough review of the incident, including the timeline of events, the impact of the breach, and the actions taken to contain and eradicate it.
- Root Cause Analysis: Determine the underlying cause of the incident. This may involve identifying vulnerabilities, misconfigurations, or human errors that contributed to the breach.
- Lessons Learned: Document the lessons learned from the incident. This includes identifying areas for improvement in the incident response plan, security controls, and training programs.
- Documentation and Reporting: Prepare a detailed report that includes the incident timeline, impact assessment, root cause analysis, and lessons learned. Share the report with relevant stakeholders.
- Remediation and Improvement: Implement corrective actions based on the lessons learned. This may include updating security policies, improving security controls, and providing additional training to employees.
Recovering from Cybersecurity Incidents
Successfully recovering from a cybersecurity incident is crucial for minimizing damage, restoring normal operations, and maintaining stakeholder trust. This involves a structured approach that encompasses data recovery, business continuity, and effective communication. It’s not merely about fixing the immediate problem; it’s about ensuring the organization can withstand future attacks and maintain resilience.
Strategies for Data Recovery and Business Continuity
Data recovery and business continuity are essential components of a robust recovery plan. They work in tandem to restore data and critical business functions after a cybersecurity incident. The choice of strategies depends on factors such as the criticality of the data, the organization’s risk tolerance, and available resources.
- Data Backup and Restoration: Implementing regular and reliable data backups is the cornerstone of data recovery. Backups should be stored in a secure, off-site location to protect against physical damage or compromise of the primary systems. The frequency of backups depends on the data’s volatility and the Recovery Point Objective (RPO), which is the maximum acceptable data loss. Restoration processes must be tested periodically to ensure their effectiveness.
For example, a financial institution might perform daily incremental backups and weekly full backups, storing them in a geographically separate data center.
- Failover Systems and Redundancy: Utilizing failover systems and redundancy ensures that critical systems and applications remain available even if the primary systems are compromised. This involves having backup systems that can automatically take over if the primary system fails. Redundancy can be implemented at various levels, including hardware, network, and data. For instance, a hospital might have a redundant network and servers to ensure continuous access to patient records and medical equipment.
- Virtualization and Cloud-Based Solutions: Virtualization and cloud-based solutions provide flexibility and scalability in data recovery. Virtualized environments allow for quick restoration of systems and applications from backups. Cloud-based services offer off-site storage and disaster recovery capabilities, often with automated failover mechanisms. A small business could leverage a cloud-based backup and disaster recovery service to minimize the cost and complexity of maintaining its own infrastructure.
- Data Replication: Data replication involves creating real-time or near real-time copies of data on a secondary system. This allows for a seamless transition to the secondary system in case of a primary system failure. There are several types of data replication, including synchronous replication (real-time) and asynchronous replication (delayed). A large e-commerce company might use synchronous replication for its database to ensure that customer transactions are always available.
Examples of Disaster Recovery Plans and Their Components
A comprehensive disaster recovery plan (DRP) Artikels the steps an organization will take to recover from a cybersecurity incident or other disruptive event. It should be a living document, regularly updated and tested to reflect changes in the organization’s environment. A well-defined DRP includes several key components.
- Plan Scope and Objectives: Defines the scope of the plan, including the systems, data, and processes covered. It also specifies the objectives, such as the Recovery Time Objective (RTO), which is the maximum acceptable downtime, and the RPO. For example, a DRP for a manufacturing company might focus on restoring production systems and ensuring the availability of critical supply chain data.
- Roles and Responsibilities: Clearly defines the roles and responsibilities of individuals and teams involved in the recovery process. This includes incident responders, IT staff, business unit representatives, and communication teams. A detailed list of contact information for key personnel should be included. A healthcare provider would clearly define the roles of the IT department, security team, and medical staff in restoring patient data.
- System Recovery Procedures: Provides detailed procedures for restoring systems and applications from backups or failover systems. These procedures should be step-by-step and include checklists to ensure consistency and accuracy. A bank would have detailed procedures for restoring its core banking system, including steps for restoring databases, applications, and network connectivity.
- Data Backup and Recovery Procedures: Artikels the procedures for backing up and restoring data, including the backup schedule, storage locations, and restoration methods. It should specify the tools and technologies used for backup and recovery. A law firm would have specific procedures for backing up and restoring client data, ensuring compliance with data privacy regulations.
- Communication Plan: Establishes a communication plan for notifying stakeholders, including employees, customers, partners, and regulatory agencies, about the incident and the recovery progress. This plan should include contact information, communication templates, and escalation procedures. An airline would have a communication plan for informing passengers about flight disruptions caused by a cybersecurity incident.
- Testing and Maintenance Schedule: Specifies the schedule for testing and maintaining the DRP. This includes regular testing of backup and recovery procedures, as well as periodic reviews and updates of the plan. A retail chain would conduct annual tests of its DRP to ensure that it can recover from a point-of-sale system outage.
Testing and Maintaining Recovery Plans
Testing and maintaining recovery plans are critical for ensuring their effectiveness. Regular testing helps identify weaknesses, validate procedures, and train personnel. Maintenance involves updating the plan to reflect changes in the organization’s environment, systems, and processes.
- Types of Testing: Various types of testing can be used to evaluate the DRP, including:
- Tabletop Exercises: A discussion-based exercise where team members walk through the plan and discuss their roles and responsibilities.
- Walkthrough Tests: A hands-on exercise where team members simulate the recovery process.
- Simulated Failover Tests: A test that simulates a system failure and triggers the failover mechanism.
- Full System Recovery Tests: A comprehensive test that involves restoring systems and applications from backups.
- Testing Frequency: The frequency of testing depends on the criticality of the systems and data, the rate of change in the environment, and regulatory requirements. Critical systems should be tested more frequently than less critical systems. For example, a financial institution might test its DRP quarterly, while a small business might test it annually.
- Documentation of Test Results: Test results should be documented, including any issues identified, lessons learned, and recommendations for improvement. This documentation should be used to update the DRP and improve the recovery process. After each test, a report detailing the test’s scope, participants, findings, and actions taken should be created.
- Plan Updates: The DRP should be reviewed and updated regularly to reflect changes in the organization’s environment, systems, and processes. Updates should be made after each test, after significant changes to the IT infrastructure, and at least annually. The DRP should be revised when new threats emerge or after any major incident to incorporate the lessons learned.
Importance of Communication During the Recovery Process
Effective communication is essential for managing expectations, maintaining stakeholder trust, and coordinating the recovery efforts during a cybersecurity incident. A well-defined communication plan helps ensure that the right information reaches the right people at the right time.
- Internal Communication: Communicating with employees is crucial for keeping them informed about the incident, the recovery progress, and any actions they need to take. This can be done through email, intranet, or other communication channels. A manufacturing company should inform its employees about the incident, the steps being taken to restore production, and any changes to their work schedules.
- External Communication: Communicating with customers, partners, and the public is important for managing their expectations and maintaining trust. This can be done through press releases, website updates, social media, or direct communication. A healthcare provider would inform its patients about the incident, the steps being taken to protect their data, and any potential impact on their care.
- Stakeholder Management: Identify and prioritize key stakeholders, such as customers, partners, regulators, and the media. Develop tailored communication strategies for each group. A retail company would communicate with its customers about the incident and offer compensation, such as free credit monitoring services.
- Communication Channels: Establish multiple communication channels to ensure that information can be disseminated effectively. This includes email, phone, website updates, social media, and press releases. A financial institution might use email, phone, and its website to communicate with its customers about a data breach.
- Message Consistency: Ensure that all communications are consistent and accurate. This requires a clear understanding of the incident, the recovery progress, and the organization’s response. Designate a spokesperson to be the primary point of contact for all communications.
Mapping Existing Security Practices to the Framework
Mapping existing security practices to the NIST Cybersecurity Framework is a crucial step in aligning an organization’s cybersecurity posture with a recognized and widely accepted standard. This process allows organizations to understand their current security capabilities, identify gaps, and prioritize efforts to improve their overall security posture. It involves comparing existing security controls against the functions, categories, and subcategories defined within the NIST Cybersecurity Framework.
Mapping Current Security Controls to Framework Functions and Categories
The process of mapping involves comparing existing security controls to the five core functions of the NIST Cybersecurity Framework: Identify, Protect, Detect, Respond, and Recover. Each function is further divided into categories, which represent specific security outcomes, and subcategories, which provide more detailed guidance.To begin mapping, an organization should:
- Inventory Current Security Controls: Create a comprehensive list of all existing security controls. This includes technical controls (e.g., firewalls, intrusion detection systems), administrative controls (e.g., policies, procedures), and physical controls (e.g., access control systems).
- Identify Framework Functions and Categories: Understand the five core functions and associated categories of the NIST Cybersecurity Framework. For example, the “Protect” function includes categories like “Identity Management and Access Control,” “Data Security,” and “Information Protection Processes and Procedures.”
- Compare Controls to Framework: For each existing security control, determine which NIST Cybersecurity Framework function, category, and subcategory it aligns with. This can be done by examining the control’s purpose, implementation, and the security outcomes it achieves.
- Document the Mapping: Create a mapping document or spreadsheet that lists each existing security control and its corresponding NIST Cybersecurity Framework alignment. This documentation serves as a valuable reference point for understanding the organization’s current security posture.
For example, consider an organization that has implemented a multi-factor authentication (MFA) system for all remote access. This control would map to the “Protect” function, specifically the “Identity Management and Access Control” category, and potentially several subcategories related to access control and authentication. Another example would be the use of a Security Information and Event Management (SIEM) system, which maps to the “Detect” function, specifically the “Anomalies and Events” category, and then to the subcategories that detail log analysis and security monitoring.
Identifying Gaps Between Current Practices and Framework Requirements
Once the mapping is complete, the next step is to identify any gaps between the organization’s current security practices and the requirements Artikeld in the NIST Cybersecurity Framework. These gaps represent areas where the organization’s security posture may be deficient or where improvements are needed.Gaps can be identified by:
- Analyzing the Mapping Document: Review the mapping document to identify any NIST Cybersecurity Framework subcategories for which no corresponding security controls exist.
- Assessing the Effectiveness of Existing Controls: Evaluate the effectiveness of existing controls to determine whether they adequately address the requirements of the corresponding framework subcategories.
- Comparing Against Industry Best Practices: Compare the organization’s security practices against industry best practices and benchmarks to identify potential gaps.
For example, if an organization lacks a formal incident response plan, a gap would be identified in the “Respond” function, specifically the “Response Planning” category and related subcategories. Similarly, if an organization does not regularly test its data backup and recovery procedures, a gap would be identified in the “Recover” function, specifically the “Recovery Planning” category. Identifying these gaps allows organizations to prioritize and allocate resources to address the most critical deficiencies in their security posture.
Methods for Prioritizing Remediation Efforts
Prioritizing remediation efforts is essential for effectively addressing identified gaps. Organizations should adopt a risk-based approach to prioritize their efforts, focusing on the most critical vulnerabilities and the controls that will have the greatest impact on reducing risk.Methods for prioritizing remediation efforts include:
- Risk Assessment: Conduct a risk assessment to identify and evaluate the potential impact and likelihood of threats exploiting identified vulnerabilities. This assessment should consider the value of the assets at risk and the potential consequences of a security breach.
- Gap Analysis: Perform a gap analysis to compare the organization’s current security posture against the requirements of the NIST Cybersecurity Framework.
- Prioritization Matrix: Use a prioritization matrix to rank remediation efforts based on their risk score, the effort required to implement the control, and the potential impact on the organization’s security posture.
- Compliance Requirements: Consider any relevant compliance requirements, such as those mandated by industry regulations or government agencies. Remediation efforts required to meet compliance obligations should be prioritized accordingly.
For instance, a high-risk vulnerability that affects critical business systems should be prioritized over a low-risk vulnerability affecting less critical assets. Remediation efforts that address multiple gaps across different NIST Cybersecurity Framework functions and categories should also be prioritized.
Visual Representation of a Mapping Process
The following table provides a simplified visual representation of a mapping process, illustrating how an organization might map its existing security controls to the NIST Cybersecurity Framework. The table demonstrates a mapping exercise for a hypothetical organization, “ExampleCorp.”
| Existing Security Control | NIST Cybersecurity Framework Function | NIST Cybersecurity Framework Category | NIST Cybersecurity Framework Subcategory (Example) | Gap Identified? (Y/N) | Priority |
|---|---|---|---|---|---|
| Firewall Implementation | Protect | Access Control | AC-1: Access control policies and procedures are established and documented. | N | High |
| Intrusion Detection System (IDS) | Detect | Anomalies and Events | DE-1: Anomalous activity is detected. | N | High |
| Data Backup and Recovery Procedures (Testing) | Recover | Recovery Planning | RC-2: Recovery plans are tested. | N | Medium |
| Incident Response Plan | Respond | Response Planning | RS-1: Response plan is executed during an incident. | N | High |
| Security Awareness Training (Employees) | Protect | Awareness and Training | PR-4: Security awareness training is provided. | N | Medium |
| Vulnerability Scanning | Detect | Security Continuous Monitoring | DE-2: Security events are correlated and analyzed. | N | High |
| Password Policy Enforcement | Protect | Identity Management and Access Control | PR-AC-1: Access control policies and procedures are established and documented. | N | Medium |
| Regular Penetration Testing | Detect | Security Continuous Monitoring | DE-3: Vulnerability scans are performed. | N | High |
| Data Loss Prevention (DLP) | Protect | Data Security | PR-DS-1: Data loss prevention measures are implemented. | N | High |
| Physical Security (e.g., Access Control) | Protect | Physical Security | PR-PS-1: Physical security controls are implemented. | N | Medium |
| Remote Access Policy (MFA) | Protect | Identity Management and Access Control | PR-AC-4: Remote access to resources is controlled. | N | High |
| Patch Management | Protect | Information Protection Processes and Procedures | PR-IP-3: Vulnerabilities are managed. | N | High |
This table demonstrates how existing security controls are mapped to NIST Cybersecurity Framework functions, categories, and subcategories. The “Gap Identified?” column indicates whether a gap exists, and the “Priority” column indicates the relative importance of addressing the control. The table allows for an easy assessment of the current security posture and helps to identify areas that require improvement. For example, if a vulnerability scan isn’t performed regularly, it would identify a gap.
Selecting and Implementing Cybersecurity Tools
The effective selection and implementation of cybersecurity tools are crucial for organizations seeking to bolster their security posture and align with the NIST Cybersecurity Framework. These tools provide the technical capabilities necessary to protect, detect, respond to, and recover from cybersecurity incidents. A strategic approach to tool selection and deployment, considering the organization’s specific needs and risk profile, is essential for maximizing their effectiveness.
Identifying Different Types of Cybersecurity Tools
A wide array of cybersecurity tools is available, each designed to address specific security challenges. Understanding the various categories and functions of these tools is the first step in building a robust security infrastructure.
- Security Information and Event Management (SIEM) Systems: SIEM systems aggregate and analyze security-related data from various sources, such as firewalls, intrusion detection systems, and endpoint devices. They provide real-time monitoring, alerting, and reporting capabilities to detect and respond to security incidents. For instance, a SIEM system might identify unusual login attempts or suspicious network traffic patterns, triggering alerts for security personnel.
- Vulnerability Scanners: Vulnerability scanners automatically identify weaknesses in systems, applications, and networks. They assess configurations, patch levels, and potential vulnerabilities, providing reports that prioritize remediation efforts. Examples include tools that scan for outdated software or misconfigured settings that could be exploited by attackers.
- Firewalls: Firewalls act as a barrier between a trusted internal network and untrusted external networks, such as the internet. They control network traffic based on predefined rules, preventing unauthorized access and malicious activity. Firewalls can be hardware-based or software-based and operate at the network layer to inspect and filter traffic.
- Intrusion Detection and Prevention Systems (IDPS): IDPS monitor network traffic and system activity for malicious behavior. Intrusion Detection Systems (IDS) primarily detect and alert on suspicious activities, while Intrusion Prevention Systems (IPS) take proactive measures to block or mitigate threats. IDPS use signature-based, anomaly-based, and behavioral analysis techniques to identify potential threats.
- Endpoint Detection and Response (EDR) Tools: EDR tools provide real-time monitoring and analysis of endpoint devices, such as computers and servers. They detect and respond to threats by collecting data on endpoint activities, identifying suspicious behavior, and providing incident response capabilities. EDR tools often include features like threat hunting, malware analysis, and endpoint isolation.
- Data Loss Prevention (DLP) Solutions: DLP solutions are designed to prevent sensitive data from leaving an organization’s control. They monitor and control data movement, identify and block unauthorized data transfers, and enforce data security policies. DLP tools can be used to protect confidential information, intellectual property, and customer data.
- Security Orchestration, Automation, and Response (SOAR) Platforms: SOAR platforms automate security tasks and workflows, enabling faster incident response and improved efficiency. They integrate with various security tools to collect threat intelligence, analyze incidents, and automate response actions. SOAR platforms streamline security operations and reduce the burden on security teams.
- Web Application Firewalls (WAFs): WAFs protect web applications from attacks, such as cross-site scripting (XSS), SQL injection, and other web-based vulnerabilities. They filter malicious traffic and protect web applications from being compromised. WAFs analyze HTTP traffic and apply security rules to block or mitigate attacks.
Providing Examples of How to Evaluate and Select the Appropriate Tools for an Organization
Selecting the right cybersecurity tools requires a thorough evaluation process, considering the organization’s specific needs, risk profile, and budget. The following steps can guide this process.
- Define Security Requirements: Start by identifying the organization’s critical assets, threats, and vulnerabilities. This includes understanding the types of data that need protection, the regulatory requirements that apply, and the potential attack vectors.
- Conduct a Needs Assessment: Evaluate the organization’s current security posture and identify gaps in its security controls. This involves assessing existing tools and processes and determining where improvements are needed.
- Research and Evaluate Potential Tools: Research available cybersecurity tools and evaluate their capabilities, features, and performance. Consider factors such as ease of use, integration with existing systems, and vendor support.
- Conduct Proof-of-Concept (POC) Testing: Conduct POC testing with a shortlist of tools to assess their effectiveness in the organization’s environment. This involves testing the tools in a controlled environment to evaluate their performance and identify any compatibility issues.
- Consider Total Cost of Ownership (TCO): Evaluate the total cost of ownership, including the initial purchase price, ongoing maintenance costs, and the cost of training and support.
- Assess Vendor Reputation and Support: Research the vendor’s reputation, customer reviews, and support offerings. Ensure that the vendor provides adequate support and training to help the organization effectively use the tool.
- Align with the NIST Cybersecurity Framework: Select tools that align with the organization’s security goals and the NIST Cybersecurity Framework. Consider how the tools will support the five core functions: Identify, Protect, Detect, Respond, and Recover.
For example, a healthcare organization handling sensitive patient data might prioritize DLP solutions to prevent data breaches and ensure compliance with HIPAA regulations. A financial institution would likely invest in SIEM and threat intelligence platforms to monitor for fraudulent activities and meet regulatory requirements like PCI DSS.
Sharing Best Practices for Implementing Cybersecurity Tools
Effective implementation is crucial for maximizing the benefits of cybersecurity tools. The following best practices should be considered.
- Plan and Design: Develop a detailed implementation plan that Artikels the scope, timeline, and resources required. Define clear objectives and success criteria.
- Configuration and Customization: Configure the tools to meet the organization’s specific needs and security policies. Customize the tools to integrate with existing systems and workflows.
- Testing and Validation: Thoroughly test the tools to ensure they are functioning correctly and providing the expected results. Validate the tools’ effectiveness in detecting and responding to security threats.
- Training and Documentation: Provide adequate training to security personnel and other relevant staff on how to use and maintain the tools. Develop comprehensive documentation that covers the tools’ features, configuration, and troubleshooting procedures.
- Integration: Integrate the tools with other security systems and tools to create a holistic security posture. Ensure seamless data sharing and communication between the tools.
- Regular Monitoring and Maintenance: Continuously monitor the tools’ performance and effectiveness. Perform regular maintenance, including patching, updates, and configuration adjustments.
- Continuous Improvement: Regularly review the tools’ performance and identify areas for improvement. Stay up-to-date with the latest threats and vulnerabilities and adapt the tools accordingly.
Discussing the Importance of Integrating Tools for a Holistic Security Posture
Integrating cybersecurity tools is essential for creating a holistic security posture that provides comprehensive protection against cyber threats. Isolated tools, while valuable individually, may not provide the same level of protection as integrated solutions.
- Enhanced Visibility: Integrated tools provide a centralized view of security events and data, enabling security teams to gain better visibility into the organization’s security posture.
- Improved Threat Detection: Integration allows for correlation of data from multiple sources, improving the ability to detect sophisticated threats that might be missed by individual tools.
- Faster Incident Response: Integrated tools can automate incident response workflows, enabling security teams to respond to incidents more quickly and efficiently.
- Reduced Manual Effort: Integration automates repetitive tasks, reducing the manual effort required for security operations.
- Better Compliance: Integrated tools can help organizations meet regulatory requirements by providing comprehensive security controls and reporting capabilities.
For example, integrating a SIEM system with a vulnerability scanner and an IDPS allows security teams to correlate vulnerability data with intrusion detection alerts, providing a more comprehensive view of potential threats. This integrated approach helps to prioritize remediation efforts and respond to incidents more effectively. Another example is integrating an EDR tool with a SOAR platform. This allows for automated incident response, where the EDR tool detects a threat, and the SOAR platform automatically isolates the affected endpoint and initiates other response actions based on predefined playbooks.
Measuring and Improving Cybersecurity Posture
Maintaining a robust cybersecurity posture is not a one-time task but an ongoing process. It requires consistent monitoring, evaluation, and refinement of security controls. This section details how to measure the effectiveness of cybersecurity measures, identify key performance indicators (KPIs), conduct regular assessments, and establish a continuous improvement process.
Measuring the Effectiveness of Cybersecurity Controls
Measuring the effectiveness of cybersecurity controls is essential to ensure they are functioning as intended and providing the necessary protection. This involves evaluating how well the controls mitigate identified risks and contribute to the overall security posture. Effectiveness can be gauged through various methods, combining technical assessments with qualitative evaluations.
- Technical Assessments: These involve using tools and techniques to evaluate the performance of security controls. Examples include vulnerability scans, penetration testing, and security information and event management (SIEM) system analysis. Vulnerability scans identify weaknesses in systems and applications, while penetration testing simulates real-world attacks to assess the resilience of security defenses. SIEM systems collect and analyze security logs to detect and respond to incidents.
- Qualitative Evaluations: These assessments involve human judgment and expertise to evaluate the effectiveness of security controls. This can include reviewing security policies and procedures, conducting interviews with personnel, and assessing the overall security culture within the organization.
- Control Testing: This involves directly testing the functionality of security controls to ensure they are working as expected. For example, testing the effectiveness of a firewall by attempting to block unauthorized network traffic or testing the ability of an intrusion detection system (IDS) to identify malicious activity.
- Incident Response Testing: Simulating cybersecurity incidents to evaluate the effectiveness of incident response plans and procedures. This includes tabletop exercises and full-scale simulations to test the ability to detect, contain, and recover from security breaches.
Key Performance Indicators (KPIs) for Cybersecurity
Key Performance Indicators (KPIs) provide measurable data to track the performance of cybersecurity efforts. These metrics help organizations understand their current security posture, identify areas for improvement, and demonstrate the value of their security investments. Choosing the right KPIs depends on the organization’s specific goals, risks, and industry regulations.
- Mean Time to Detect (MTTD): This KPI measures the average time it takes to identify a security incident. A lower MTTD indicates a more effective incident detection capability.
- Mean Time to Respond (MTTR): This KPI measures the average time it takes to respond to and contain a security incident. A lower MTTR signifies a more efficient incident response process.
- Number of Security Incidents: Tracking the frequency of security incidents provides insight into the overall security posture. A decrease in the number of incidents generally indicates an improvement in security.
- Vulnerability Remediation Time: This KPI measures the time it takes to remediate identified vulnerabilities. Reducing remediation time minimizes the window of opportunity for attackers.
- Percentage of Systems Patched: This KPI tracks the percentage of systems that have been patched with the latest security updates. A higher percentage indicates a more secure environment.
- Phishing Click-Through Rate: This KPI measures the percentage of employees who click on malicious links in phishing emails. A lower click-through rate suggests effective security awareness training.
- Compliance with Security Policies: This KPI measures the extent to which employees and systems comply with established security policies and procedures.
- Security Awareness Training Completion Rate: This KPI tracks the percentage of employees who complete security awareness training. A higher completion rate contributes to a more security-conscious workforce.
Methods for Conducting Regular Audits and Assessments
Regular audits and assessments are critical for evaluating the effectiveness of cybersecurity controls and identifying areas for improvement. These assessments should be conducted at regular intervals, or when significant changes occur in the IT environment or threat landscape. Different types of audits and assessments can be used to evaluate various aspects of cybersecurity.
- Vulnerability Assessments: These assessments identify vulnerabilities in systems, applications, and networks. Vulnerability scanning tools automate the process of identifying known vulnerabilities, while penetration testing simulates real-world attacks to exploit identified weaknesses.
- Penetration Testing: Penetration testing involves simulating real-world attacks to identify vulnerabilities and weaknesses in a system or network. Ethical hackers, or penetration testers, use various techniques to attempt to gain unauthorized access, demonstrating the potential impact of a successful attack.
- Compliance Audits: These audits assess an organization’s adherence to industry regulations, standards, and internal security policies. They often involve reviewing documentation, interviewing personnel, and testing security controls to verify compliance.
- Risk Assessments: Risk assessments identify and evaluate potential threats, vulnerabilities, and impacts to information assets. This process involves analyzing the likelihood of threats, the potential impact of successful attacks, and the effectiveness of existing security controls.
- Security Audits: Security audits involve a comprehensive review of an organization’s security posture. These audits assess the effectiveness of security controls, identify gaps in security practices, and provide recommendations for improvement.
Designing a Continuous Improvement Process
A continuous improvement process ensures that cybersecurity efforts evolve with the changing threat landscape and organizational needs. This iterative process uses the results of audits, assessments, and performance metrics to identify areas for improvement, implement changes, and measure the effectiveness of those changes.
- Establish a Baseline: Begin by establishing a baseline understanding of the current security posture. This involves conducting initial audits, assessments, and risk assessments to identify strengths, weaknesses, and areas for improvement.
- Identify Areas for Improvement: Based on the findings from audits, assessments, and performance metrics, identify specific areas where improvements are needed. Prioritize these areas based on their potential impact and the organization’s risk tolerance.
- Develop Action Plans: Create detailed action plans to address the identified areas for improvement. These plans should include specific tasks, timelines, responsible parties, and resource allocation.
- Implement Changes: Implement the changes Artikeld in the action plans. This may involve deploying new security tools, updating policies and procedures, providing security awareness training, or making changes to system configurations.
- Monitor and Measure: Continuously monitor the effectiveness of the implemented changes using performance metrics and regular assessments. Track KPIs, conduct vulnerability scans, and perform penetration testing to evaluate the impact of the improvements.
- Review and Refine: Regularly review the results of monitoring and measurement activities. Identify any remaining gaps or weaknesses and refine the action plans accordingly. The continuous improvement process is iterative, so repeat the cycle to further enhance the cybersecurity posture.
Wrap-Up
In conclusion, mastering the NIST Cybersecurity Framework is not merely about compliance; it’s about building a culture of security and resilience. By understanding the core functions, implementing practical controls, and continuously improving your approach, your organization can effectively protect its assets and respond to cyber threats. This journey requires ongoing effort and adaptation, but the benefits—a more secure environment and increased trust—are well worth the investment.
FAQ Resource
What is the primary goal of the NIST Cybersecurity Framework?
The primary goal is to help organizations manage and reduce cybersecurity risks in a cost-effective way, improving their overall cybersecurity posture.
How often should an organization review and update its cybersecurity framework implementation?
Regular reviews and updates should be conducted, ideally at least annually, or more frequently if significant changes occur in the threat landscape, business operations, or technology infrastructure.
Does the NIST Cybersecurity Framework mandate specific security technologies?
No, the framework is flexible and does not mandate specific technologies. It provides a framework for identifying and implementing appropriate security controls based on an organization’s specific needs and risk profile.