The transition to cloud computing offers significant advantages, from enhanced scalability and cost efficiency to improved agility. However, migrating an entire application portfolio to the cloud simultaneously is often impractical and can lead to disruptions. Therefore, the process of prioritizing applications for cloud migration becomes a critical strategic undertaking. This document provides a structured methodology for evaluating and ranking applications, ensuring a smooth and successful cloud adoption journey.
This guide delves into the multifaceted considerations involved in prioritizing applications. It encompasses detailed assessments of existing application landscapes, definition of clear migration goals, and the identification of interdependencies. It also includes evaluation of technical feasibility, business value assessment, risk mitigation strategies, and the creation of a prioritization matrix to streamline the migration process.
Assessing Current Application Portfolio
Understanding the current application landscape is the foundational step in any successful cloud migration strategy. This involves a comprehensive assessment of existing applications, their functionalities, dependencies, infrastructure, and performance characteristics. This assessment provides the necessary data to make informed decisions regarding the suitability of applications for cloud migration, the optimal migration approach, and the required cloud resources.
Cataloging Existing Applications and Functionalities
A thorough catalog of existing applications is crucial for understanding the application portfolio. This process involves identifying all applications, documenting their core functionalities, and mapping their interdependencies. This catalog serves as a central repository of information, facilitating subsequent analysis and decision-making.
- Application Identification: Begin by creating a comprehensive list of all applications within the organization. This includes both internal and external-facing applications, as well as supporting services and utilities. Utilize discovery tools and consult with various stakeholders, including application owners, developers, and infrastructure teams, to ensure completeness.
- Functionality Documentation: For each application, document its primary functionalities and purpose. Describe the business processes supported by the application and its key features. This documentation should be clear, concise, and easily understandable by both technical and non-technical stakeholders.
- Dependency Mapping: Identify and document the dependencies of each application on other applications, services, databases, and infrastructure components. Dependencies can be direct (e.g., one application calling another) or indirect (e.g., applications sharing a common database). Understanding these dependencies is crucial for planning the migration order and minimizing disruption. A dependency matrix can be used to visually represent these relationships.
- Data Flow Analysis: Analyze the flow of data within and between applications. This includes identifying the sources, destinations, and transformations of data. Understanding data flows is essential for ensuring data integrity and security during and after the migration.
Documenting Current Infrastructure
Documenting the current infrastructure is essential to understanding the existing environment and planning for cloud migration. This involves capturing detailed information about the hardware, software, and network components that host each application. This information is crucial for assessing the compatibility of applications with the cloud and for determining the appropriate cloud resources.
- Hardware Inventory: Create a detailed inventory of the hardware resources used by each application. This includes servers, storage devices, network devices, and any specialized hardware. Capture information such as the manufacturer, model, CPU, memory, storage capacity, and network configuration.
- Software Inventory: Document the software components used by each application, including the operating system, middleware, databases, and any custom-built applications. Specify the version numbers and any relevant configuration details. This is crucial for compatibility assessments in the cloud environment.
- Network Configuration: Document the network configuration for each application, including IP addresses, subnets, firewalls, and network security groups. This information is necessary for replicating the network environment in the cloud and ensuring connectivity.
- Hosting Environment: Specify the current hosting environment for each application (e.g., on-premises data center, colocation facility, or a hybrid environment). Document the location, physical characteristics, and any relevant security considerations.
Capturing Application Performance Metrics
Tracking application performance metrics provides valuable insights into application behavior and resource utilization. This information is critical for identifying performance bottlenecks, optimizing application performance, and determining the appropriate cloud resources for each application. The following HTML table template can be used to capture and track these metrics.“`html
| Application Name | Metric | Value | Time Stamp |
|---|---|---|---|
| Application A | CPU Usage (%) | 65 | 2024-02-29 10:00:00 |
| Application A | Memory Consumption (GB) | 8 | 2024-02-29 10:00:00 |
| Application A | Latency (ms) | 150 | 2024-02-29 10:00:00 |
| Application B | CPU Usage (%) | 20 | 2024-02-29 10:00:00 |
| Application B | Memory Consumption (GB) | 4 | 2024-02-29 10:00:00 |
| Application B | Latency (ms) | 50 | 2024-02-29 10:00:00 |
“`This table provides a basic framework. The “Metric” column should include a list of critical performance indicators.
- CPU Usage: The percentage of CPU resources utilized by the application. High CPU usage can indicate a need for more compute resources.
- Memory Consumption: The amount of memory used by the application. Insufficient memory can lead to performance degradation and application crashes.
- Disk I/O: The rate at which the application reads from and writes to disk. High disk I/O can indicate a storage bottleneck.
- Network Throughput: The amount of data transferred over the network. High network throughput can indicate network congestion.
- Latency: The time it takes for the application to respond to a request. High latency can indicate performance issues.
- Error Rates: The rate at which the application encounters errors. High error rates can indicate problems with the application code or underlying infrastructure.
Defining Cloud Migration Goals and Objectives
Establishing clear goals and objectives is paramount for a successful cloud migration. Without a well-defined roadmap, the migration process can become inefficient, costly, and ultimately fail to deliver the expected business benefits. This section Artikels how to define these crucial elements, aligning them with overall business strategy and ensuring a measurable and achievable outcome.
Business Objectives Driving Cloud Migration
Cloud migration decisions are typically driven by a combination of business objectives. These objectives should be clearly articulated to guide the entire migration process and serve as benchmarks for measuring success.
- Cost Reduction: This is a frequently cited objective, aiming to decrease IT infrastructure expenses. This includes reducing capital expenditures (CapEx) associated with on-premises hardware and operational expenditures (OpEx) such as power, cooling, and IT staff. For example, companies often cite reductions of 20-30% in overall IT costs after migration, particularly when leveraging cloud-native services and optimizing resource utilization.
- Scalability and Elasticity: Cloud platforms provide the ability to scale resources up or down on demand, responding to fluctuating workloads. This elasticity allows businesses to avoid over-provisioning, optimize resource allocation, and handle peak loads effectively. Consider Netflix, which uses AWS to scale its video streaming services, handling massive traffic spikes during peak viewing hours without performance degradation.
- Improved Agility and Innovation: Cloud environments enable faster deployment cycles, rapid prototyping, and experimentation. This increased agility allows organizations to bring new products and services to market more quickly and respond more effectively to changing market demands. This is exemplified by companies like Spotify, which leverage the cloud’s agility to iterate quickly on its music streaming platform, adding new features and adapting to user feedback in real-time.
- Enhanced Business Continuity and Disaster Recovery: Cloud providers offer robust disaster recovery (DR) solutions, ensuring business operations can continue even in the event of an outage or disaster. This is achieved through geographically diverse data centers, automated failover mechanisms, and regular data backups. Many financial institutions, for instance, leverage cloud-based DR to ensure they meet stringent regulatory requirements for business continuity, maintaining service availability even in critical situations.
- Increased Security and Compliance: Cloud providers invest heavily in security measures, offering advanced security tools, and adhering to industry-specific compliance standards (e.g., HIPAA, GDPR). This can improve an organization’s security posture and simplify compliance efforts. Companies like Salesforce, operating within the cloud, demonstrate the ability to meet stringent security and compliance requirements through a combination of provider-managed security and customer-configured controls.
Framework for Defining SMART Goals
Defining specific, measurable, achievable, relevant, and time-bound (SMART) goals is crucial for a successful cloud migration. The SMART framework provides a structured approach to ensure goals are clearly defined and can be tracked effectively.
- Specific: Goals should be clearly defined, leaving no room for ambiguity. The scope of the goal should be well-defined, specifying exactly what needs to be achieved.
- Measurable: Goals must be quantifiable so progress can be tracked. This requires defining key performance indicators (KPIs) to measure success.
- Achievable: Goals should be realistic and attainable, considering available resources and constraints. Overly ambitious goals can lead to frustration and failure.
- Relevant: Goals should align with overall business objectives and contribute to the organization’s strategic priorities.
- Time-bound: Goals should have a defined timeframe for completion, creating a sense of urgency and providing a deadline for accountability.
For example, consider the objective of cost reduction. A SMART goal might be:
“Reduce IT infrastructure costs by 20% within 12 months by migrating the CRM application to a cloud-based platform, utilizing reserved instances and optimizing resource utilization.”
This goal is specific (migrate the CRM application), measurable (20% cost reduction), achievable (based on industry benchmarks), relevant (aligns with cost reduction objective), and time-bound (within 12 months). The measurement of cost reduction can be done by tracking the expenditure on the on-premise infrastructure and the cloud services before and after the migration.
Aligning Application Prioritization with Business Strategy
Application prioritization for cloud migration should be directly aligned with the overall business strategy. This ensures that the migration efforts contribute to the most important business goals and delivers maximum value.
- Identify Strategic Business Priorities: Begin by understanding the organization’s strategic goals. These might include market expansion, new product development, customer experience improvements, or operational efficiency gains.
- Assess Application Alignment: Evaluate how each application supports these strategic priorities. Identify applications that are critical to achieving the business goals.
- Prioritize Based on Strategic Value: Prioritize applications for migration based on their strategic importance. Applications that directly support key business objectives should be migrated first.
- Consider Technical Factors: While business value is the primary driver, also consider technical factors such as application complexity, dependencies, and cloud readiness. This will help in planning a migration strategy that is both strategically sound and technically feasible.
- Regularly Review and Adjust: The business strategy and priorities can evolve over time. Regularly review the application prioritization and adjust the migration plan accordingly to ensure alignment with the current strategic direction.
For example, if a company’s strategic priority is to improve customer experience, applications directly related to customer interactions (e.g., CRM, customer service platforms, e-commerce platforms) should be prioritized for migration. The benefits of migrating these applications first can be quickly realized, leading to immediate improvements in customer satisfaction and contributing directly to the company’s strategic goals. This also creates a positive momentum, as it generates early wins, which helps in gaining support and buy-in from various stakeholders.
Identifying Application Dependencies and Interrelationships
Understanding and meticulously mapping application dependencies is paramount for a successful cloud migration. This process mitigates the risk of service disruptions, data loss, and operational inefficiencies during and after the migration. A comprehensive dependency analysis allows for a phased migration approach, prioritizing applications based on their interdependencies and ensuring that critical services remain available throughout the transition. Neglecting this step can lead to cascading failures, significantly increasing the complexity and cost of the migration.
Mapping Application Dependencies to Avoid Disruption During Migration
Application dependency mapping is a crucial element in mitigating risks associated with cloud migration. It involves systematically identifying and documenting the relationships between applications, services, and infrastructure components. This process facilitates a structured approach to migration, minimizing downtime and ensuring service continuity.To effectively map dependencies, consider the following:
- Application Discovery: Begin by cataloging all applications within the existing IT landscape. This includes both internal and external-facing applications.
- Dependency Analysis: Investigate the communication pathways between applications. Determine which applications rely on others, including data flows, API calls, and shared resources.
- Component Identification: Identify the underlying components supporting each application, such as databases, servers, and network infrastructure.
- Impact Assessment: Evaluate the potential impact of migrating each application. Determine the consequences of downtime or migration failures on dependent applications.
- Migration Grouping: Group applications based on their dependencies to define migration sequences. Prioritize migrations to minimize disruption.
- Testing and Validation: Thoroughly test each migration step, verifying the functionality and data integrity of migrated applications.
- Documentation: Maintain comprehensive documentation of application dependencies, migration plans, and testing results.
By implementing these steps, organizations can reduce the likelihood of unforeseen issues, such as service outages, during cloud migration. The methodical mapping of dependencies enables informed decision-making and minimizes potential disruptions.
Visualizing Application Interdependencies Using a Diagram
Visual representation of application interdependencies is essential for effectively communicating and understanding complex relationships. Diagrams provide a clear and concise overview of the entire application landscape, allowing stakeholders to quickly grasp the impact of migration decisions. A well-designed diagram enhances collaboration and aids in the development of effective migration strategies.A common technique for visualizing interdependencies involves creating a dependency graph.
This graph typically uses nodes to represent applications and edges to depict the relationships between them. The characteristics of a dependency graph are as follows:
- Nodes: Each node in the graph represents an application or service. The nodes can be labeled with application names, version numbers, or other relevant information.
- Edges: Edges, or lines, connect the nodes and represent the dependencies between applications. The direction of the edge indicates the direction of the dependency. For example, an edge from application A to application B signifies that application A depends on application B.
- Edge Attributes: Attributes can be added to the edges to provide additional information about the dependency, such as the type of communication (e.g., API call, database query), the frequency of communication, and the data volume.
- Color-Coding: Color-coding can be used to categorize applications based on their criticality, business function, or migration priority.
- Layout: The layout of the graph should be clear and easy to understand. Techniques such as hierarchical layouts or force-directed layouts can be used to visualize complex relationships.
A practical example could be a diagram depicting an e-commerce platform. This diagram might show the web application depending on a database, an order processing service, and a payment gateway. The database might depend on a caching service for performance. Different colors could indicate applications ready for migration (green), those in progress (yellow), and those that are not yet migrated (red).
This visual representation provides a clear understanding of the entire system and allows for an efficient and phased migration strategy.
Procedure for Identifying and Documenting Communication Pathways Between Applications
Establishing a systematic procedure for identifying and documenting communication pathways between applications is fundamental to a successful cloud migration. A detailed understanding of these pathways allows for the creation of a well-defined migration strategy, ensuring that all dependencies are accounted for and that the migration process proceeds smoothly. This process reduces the risk of data loss, service disruptions, and operational inefficiencies.The procedure includes several key steps:
- Inventory Collection: Compile a comprehensive inventory of all applications within the existing IT infrastructure. Include application names, versions, and a brief description of their purpose.
- Communication Analysis: Analyze the communication patterns between applications. This can involve several methods:
- Network Traffic Analysis: Use network monitoring tools to identify the communication between applications, including protocols, ports, and data volumes.
- Log Analysis: Examine application logs to identify inter-application calls and data exchanges.
- Code Review: Review application source code to identify hardcoded dependencies and communication endpoints.
- Application Performance Monitoring (APM): Utilize APM tools to track application interactions and identify dependencies.
- Dependency Mapping: Document the identified dependencies in a dependency matrix or graph. The matrix should list all applications and indicate the communication pathways between them.
- Communication Pathway Details: For each communication pathway, document:
- Protocol: The communication protocol used (e.g., HTTP, TCP, UDP).
- Port: The port number used for communication.
- Data Format: The format of the data exchanged (e.g., JSON, XML).
- Data Volume: The average and peak data volume transmitted.
- Frequency: The frequency of communication.
- Security Considerations: Security protocols used for communication.
- Documentation and Maintenance: Maintain up-to-date documentation of all dependencies and communication pathways. This documentation should be regularly reviewed and updated as applications evolve.
By following this procedure, organizations can create a comprehensive map of application dependencies, enabling them to develop effective migration strategies, reduce risks, and ensure a smooth transition to the cloud.
Evaluating Application Suitability for Cloud Migration
The evaluation of application suitability for cloud migration is a critical step in any cloud adoption strategy. This process determines which applications are best suited for migration, the most appropriate migration approach for each, and ultimately, helps organizations maximize the benefits of cloud computing while minimizing risks and costs. This section delves into the various cloud migration strategies, their respective advantages and disadvantages, and provides a decision-making framework to guide the selection process.
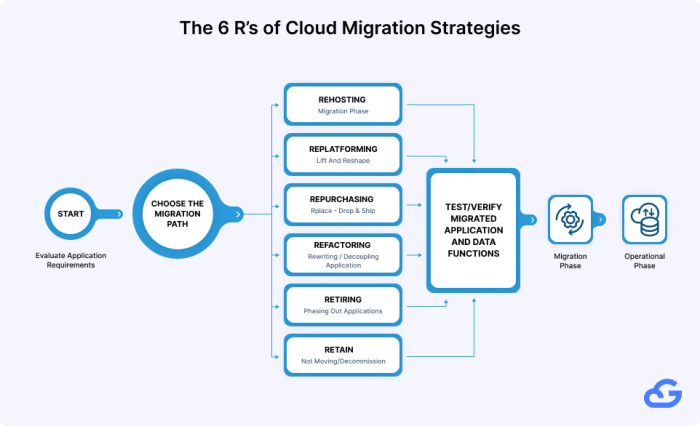
Cloud Migration Strategies
Choosing the right cloud migration strategy is paramount to a successful transition. Different applications have different characteristics and requirements, and therefore, require tailored approaches. Several key strategies exist, each with its own implications for cost, effort, and potential benefits.
- Rehosting (Lift and Shift): Rehosting involves migrating an application “as is” to the cloud without making any changes to the application’s code or architecture. This strategy is typically the fastest and least expensive approach, making it suitable for applications that are relatively straightforward and have minimal dependencies.
- Re-platforming (Lift, Tinker, and Shift): Re-platforming entails making some changes to the application to take advantage of cloud-native features. This might involve changing the database or using a different operating system. While more complex than rehosting, re-platforming can improve performance and scalability.
- Refactoring (Re-architecting): Refactoring involves redesigning and rewriting the application to fully leverage cloud-native services and architectures. This is the most complex and time-consuming strategy, but it offers the greatest potential for optimizing performance, scalability, and cost efficiency.
- Repurchase (Replace): Repurchasing involves replacing the existing application with a software-as-a-service (SaaS) solution. This strategy is suitable for applications where a suitable SaaS alternative exists and can meet the organization’s needs.
- Retire: Retiring an application involves decommissioning it entirely. This strategy is applicable to applications that are no longer needed or are underutilized.
Pros and Cons of Each Cloud Migration Strategy
Each migration strategy presents a unique set of advantages and disadvantages that must be carefully considered during the evaluation process. A thorough understanding of these trade-offs is essential for making informed decisions.
- Rehosting (Lift and Shift):
- Pros: Fastest migration time, lowest initial cost, minimal disruption to the application.
- Cons: May not fully leverage cloud benefits, potential for increased operational costs if the application is not optimized for the cloud, may not be suitable for all application types.
- Re-platforming (Lift, Tinker, and Shift):
- Pros: Improved performance and scalability, moderate migration time and cost, leverages some cloud-native features.
- Cons: Requires some code modifications, potential for compatibility issues, increased complexity compared to rehosting.
- Refactoring (Re-architecting):
- Pros: Maximizes cloud benefits (scalability, performance, cost optimization), leverages cloud-native services, highly adaptable and flexible.
- Cons: Most complex and time-consuming, highest initial cost, requires significant development effort and expertise.
- Repurchase (Replace):
- Pros: Reduced IT burden, access to the latest features and updates, potentially lower total cost of ownership (TCO).
- Cons: May require significant changes to business processes, potential vendor lock-in, may not fully meet all customization needs.
- Retire:
- Pros: Simplifies IT infrastructure, reduces costs, eliminates maintenance overhead.
- Cons: Requires careful assessment of application usage and dependencies, may impact business processes if the application is critical.
Decision Tree for Cloud Migration Strategy Selection
A decision tree provides a structured approach to determine the most suitable migration strategy for a given application. The following factors are considered in this decision-making process.
- Application Architecture: Is the application monolithic or microservices-based? Monolithic applications are often best suited for rehosting or re-platforming initially, while microservices-based applications can be more easily refactored.
- Application Dependencies: What are the dependencies of the application? Applications with complex dependencies may require more effort to migrate.
- Business Requirements: What are the business requirements for the application? Is high availability, scalability, and cost optimization critical? These factors will influence the choice of migration strategy.
- Cost and Time Constraints: What are the budget and time constraints for the migration? Rehosting is typically the fastest and least expensive option, while refactoring is the most time-consuming and costly.
- Technical Expertise: What technical expertise is available within the organization? Refactoring requires significant development skills, while rehosting requires less specialized knowledge.
Based on the answers to these questions, a decision tree can guide the selection of the appropriate migration strategy. For example:
- If the application is monolithic, has few dependencies, and the business prioritizes speed and cost, rehosting might be the best option.
- If the application is modular, requires high scalability, and the business is willing to invest in the long-term benefits, refactoring could be a better choice.
- If a suitable SaaS alternative is available and meets the business requirements, then repurchase might be considered.
Here is a simplified representation of a decision tree structure:
Question Answer Strategy Is the application monolithic? Yes Rehosting/Re-platforming Is the application monolithic? No Refactoring Is a SaaS alternative available? Yes Repurchase Is the application utilized? No Retire
The decision tree approach provides a systematic way to evaluate application suitability and select the optimal cloud migration strategy, aligning technical considerations with business goals and constraints.
Assessing Technical Feasibility and Complexity
Evaluating the technical feasibility and complexity is crucial for successful cloud migration. This assessment identifies potential technical challenges, compatibility issues, and the effort required to move applications to the cloud. A thorough evaluation minimizes risks, informs migration strategy, and provides a realistic understanding of the resources needed.
Assessing Technical Challenges Associated with Application Migration
Migrating applications involves addressing a variety of technical hurdles. These challenges vary based on application architecture, dependencies, and the chosen cloud platform. A systematic approach is essential to accurately gauge the effort involved.
- Application Architecture Analysis: Evaluate the application’s design and how it’s built. This includes understanding its components, dependencies, and how they interact. Monolithic applications often present different challenges than microservices-based architectures.
- Example: A monolithic application may require significant refactoring to be cloud-native, while microservices can be migrated more easily.
- Dependency Mapping: Identify all internal and external dependencies. This includes databases, middleware, APIs, and other services the application relies on. Understanding these dependencies is crucial for ensuring functionality post-migration.
- Example: An application dependent on an on-premises database will require a strategy for database migration or integration with a cloud-based database service.
- Platform Compatibility: Determine the application’s compatibility with the chosen cloud platform’s operating systems, programming languages, and frameworks. Compatibility gaps may necessitate code modifications or platform-specific adaptations.
- Example: An application written in .NET Framework might require significant changes to run on a Linux-based cloud environment.
- Network Requirements: Analyze the network requirements of the application, including bandwidth, latency, and security considerations. Cloud migration necessitates ensuring adequate network connectivity and security configurations.
- Example: Applications requiring low-latency access might need to be deployed in regions closer to the end-users.
- Security and Compliance: Assess the application’s security posture and compliance requirements. This involves evaluating data encryption, access controls, and compliance with industry regulations (e.g., GDPR, HIPAA).
- Example: Applications handling sensitive data will require robust security measures, including encryption at rest and in transit.
- Data Migration Strategy: Plan the strategy for migrating data to the cloud. This includes choosing the right data migration tools and methods (e.g., online, offline, or hybrid approaches).
- Example: Large datasets may require offline migration methods to minimize downtime and data transfer costs.
- Testing and Validation: Define the testing strategy to validate the application’s functionality, performance, and security after migration. Comprehensive testing is critical to ensure a smooth transition.
- Example: Performance testing will be necessary to ensure the application performs adequately in the cloud environment.
Creating a Checklist for Evaluating Application Compatibility
A structured checklist helps assess an application’s compatibility with the cloud platform. This checklist ensures a consistent and thorough evaluation process.
- Operating System Compatibility: Verify if the application’s operating system is supported by the cloud platform.
- Check: Is the OS supported? Are there specific versions required?
- Programming Language and Framework Support: Ensure the cloud platform supports the application’s programming language and frameworks.
- Check: Are the language and framework versions supported?
- Database Compatibility: Determine if the application’s database is compatible with cloud-based database services.
- Check: Is the database compatible? Are there migration options available?
- Middleware and Library Compatibility: Assess the compatibility of middleware components and third-party libraries.
- Check: Are middleware components and libraries compatible or replaceable?
- API and Integration Compatibility: Evaluate the compatibility of APIs and integrations with other systems.
- Check: Are APIs and integrations compatible with the cloud platform’s services?
- Security Requirements: Assess if the application’s security requirements can be met on the cloud platform.
- Check: Are security features such as encryption, access controls, and identity management supported?
- Performance Requirements: Verify that the cloud platform can meet the application’s performance requirements.
- Check: Does the platform offer adequate resources for performance?
- Cost Considerations: Evaluate the potential costs associated with running the application on the cloud platform.
- Check: Is the cost structure feasible? Are there cost optimization strategies?
Sharing Examples of Common Technical Roadblocks and Addressing Strategies
Cloud migration often presents several technical roadblocks. Understanding these challenges and their solutions is essential for a successful migration.
- Database Migration Challenges: Migrating databases can be complex, especially for large databases or those with specific compatibility issues.
- Roadblock: Incompatible database versions or proprietary database features.
- Solution: Use database migration tools, convert proprietary features, or consider a database-as-a-service (DBaaS) offering on the cloud.
- Network Configuration Issues: Ensuring seamless network connectivity and security can be challenging.
- Roadblock: Incorrect network configurations, firewall restrictions, or latency issues.
- Solution: Implement proper network segmentation, configure firewalls, and optimize network settings. Use cloud-specific networking services.
- Application Code Incompatibility: Code written for on-premises environments may not be compatible with the cloud platform.
- Roadblock: Hard-coded file paths, reliance on specific libraries, or incompatible dependencies.
- Solution: Refactor the code, update dependencies, and use cloud-native services.
- Security and Compliance Concerns: Meeting security and compliance requirements can be challenging.
- Roadblock: Data encryption, access control, and regulatory compliance.
- Solution: Implement encryption, use identity and access management (IAM) services, and follow industry best practices.
- Integration Challenges: Integrating with other systems or services can be difficult.
- Roadblock: Incompatible APIs or lack of cloud-based alternatives.
- Solution: Use API gateways, implement service meshes, or consider integration-as-a-service (iPaaS) platforms.
- Performance Bottlenecks: Applications may experience performance issues after migration.
- Roadblock: Inadequate resources, inefficient code, or network latency.
- Solution: Optimize code, scale resources, and use caching mechanisms. Conduct performance testing.
Determining Business Value and Prioritization Criteria
Prioritizing applications for cloud migration is a critical step, ensuring resources are allocated effectively and maximizing the return on investment. This involves quantifying the business value of each application, assessing technical feasibility, and considering associated risks. A structured approach, incorporating a scoring system and ROI calculations, allows for informed decision-making and a strategic migration plan.
Quantifying Business Value of Application Migration
The business value of migrating an application to the cloud can be quantified using several metrics, encompassing both cost savings and revenue generation. Analyzing these factors provides a comprehensive understanding of the potential benefits.
- Potential Cost Savings: Cloud migration often leads to significant cost reductions. These savings can be derived from various sources:
- Infrastructure Costs: Reduced spending on hardware, data center space, and power consumption.
- Operational Costs: Decreased IT staff requirements for maintenance, patching, and upgrades.
- Licensing Costs: Leveraging pay-as-you-go models or cloud-based software-as-a-service (SaaS) offerings.
For example, a retail company migrating its e-commerce platform to the cloud could potentially reduce its infrastructure costs by 30% annually and decrease IT operational expenses by 20%.
- Revenue Generation: Cloud migration can also contribute to increased revenue through:
- Improved Application Performance: Faster response times and higher availability can enhance user experience and increase sales.
- New Feature Deployment: Cloud platforms offer access to advanced services, such as machine learning and data analytics, enabling the development of new features and services that drive revenue.
- Scalability and Agility: The ability to quickly scale resources can accommodate peak demand and support business growth.
Consider a financial services company migrating its trading platform to the cloud. The improved performance and scalability could lead to a 5% increase in trading volume and a corresponding rise in revenue.
- Risk Mitigation: While not directly generating revenue, risk mitigation adds value by reducing potential losses.
- Disaster Recovery: Cloud-based disaster recovery solutions provide better business continuity.
- Security Enhancements: Cloud providers often offer robust security measures.
For example, a healthcare provider migrating its patient data management system to the cloud benefits from enhanced data security and improved disaster recovery capabilities, reducing the risk of data breaches and service disruptions.
Scoring System for Application Prioritization
A scoring system helps prioritize applications based on a combination of factors. This system assigns weights to different criteria and calculates a total score for each application.
- Factors and Weights: Define the factors to be considered and assign weights to reflect their relative importance. Example factors and weights:
- Business Value (40%): Measured by potential cost savings, revenue generation, and risk mitigation.
- Technical Feasibility (30%): Assessed based on application architecture, complexity, and compatibility with cloud platforms.
- Risk (30%): Evaluated based on the potential impact of migration failures, data security concerns, and compliance requirements.
- Scoring Methodology: For each factor, create a scoring scale (e.g., 1-5, where 1 is the lowest and 5 is the highest). Evaluate each application against the defined criteria and assign a score.
- Business Value Score: Assess each application’s potential cost savings, revenue generation, and risk mitigation benefits.
- Technical Feasibility Score: Evaluate the application’s architecture, complexity, and compatibility with cloud platforms.
- Risk Score: Assess the potential impact of migration failures, data security concerns, and compliance requirements.
- Total Score Calculation: Calculate the total score for each application by multiplying each factor’s score by its weight and summing the results.
Total Score = (Business Value Score
- 0.4) + (Technical Feasibility Score
- 0.3) + (Risk Score
- 0.3)
Applications with higher total scores should be prioritized for migration.
- Example:
Application Business Value Score Technical Feasibility Score Risk Score Total Score Priority E-commerce Platform 5 4 3 4.2 High Customer Relationship Management (CRM) 4 3 4 3.6 Medium Legacy Accounting System 2 2 5 3.3 Low
Calculating Return on Investment (ROI) for Application Migration
Calculating the ROI for each application migration provides a financial justification for the project and helps in prioritizing applications.
- Cost Estimation: Estimate the total cost of the migration, including:
- Migration Costs: Costs associated with the migration process, such as professional services, tools, and training.
- Cloud Infrastructure Costs: Costs for cloud resources, including compute, storage, and networking.
- Operational Costs: Ongoing costs for managing and maintaining the application in the cloud.
- Benefit Estimation: Estimate the total benefits of the migration, including:
- Cost Savings: Quantify the expected cost reductions in infrastructure, operations, and licensing.
- Revenue Generation: Estimate the potential increase in revenue due to improved performance, new features, or increased scalability.
- ROI Calculation: Calculate the ROI using the following formula:
ROI = ((Total Benefits – Total Costs) / Total Costs) – 100
A positive ROI indicates that the migration is expected to generate a return on investment. The higher the ROI, the more financially attractive the migration is.
- Example:
- Application: E-commerce Platform
- Total Migration Costs: $100,000
- Annual Cost Savings: $50,000
- Annual Revenue Increase: $25,000
- Total Annual Benefits: $75,000
- ROI: (($75,000 – $100,000) / $100,000)
– 100 = -25%
In this example, the ROI is negative, indicating that the migration is not financially viable in the short term. Further analysis may be required to identify ways to reduce costs or increase benefits.
- Application: Customer Relationship Management (CRM)
- Total Migration Costs: $75,000
- Annual Cost Savings: $20,000
- Annual Revenue Increase: $10,000
- Total Annual Benefits: $30,000
- ROI: (($30,000 – $75,000) / $75,000)
– 100 = -60%
In this example, the ROI is negative, indicating that the migration is not financially viable in the short term. Further analysis may be required to identify ways to reduce costs or increase benefits.
- Application: Legacy Accounting System
- Total Migration Costs: $50,000
- Annual Cost Savings: $15,000
- Annual Revenue Increase: $0
- Total Annual Benefits: $15,000
- ROI: (($15,000 – $50,000) / $50,000)
– 100 = -70%
In this example, the ROI is negative, indicating that the migration is not financially viable in the short term. Further analysis may be required to identify ways to reduce costs or increase benefits.
Risk Assessment and Mitigation Strategies
Cloud migration, while offering significant advantages, introduces potential risks that must be carefully evaluated and addressed. A proactive approach to risk assessment and mitigation is crucial for a successful and secure cloud transition. This involves identifying potential threats, assessing their likelihood and impact, and developing strategies to minimize their negative consequences. This section Artikels the key steps involved in this process, providing practical examples and actionable strategies.
Identifying and Assessing Risks
Identifying and assessing risks is the foundation of a robust cloud migration strategy. This process involves a systematic examination of potential vulnerabilities and threats that could impact the migration process and the ongoing operation of applications in the cloud.
- Data Security Risks: Data security is a paramount concern. Potential risks include data breaches, unauthorized access, data loss, and data corruption. These risks can arise from various sources, including misconfigured cloud services, vulnerabilities in applications, and malicious attacks. Assessing these risks requires understanding the sensitivity of the data, the existing security controls, and the security features offered by the chosen cloud provider.
- Compliance Risks: Compliance with industry regulations and legal requirements is crucial, especially for organizations operating in regulated industries such as finance or healthcare. Failure to comply can result in significant penalties and legal liabilities. Risks include non-compliance with data privacy regulations (e.g., GDPR, CCPA), industry-specific regulations (e.g., HIPAA), and internal policies. A thorough assessment involves mapping applications and data to relevant compliance requirements and verifying that the cloud environment meets these requirements.
- Downtime Risks: Downtime, or the unavailability of applications and services, can have significant financial and operational impacts. Risks include outages caused by infrastructure failures, network disruptions, software bugs, and human error. Assessing downtime risks involves evaluating the criticality of each application, the existing redundancy and failover mechanisms, and the service level agreements (SLAs) provided by the cloud provider.
- Vendor Lock-in Risks: Vendor lock-in refers to the difficulty of migrating applications and data from one cloud provider to another. This can limit flexibility, increase costs, and reduce negotiating power. Risks include proprietary technologies, complex migration processes, and high egress fees. Assessing these risks involves evaluating the portability of applications, the availability of open standards, and the cost implications of migrating to a different provider.
- Performance Risks: Poor application performance can negatively impact user experience and business productivity. Risks include latency issues, insufficient resources, and inefficient application design. Assessing performance risks involves analyzing application performance metrics, simulating workload demands, and optimizing application configurations for the cloud environment.
- Cost Risks: Unexpected or excessive cloud costs can erode the financial benefits of cloud migration. Risks include cost overruns, inefficient resource utilization, and unexpected charges. Assessing cost risks involves carefully estimating cloud costs, monitoring resource consumption, and implementing cost optimization strategies.
- Operational Risks: Cloud migration can introduce new operational challenges, such as the need for new skills, changes to existing processes, and increased complexity. Risks include skills gaps, process inefficiencies, and integration challenges. Assessing operational risks involves evaluating the organization’s readiness for cloud operations, identifying training needs, and developing new operational procedures.
Creating a Risk Mitigation Plan
A comprehensive risk mitigation plan is essential for addressing the identified risks and ensuring a successful cloud migration. The plan should Artikel specific mitigation strategies, assign responsibilities, and establish timelines for implementation.
- Prioritization: Risks should be prioritized based on their likelihood and impact. High-priority risks require immediate attention and more comprehensive mitigation strategies.
- Ownership: Assigning ownership for each risk ensures accountability and facilitates effective risk management.
- Documentation: The risk mitigation plan should be documented clearly and concisely, including risk descriptions, mitigation strategies, responsible parties, and timelines.
- Monitoring: Regularly monitor the effectiveness of mitigation strategies and update the plan as needed.
Examples of Risk Mitigation Strategies
The following examples illustrate various risk mitigation strategies, grouped by the type of risk they address:
Data Security Risks:
- Data Encryption: Implement encryption for data at rest and in transit using strong encryption algorithms (e.g., AES-256).
- Access Control: Implement robust access controls, including multi-factor authentication (MFA), role-based access control (RBAC), and the principle of least privilege.
- Data Loss Prevention (DLP): Deploy DLP solutions to monitor and prevent sensitive data from leaving the cloud environment.
- Regular Security Audits: Conduct regular security audits and penetration testing to identify and address vulnerabilities.
Compliance Risks:
- Compliance Assessments: Conduct thorough compliance assessments to identify gaps and ensure adherence to relevant regulations.
- Data Residency: Choose cloud regions that meet data residency requirements.
- Data Masking and Anonymization: Implement data masking and anonymization techniques to protect sensitive data.
- Compliance Monitoring Tools: Utilize compliance monitoring tools to track compliance status and generate reports.
Downtime Risks:
- High Availability Architecture: Design applications with high availability architectures, including redundancy, failover mechanisms, and automatic scaling.
- Disaster Recovery (DR) Planning: Develop and test a comprehensive DR plan to ensure business continuity in the event of an outage.
- Service Level Agreements (SLAs): Leverage SLAs with cloud providers to guarantee uptime and define service level objectives.
- Regular Testing: Conduct regular testing of failover mechanisms and DR plans to ensure their effectiveness.
Vendor Lock-in Risks:
- Multi-Cloud Strategy: Adopt a multi-cloud strategy to reduce dependence on a single provider.
- Open Standards: Utilize open standards and technologies to enhance portability.
- Containerization: Employ containerization technologies (e.g., Docker, Kubernetes) to improve application portability.
- Regular Code Reviews: Perform code reviews to prevent vendor-specific lock-in.
Performance Risks:
- Performance Testing: Conduct performance testing and load testing to identify and address performance bottlenecks.
- Auto-Scaling: Implement auto-scaling to automatically adjust resources based on demand.
- Caching: Utilize caching mechanisms to improve application performance.
- Content Delivery Networks (CDNs): Leverage CDNs to distribute content closer to users.
Cost Risks:
- Cost Optimization Tools: Utilize cost optimization tools to monitor and manage cloud spending.
- Reserved Instances/Savings Plans: Leverage reserved instances or savings plans to reduce costs.
- Right-Sizing Resources: Right-size resources to ensure efficient utilization and avoid overspending.
- Regular Cost Analysis: Conduct regular cost analysis to identify areas for improvement.
Operational Risks:
- Training and Skill Development: Provide training and skill development programs to equip staff with the necessary cloud skills.
- Automation: Automate operational tasks to reduce manual effort and improve efficiency.
- Change Management: Implement a robust change management process to manage changes to the cloud environment.
- Monitoring and Alerting: Implement comprehensive monitoring and alerting systems to proactively identify and address operational issues.
Creating a Prioritization Matrix
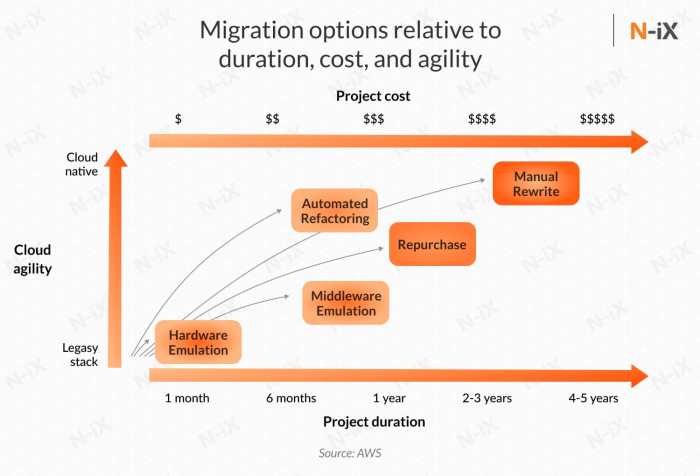
The creation of a prioritization matrix is a crucial step in streamlining the cloud migration process. This matrix provides a visual representation of the applications based on key criteria, enabling a systematic and data-driven approach to determining the migration order. By plotting applications within this framework, organizations can make informed decisions, optimize resource allocation, and minimize risks.
Design of a Four-Quadrant Prioritization Matrix
The prioritization matrix typically utilizes a four-quadrant model, leveraging two primary dimensions: business value and technical complexity. This approach allows for a clear categorization of applications and facilitates informed decision-making. The matrix is structured as follows:
- Business Value (Vertical Axis): This axis represents the value the application provides to the business. It can be assessed based on factors like revenue generation, cost savings, strategic importance, and impact on customer experience. Applications with high business value are positioned towards the top of the matrix, while those with lower value are placed towards the bottom.
- Technical Complexity (Horizontal Axis): This axis reflects the difficulty of migrating an application to the cloud. Complexity is determined by factors such as the application’s architecture, dependencies, integration with other systems, and the need for refactoring or re-architecting. Applications with high technical complexity are placed on the right side of the matrix, and those with lower complexity are positioned on the left.
- The Four Quadrants: The intersection of these axes creates four distinct quadrants, each representing a different priority level for migration:
- Quadrant 1: Quick Wins (High Business Value, Low Technical Complexity): Applications in this quadrant offer the greatest return on investment (ROI) with the least effort. They are prime candidates for early migration.
- Quadrant 2: Strategic Migrations (High Business Value, High Technical Complexity): These applications are critical to the business but require more complex migration strategies. They should be prioritized after the quick wins.
- Quadrant 3: Re-architect or Retain (Low Business Value, High Technical Complexity): Applications in this quadrant are the most challenging to migrate and offer limited business value. Options include re-architecting for the cloud, or, if not feasible, retaining them on-premises or sunsetting them.
- Quadrant 4: Low-Hanging Fruit (Low Business Value, Low Technical Complexity): These applications are relatively easy to migrate but offer minimal business impact. They can be migrated later, or potentially retired.
Guide on Populating the Matrix with Application Data
Populating the prioritization matrix requires a structured approach, involving the assessment of each application against the defined criteria of business value and technical complexity. This process ensures objectivity and data-driven decision-making.
- Data Collection: Gather relevant data for each application. This includes information from previous steps, such as the application assessment, dependency mapping, and business value analysis. Document all the application information in a spreadsheet.
- Business Value Scoring: Define a scoring system for business value. This could involve assigning points based on factors like revenue contribution, cost savings potential, and strategic importance. For example:
- Revenue Contribution: Assign points based on the percentage of total revenue generated by the application.
- Cost Savings Potential: Estimate the potential cost savings from migrating the application to the cloud (e.g., infrastructure costs, maintenance costs).
- Strategic Importance: Assess the application’s alignment with business strategy and goals.
- Technical Complexity Scoring: Develop a scoring system for technical complexity. This should consider factors such as:
- Application Architecture: Evaluate the application’s architecture (e.g., monolithic, microservices).
- Dependencies: Identify and assess the number and complexity of application dependencies.
- Integration Requirements: Assess the complexity of integrating the application with other systems.
- Refactoring Needs: Determine the extent of refactoring required for cloud compatibility.
- Scoring Applications: Evaluate each application against the business value and technical complexity criteria, using the defined scoring systems. Record the scores for each application.
- Matrix Placement: Plot each application on the matrix based on its business value and technical complexity scores. This visually represents the relative priority of each application for cloud migration.
Demonstrating the Use of the Matrix for Migration Order Determination
The prioritization matrix directly informs the order in which applications should be migrated. The quadrant in which an application falls dictates its priority. The goal is to maximize ROI and minimize risk.
- Identify Quick Wins (Quadrant 1): Start by migrating applications in the “Quick Wins” quadrant. These applications offer the fastest path to value and can help build momentum for the migration project. Example: a simple web application with low dependencies.
- Prioritize Strategic Migrations (Quadrant 2): After addressing the quick wins, focus on applications in the “Strategic Migrations” quadrant. These applications are critical to the business, but the migration will be more complex and time-consuming. Plan the migration in phases and consider using a phased approach to minimize risk. Example: a core business application with complex dependencies.
- Evaluate Re-architect or Retain (Quadrant 3): For applications in the “Re-architect or Retain” quadrant, carefully evaluate the options. Consider whether re-architecting for the cloud is feasible and cost-effective. If not, explore alternative solutions, such as retaining the application on-premises or potentially retiring it.
- Consider Low-Hanging Fruit (Quadrant 4): Migrate applications in the “Low-Hanging Fruit” quadrant after addressing the higher-priority applications. These applications can be migrated relatively easily but offer limited business impact. Example: a non-critical internal tool with few dependencies.
- Iterative Refinement: The prioritization matrix is not static. As the migration project progresses, reassess the applications and adjust the matrix as needed. New information or changing business priorities may require modifications to the migration order.
The prioritization matrix provides a structured, visual framework for managing the cloud migration process. By systematically assessing applications based on business value and technical complexity, organizations can make informed decisions, optimize resource allocation, and maximize the return on their cloud investments.
Developing a Migration Roadmap and Timeline
Developing a comprehensive migration roadmap and timeline is critical for a successful cloud migration. This phase translates the strategic prioritization into actionable steps, providing a structured approach to manage the complexities of the migration process. It defines the sequence of activities, allocates resources, and sets realistic expectations for stakeholders. A well-defined roadmap minimizes risks, facilitates effective communication, and ensures the project stays on track.
Creating a Sample Migration Roadmap
A migration roadmap Artikels the phases, tasks, and timelines required to move applications to the cloud. It serves as a strategic blueprint, guiding the migration efforts from initial planning to final deployment and optimization.The following is a sample migration roadmap with illustrative phases and timelines:
- Phase 1: Assessment and Planning (4-6 weeks)
This initial phase focuses on detailed assessment, defining migration strategies, and creating a comprehensive migration plan. It involves thorough evaluation of the current application portfolio, identifying dependencies, and selecting the appropriate cloud migration approach for each application.
- Application Portfolio Analysis and Prioritization
- Cloud Platform Selection (e.g., AWS, Azure, Google Cloud)
- Migration Strategy Definition (Rehost, Replatform, Refactor, etc.)
- Resource Allocation and Budgeting
- Risk Assessment and Mitigation Planning
- Phase 2: Pilot Migration (6-8 weeks)
The pilot migration phase involves migrating a small subset of applications to the cloud. This allows the team to test the migration processes, identify potential challenges, and refine the migration strategy before proceeding with the full-scale migration. It provides valuable learning opportunities and mitigates risks.
- Selection of Pilot Applications
- Environment Setup in the Cloud
- Migration of Pilot Applications
- Testing and Validation
- Performance Monitoring and Optimization
- Phase 3: Migration Execution (Varies – several months to years)
This is the core phase of the migration, involving the migration of the remaining applications based on the defined priorities and strategies. It requires careful coordination, continuous monitoring, and proactive problem-solving to ensure a smooth transition.
- Application-Specific Migration Execution (based on prioritized list)
- Data Migration and Synchronization
- Testing and Quality Assurance
- User Acceptance Testing (UAT)
- Cutover and Go-Live
- Phase 4: Optimization and Management (Ongoing)
This phase focuses on optimizing the migrated applications for the cloud environment and managing the cloud infrastructure. It involves continuous monitoring, performance tuning, cost optimization, and security enhancements.
- Performance Monitoring and Tuning
- Cost Optimization and Management
- Security Hardening and Compliance
- Disaster Recovery and Business Continuity Planning
- Ongoing Management and Maintenance
Creating a Gantt Chart for Visualization
A Gantt chart is a visual project management tool that effectively displays the project timeline, tasks, and dependencies. It facilitates understanding the project’s progress and identifying potential bottlenecks. Creating a Gantt chart is crucial for visualizing the migration project timeline and tracking progress.To create a Gantt chart, consider the following steps:
- List Tasks: Break down the migration project into specific tasks and subtasks. These tasks should align with the phases Artikeld in the migration roadmap.
- Estimate Duration: Estimate the time required to complete each task. Consider factors such as application complexity, team experience, and resource availability.
- Define Dependencies: Identify dependencies between tasks. Some tasks may need to be completed before others can begin.
- Assign Resources: Assign resources (e.g., personnel, tools) to each task.
- Create the Chart: Use project management software (e.g., Microsoft Project, Asana, Trello) or spreadsheet software (e.g., Microsoft Excel, Google Sheets) to create the Gantt chart. Enter the tasks, durations, dependencies, and resource assignments.
- Track Progress: Regularly update the Gantt chart to reflect the project’s progress. This allows you to identify delays and adjust the schedule as needed.
A sample Gantt chart might include:* A horizontal timeline representing the project duration.
- Rows representing individual tasks.
- Bars representing the duration of each task, starting and ending on the timeline.
- Dependencies shown by connecting lines between tasks.
- Milestones marking important checkpoints.
- Resource allocation information.
Providing a Template for Tracking Progress and Managing Dependencies
Effective progress tracking and dependency management are essential for a successful cloud migration. A structured template facilitates monitoring the project’s status, identifying risks, and making informed decisions.A comprehensive template should include the following elements:
- Task ID: A unique identifier for each task.
- Task Name: A descriptive name for the task.
- Start Date: The planned start date for the task.
- End Date: The planned end date for the task.
- Assigned Resource(s): The person(s) or team responsible for the task.
- Status: The current status of the task (e.g., Not Started, In Progress, Completed, Blocked).
- Dependencies: The tasks that must be completed before this task can begin.
- Progress (%): The percentage of the task completed.
- Comments/Notes: Any relevant notes or comments about the task.
- Risks/Issues: Identified risks or issues affecting the task.
- Mitigation Plan: The plan to address identified risks or issues.
This template can be implemented using spreadsheets or project management software. Regular updates to the template provide a clear view of the project’s progress, identify potential problems early, and enable timely corrective actions. For instance, if a task’s status is “Blocked” due to a dependency not being completed, the template highlights the need to address the blocking task immediately. If a task’s progress is significantly behind schedule, the template triggers a review of the task’s resource allocation and timeline.
Cost Estimation and Budgeting
Accurately estimating and budgeting for cloud migration is crucial for financial planning and successful project execution. A comprehensive cost analysis considers various factors, from initial migration expenses to ongoing operational costs. This section provides a detailed approach to cost estimation, budgeting, and cost optimization strategies for a cloud environment.
Estimating Cloud Migration Costs
Estimating the total cost of cloud migration involves a multi-faceted approach, encompassing both upfront and recurring expenses. These costs can be categorized to facilitate a more organized and precise estimation process.
- Migration Tools and Services: These costs relate to the software and services used for data transfer, application refactoring, and cloud infrastructure setup.
- Assessment Tools: Tools that analyze the existing on-premises environment to determine application dependencies, resource utilization, and cloud suitability. Example: Cloudamize, which provides a detailed assessment report of the IT environment, identifying migration strategies and associated costs.
- Data Migration Tools: Services for transferring data from on-premises to the cloud. Example: AWS DataSync, Azure Data Box, and Google Cloud Storage Transfer Service. The costs depend on the volume of data, transfer speed, and storage fees.
- Refactoring Tools: Tools that assist in modifying applications for the cloud environment. Example: AWS Application Migration Service (MGN) can be used to automatically convert and migrate applications.
- Cloud Services: The cost of utilizing cloud resources such as compute instances, storage, databases, and networking.
- Compute: Costs associated with virtual machines (VMs), containers, and serverless functions. The pricing model often depends on the instance size, operating system, and duration of use.
- Storage: The costs for storing data, including object storage, block storage, and file storage. Pricing varies based on storage class (e.g., standard, infrequent access, archive), data volume, and data access frequency.
- Databases: The cost of database services, including managed database instances and database-as-a-service (DBaaS) offerings. Costs are based on instance size, storage, and database type.
- Networking: Costs associated with data transfer, virtual private networks (VPNs), and other network services. Pricing varies based on data transfer volume and network configuration.
- Ongoing Operations: Costs related to maintaining and managing the cloud environment after migration.
- Operational Support: Costs of managing the cloud environment, including monitoring, security, and maintenance.
- Monitoring and Logging: Costs associated with monitoring and logging tools to track application performance, resource utilization, and security events. Example: Splunk, Datadog, and Prometheus.
- Security: The cost of security services, including firewalls, intrusion detection systems, and identity and access management (IAM) solutions.
- Training and Staffing: Costs related to training the IT staff on cloud technologies and potentially hiring new personnel with cloud expertise.
- Training: Costs of providing training courses and certifications to the IT staff to ensure they can manage and maintain the cloud environment.
- Staffing: The cost of hiring cloud architects, engineers, and administrators.
- Other Expenses: These are additional costs associated with cloud migration.
- Testing: Costs associated with testing applications in the cloud environment.
- Consulting: The cost of hiring consultants to assist with the migration process.
Creating a Budget for Cloud Migration
Creating a detailed budget is essential for managing the financial aspects of cloud migration. The budget should encompass all the cost components identified during the estimation phase.
- Cost Breakdown: Categorize all costs into distinct areas, such as migration tools, cloud services, and ongoing operations. This detailed breakdown enables accurate tracking and control of spending.
- Timeframe: Define the budget timeframe. The budget should align with the migration roadmap and timeline, considering both the short-term and long-term costs.
- Contingency Planning: Allocate a contingency fund to address unexpected expenses. It is recommended to include a contingency of 10-20% of the total budget to account for unforeseen issues or changes.
- Cost Tracking and Reporting: Implement a system to track actual costs against the budget. This can be done using spreadsheets, project management software, or cloud-specific cost management tools. Regularly generate reports to monitor spending and identify any deviations from the budget.
- Budget Review: Review and adjust the budget periodically, especially during the initial phases of migration, to accommodate any changes in scope, resource requirements, or pricing.
Cost Optimization Strategies for the Cloud Environment
Cost optimization is a continuous process that aims to minimize cloud spending while maximizing the value derived from cloud resources. The following strategies can help in achieving cost efficiency:
- Right-Sizing Resources: Ensure that compute instances and other cloud resources are appropriately sized to meet the actual workload demands.
- Monitoring: Monitor resource utilization and adjust instance sizes accordingly. Underutilized resources lead to unnecessary costs.
- Automation: Use automation tools to automatically scale resources up or down based on demand.
- Reserved Instances and Savings Plans: Utilize reserved instances and savings plans to reduce the cost of compute resources. These options offer significant discounts compared to on-demand pricing for long-term resource commitments.
- Reserved Instances: Reserved instances offer significant discounts for committed usage over a specific period.
- Savings Plans: Savings plans provide flexible pricing models, allowing organizations to commit to a specific spending level in exchange for discounts.
- Storage Optimization: Optimize storage costs by selecting the appropriate storage tier based on data access frequency and retention requirements.
- Tiering: Use different storage tiers (e.g., standard, infrequent access, archive) to store data based on access frequency.
- Data Lifecycle Management: Implement data lifecycle policies to automatically move data between storage tiers based on its age and access patterns.
- Automated Scaling: Implement auto-scaling to automatically adjust the number of compute instances based on demand. This ensures that resources are available when needed while minimizing costs during periods of low demand.
- Horizontal Scaling: Add or remove instances to meet fluctuating demands.
- Vertical Scaling: Adjust the size of instances.
- Cost Monitoring and Reporting: Use cloud-specific cost management tools to monitor and analyze spending patterns. Regularly review cost reports to identify areas for optimization.
- Cost Management Tools: Leverage cloud provider’s cost management tools, such as AWS Cost Explorer, Azure Cost Management, and Google Cloud Billing.
- Alerts: Set up alerts to notify of any unexpected spending or deviations from the budget.
- Deleting Unused Resources: Regularly identify and remove unused resources, such as idle instances, unused storage volumes, and orphaned network resources.
- Resource Tagging: Tag resources to identify and track their usage and associated costs.
- Automation: Automate the process of identifying and deleting unused resources.
- Leveraging Spot Instances: Use spot instances for workloads that are fault-tolerant and can withstand interruptions. Spot instances offer significant discounts compared to on-demand instances, but they can be terminated with short notice if the spot price exceeds the bid price.
- Implementing a FinOps Culture: Foster a culture of financial accountability and transparency within the organization. This involves educating teams on cloud costs, promoting cost-conscious decision-making, and establishing clear ownership of cloud spending.
Communication and Stakeholder Management
Effective communication and proactive stakeholder management are crucial for the successful migration of applications to the cloud. A well-defined communication strategy ensures transparency, builds trust, and facilitates collaboration among all involved parties. This, in turn, mitigates risks, manages expectations, and fosters a smooth transition process.
Sharing a Communication Plan to Keep Stakeholders Informed Throughout the Migration Process
A comprehensive communication plan provides a structured framework for disseminating information to stakeholders throughout the cloud migration lifecycle. It should clearly define the target audience, communication frequency, communication channels, and the specific information to be shared at each stage.
- Target Audience Identification: The communication plan must identify all stakeholders, including executive leadership, IT teams, business units, security teams, and any external vendors or partners involved. Each group may require different levels of detail and frequency of updates.
- Communication Frequency and Channels: Establish a regular communication cadence, such as weekly status reports, monthly steering committee meetings, and ad-hoc communications for critical events. Utilize appropriate channels like email, project management software, intranet portals, and in-person meetings.
- Information to be Shared: The plan should specify the type of information to be shared at each stage, including project timelines, progress updates, identified risks and mitigation strategies, resource allocation, budget status, and any decisions requiring stakeholder input.
- Roles and Responsibilities: Clearly define the individuals responsible for creating, distributing, and managing communication materials. This ensures accountability and consistency in messaging.
- Feedback Mechanisms: Implement mechanisms for stakeholders to provide feedback and raise concerns, such as surveys, Q&A sessions, or dedicated communication channels.
Detailing How to Manage Stakeholder Expectations and Address Concerns
Managing stakeholder expectations and addressing concerns proactively is critical for maintaining support and minimizing resistance to change. This involves transparency, responsiveness, and a commitment to addressing issues promptly.
- Setting Realistic Expectations: Be transparent about the challenges and potential delays associated with cloud migration. Avoid overpromising or setting unrealistic timelines. Provide realistic estimates based on thorough assessments.
- Proactive Communication: Regularly communicate progress, challenges, and risks to stakeholders. Address potential issues before they escalate.
- Active Listening and Feedback Incorporation: Actively listen to stakeholder concerns and feedback. Incorporate their input into the project plan where feasible. Show stakeholders that their opinions are valued.
- Issue Resolution and Escalation: Establish a clear process for addressing and resolving issues. Escalate critical issues to the appropriate decision-makers promptly.
- Change Management: Implement change management strategies to help stakeholders adapt to the new cloud environment. This includes providing training, documentation, and support.
Providing Examples of Communication Materials, Such as Presentations and Reports
Various communication materials can be used to keep stakeholders informed and engaged throughout the cloud migration process. These materials should be tailored to the specific audience and the stage of the project.
- Executive Summary Presentations: High-level presentations for executive leadership summarizing project progress, key milestones, budget status, and risks. These presentations should be concise and focus on strategic implications.
- Detailed Status Reports: Comprehensive reports providing a detailed overview of project activities, including completed tasks, upcoming milestones, resource utilization, and any issues encountered. These reports should be distributed regularly to project teams and relevant stakeholders.
- Technical Deep Dives: Technical presentations and documentation for IT teams, covering architectural designs, implementation details, and troubleshooting guides. These should be tailored for technical audiences.
- Risk Assessment Reports: Reports identifying potential risks associated with the cloud migration and outlining mitigation strategies. These reports should be shared with stakeholders to promote transparency and encourage proactive risk management.
- Change Management Communication: Materials such as training manuals, FAQs, and communication campaigns designed to inform users about changes and provide guidance on how to adapt to the new cloud environment.
- Example: Consider a cloud migration project where the initial assessment phase revealed a dependency on a legacy application. This dependency presented a potential risk, and it was communicated via a risk assessment report. The report detailed the impact of the dependency, possible mitigation strategies (such as refactoring the application), and the estimated timeline for resolution. This report, shared with the project team and stakeholders, allowed for proactive planning and management of expectations.
End of Discussion
In conclusion, effectively prioritizing applications for cloud migration is not merely a technical exercise; it’s a strategic imperative. By systematically evaluating applications based on business value, technical feasibility, and risk, organizations can create a well-defined roadmap. This approach facilitates a phased migration, maximizing the benefits of cloud adoption while minimizing potential disruptions. The methodologies presented provide a framework for informed decision-making, ensuring a successful and optimized cloud transformation.
Top FAQs
What is the primary benefit of prioritizing applications for cloud migration?
Prioritization enables a phased approach, reducing risk, optimizing resource allocation, and accelerating the realization of cloud benefits, such as cost savings and improved agility.
How do you determine the business value of an application for cloud migration?
Business value is determined by assessing potential cost savings, revenue generation opportunities, improved operational efficiency, and alignment with strategic business objectives.
What are the common cloud migration strategies?
Common strategies include rehosting (lift and shift), re-platforming, refactoring, repurchase, and retirement, each with its own set of advantages and disadvantages.
How does technical feasibility impact application prioritization?
Technical feasibility assesses the complexity of migrating an application, considering factors like compatibility with the cloud platform, required code modifications, and the availability of necessary tools and expertise.
What is a prioritization matrix, and how is it used?
A prioritization matrix, typically based on business value and technical complexity, visually represents applications and helps determine the optimal migration order.