In the intricate landscape of modern microservices, where applications communicate extensively, ensuring secure and reliable service-to-service interactions is paramount. This is where mutual Transport Layer Security (mTLS) steps in, offering a robust solution to protect sensitive data and maintain trust within your infrastructure. mTLS provides a powerful method for authenticating and encrypting communication between services, ensuring that only authorized entities can access and exchange information.
This guide explores the core principles of mTLS, its inner workings, and the benefits it brings to the table. We will delve into how mTLS functions, from certificate management to secure handshake processes. We’ll also examine various implementation methods, common challenges, and best practices to help you effectively integrate mTLS into your service-to-service communication strategy. Whether you’re a seasoned developer or just starting your journey into secure communication, this resource aims to provide a comprehensive understanding of mTLS and its vital role in securing your services.
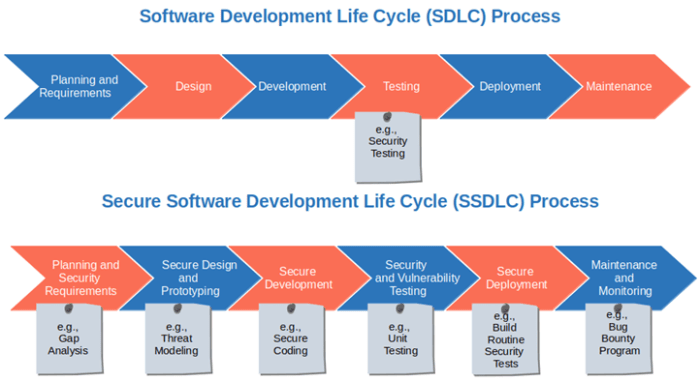
Introduction to mTLS for Service-to-Service Communication
Mutual Transport Layer Security (mTLS) is a critical security protocol designed to authenticate and encrypt communication between services, particularly in modern distributed architectures like microservices. It extends the standard TLS protocol by requiring both the client and the server to authenticate themselves using digital certificates. This two-way authentication significantly enhances security, ensuring that only authorized services can communicate with each other.mTLS plays a vital role in establishing trust and securing sensitive data exchanged between services, forming a cornerstone of robust and secure service-to-service communication.
Definition of mTLS
mTLS, or Mutual Transport Layer Security, is a security protocol that provides a secure channel for communication between two endpoints, typically a client and a server. It goes beyond the standard TLS by requiring both the client and the server to present digital certificates for authentication.The core components of mTLS include:
- Digital Certificates: These are electronic documents used to verify the identity of the communicating parties. They are issued by a trusted Certificate Authority (CA) or can be self-signed in certain environments. Each certificate contains information about the entity it represents, such as its name, public key, and the CA that issued it.
- Authentication: mTLS involves two-way authentication. The client presents its certificate to the server, and the server validates it. Similarly, the server presents its certificate to the client, which also validates it. This ensures that both parties are who they claim to be.
- Encryption: Once both parties have authenticated, the communication channel is encrypted using symmetric encryption keys. These keys are negotiated during the TLS handshake and are used to encrypt and decrypt the data transmitted between the client and server, ensuring confidentiality.
Problem mTLS Solves in Microservices Architectures
Microservices architectures, with their distributed nature and numerous services communicating with each other, present unique security challenges. Traditional security measures, such as network firewalls, are often insufficient to protect the internal communication between these services.mTLS addresses these challenges by:
- Securing Internal Communication: mTLS provides a robust mechanism for securing the communication between microservices, ensuring that only authorized services can communicate with each other, even within the same network.
- Preventing Man-in-the-Middle Attacks: By requiring mutual authentication, mTLS prevents man-in-the-middle attacks, where an attacker intercepts and potentially modifies the communication between two services.
- Enhancing Trust and Authentication: mTLS establishes a strong foundation of trust between services by verifying their identities through digital certificates. This is particularly important in environments where sensitive data is exchanged.
- Improving Compliance: Implementing mTLS helps organizations meet regulatory compliance requirements that mandate secure communication and data protection.
- Simplifying Security Management: Centralized certificate management and automated certificate rotation, which are often part of mTLS implementations, streamline security management and reduce the risk of security breaches due to expired or compromised certificates.
How mTLS Works
Mutual TLS (mTLS) ensures secure service-to-service communication by verifying the identities of both the client and the server. This is achieved through the use of digital certificates and a carefully orchestrated handshake process. Understanding the technical underpinnings of mTLS is crucial for implementing and maintaining a robust and secure network.
Mutual Authentication Using Digital Certificates
mTLS leverages digital certificates to authenticate both the client and the server. These certificates act as digital identities, containing information about the entity they represent, such as the service name, domain, and public key.The process of mutual authentication unfolds as follows:
- Certificate Presentation: Both the client and the server present their digital certificates to each other during the TLS handshake. The server presents its certificate to the client, and the client presents its certificate to the server.
- Verification of Certificate: Each party verifies the other’s certificate to ensure its authenticity and validity. This involves checking the certificate’s signature, expiration date, and revocation status.
- Identity Confirmation: If the certificates are valid, the identities of both parties are confirmed, establishing a basis for a trusted connection.
This two-way authentication significantly enhances security compared to traditional TLS, where only the server is typically authenticated.
Role of a Certificate Authority (CA)
A Certificate Authority (CA) is a trusted entity that issues and validates digital certificates. CAs play a vital role in establishing trust within the mTLS ecosystem.The functions of a CA include:
- Issuing Certificates: The CA verifies the identity of the entity requesting a certificate and, if the verification is successful, issues a digital certificate to that entity. This certificate binds the entity’s identity to its public key.
- Certificate Validation: The CA maintains a Certificate Revocation List (CRL) and uses other mechanisms to validate the status of certificates. This ensures that only valid and trusted certificates are used.
- Establishing Trust: By trusting a CA, you implicitly trust the certificates issued by that CA. This trust is typically established by including the CA’s root certificate in a trusted store on the client and server.
The CA’s role is critical because it acts as a trusted third party, verifying the identity of entities and enabling secure communication.
Handshake Process in mTLS
The mTLS handshake is a sequence of steps that establish a secure connection between the client and the server. This process involves the exchange of certificates, the negotiation of encryption algorithms, and the establishment of encryption keys.The handshake process can be summarized as follows:
- Client Hello: The client initiates the handshake by sending a “Client Hello” message to the server. This message includes the client’s supported TLS versions, cipher suites, and a random number.
- Server Hello: The server responds with a “Server Hello” message, selecting a TLS version and cipher suite supported by both the client and the server. The server also sends its certificate to the client.
- Certificate Exchange (Server): The server sends its digital certificate to the client, enabling the client to verify the server’s identity.
- Certificate Exchange (Client – mTLS): In mTLS, the client sends its digital certificate to the server, enabling the server to verify the client’s identity.
- Server Key Exchange (Optional): The server may send a “Server Key Exchange” message, depending on the chosen cipher suite. This message provides the server’s public key and other necessary parameters.
- Client Key Exchange: The client generates a pre-master secret and encrypts it with the server’s public key (obtained from the server’s certificate). The client sends the encrypted pre-master secret to the server.
- Certificate Verify (Client – mTLS): The client may send a “Certificate Verify” message, signed with its private key, to prove it possesses the private key associated with its certificate. This is an extra layer of security to prove the client’s ownership of its certificate.
- Change Cipher Spec: Both the client and the server send a “Change Cipher Spec” message, indicating that they are switching to the encrypted mode.
- Finished: The client and the server send “Finished” messages, which are encrypted using the newly established keys. These messages verify that the handshake was successful and that both parties can communicate securely.
The entire process culminates in a secure, encrypted communication channel between the client and the server.
Diagram of mTLS Handshake Process
The following diagram illustrates the mTLS handshake process:
Visual Representation Description:
The diagram illustrates a sequence of steps between a client and a server. It is structured as a timeline with arrows representing the flow of messages.
1. Client Hello: The client initiates the process by sending a “Client Hello” message to the server. This message includes information like supported TLS versions and cipher suites.
2. Server Hello, Certificate (Server), Server Key Exchange (Optional), Server Hello Done: The server responds with a “Server Hello” message, including the selected TLS version and cipher suite. It also sends its digital certificate. An optional Server Key Exchange message may follow, and the server then signals the end of its initial messages with “Server Hello Done.”
3. Certificate (Client): The client then sends its digital certificate to the server. This is a key step in mutual authentication.
4. Client Key Exchange: The client sends the “Client Key Exchange” message, which contains information used to generate the session keys.
5. Certificate Verify (Client – mTLS): The client may optionally send a “Certificate Verify” message, signed with its private key.
6. Change Cipher Spec: Both client and server independently send a “Change Cipher Spec” message, indicating they are switching to the encrypted mode.
7. Finished: Both the client and the server send “Finished” messages, confirming the successful completion of the handshake and that secure communication can begin.
The arrows are labeled with the message names, indicating the direction and content of each exchange. The diagram visually represents the chronological order and the specific messages exchanged to establish a secure mTLS connection.
Benefits of Implementing mTLS
Implementing mTLS offers significant advantages in securing service-to-service communication. It enhances security posture, improves data protection, and builds a stronger foundation of trust within an organization’s infrastructure. This approach provides a robust method for authenticating and encrypting communication, leading to a more resilient and secure system.
Security Advantages Over Other Authentication Methods
mTLS surpasses simpler authentication methods like API keys or basic authentication in several key areas. These advantages stem from its reliance on cryptographic certificates, which provide a more secure and verifiable means of verifying identities.
- Enhanced Authentication: mTLS uses client-side certificates for authentication, making it significantly harder for attackers to impersonate services. Unlike password-based systems that are vulnerable to credential stuffing or phishing attacks, mTLS requires possession of a valid certificate, which is more difficult to compromise.
- Improved Key Management: The use of certificates allows for more sophisticated key management practices. Certificates can be easily revoked if compromised, and the certificate authority (CA) can quickly issue new certificates, minimizing the impact of a security breach.
- Protection Against Man-in-the-Middle (MitM) Attacks: mTLS protects against MitM attacks because the client verifies the server’s certificate, and the server verifies the client’s certificate. This mutual verification ensures that both parties are communicating with the intended endpoints, preventing attackers from intercepting and decrypting data in transit.
- Increased Trust and Verification: The certificate authority (CA) validates the identity of the services. This third-party validation enhances trust and provides assurance that the communicating parties are legitimate.
Enhanced Security and Data Protection
mTLS contributes to robust security and data protection through encryption and identity verification. This combination ensures data confidentiality and integrity, minimizing the risk of data breaches.
- Data Encryption in Transit: mTLS leverages TLS encryption to secure data transmitted between services. This encryption protects sensitive information from unauthorized access during transit, ensuring confidentiality.
- Data Integrity: TLS includes mechanisms to ensure data integrity, preventing data tampering. Any modification to the data during transit will be detected, protecting the accuracy and reliability of the information exchanged.
- Stronger Identity Verification: By using client certificates, mTLS verifies the identity of each service. This prevents unauthorized services from accessing protected resources and ensures that only trusted services can communicate.
- Reduced Attack Surface: By requiring certificates, mTLS reduces the attack surface. Attackers cannot easily gain access without a valid certificate, making it more difficult to exploit vulnerabilities.
Improved Trust and Reduced Risk of Unauthorized Access
mTLS fosters trust and reduces the risk of unauthorized access within a service-oriented architecture. This is achieved through rigorous authentication and authorization mechanisms.
- Verified Service Identity: mTLS verifies the identity of each service involved in communication. This ensures that only authorized services can access resources, preventing unauthorized access.
- Reduced Risk of Lateral Movement: By requiring certificates for all communication, mTLS limits the ability of an attacker to move laterally within a network. Even if one service is compromised, the attacker cannot easily access other services without a valid certificate.
- Improved Compliance: mTLS helps organizations meet compliance requirements related to data security and privacy. The encryption and authentication provided by mTLS support adherence to regulations such as GDPR, HIPAA, and PCI DSS.
- Simplified Auditing: mTLS simplifies auditing by providing a clear record of service-to-service communication. Audit logs can track which services are communicating, when they are communicating, and what data is being exchanged, improving visibility and accountability.
mTLS Implementation Methods and Procedures
Implementing mutual TLS (mTLS) requires careful planning and execution. The method chosen depends on the architecture of the services, existing infrastructure, and security requirements. Selecting the right approach is crucial for successfully securing service-to-service communication.There are several approaches to implementing mTLS, each with its own set of advantages and disadvantages. Understanding these different methods allows for informed decision-making when designing and deploying mTLS.
mTLS Implementation Approaches
Several approaches can be employed to integrate mTLS into a service-to-service communication framework. These methods offer varying degrees of complexity, control, and integration effort.
- Service Mesh: Service meshes, such as Istio and Linkerd, provide a dedicated infrastructure layer for handling service-to-service communication. They automatically handle mTLS encryption, certificate management, and policy enforcement. This approach simplifies mTLS implementation and offers centralized control.
- API Gateways: API gateways can act as intermediaries, terminating TLS connections from clients and establishing mTLS connections to backend services. This method provides a centralized point for managing security policies and authentication, including mTLS.
- Direct Integration: In this approach, mTLS is implemented directly within the application code. This involves configuring the application to use TLS certificates for authentication and encryption. This method offers fine-grained control but can be more complex to manage and maintain, especially in larger deployments.
- Sidecar Proxy: This method involves deploying a sidecar proxy alongside each service instance. The sidecar proxy handles mTLS encryption and decryption, while the application communicates with the proxy locally. This approach can be used with various service architectures.
Configuring mTLS in a Service Mesh (Istio or Linkerd)
Service meshes like Istio and Linkerd simplify the implementation of mTLS. They automate much of the process, reducing the complexity of configuring and managing certificates and encryption. The configuration steps differ slightly between Istio and Linkerd, but the underlying principles are similar.
- Deploying the Service Mesh: The first step is to install and configure the chosen service mesh, such as Istio or Linkerd, within the Kubernetes cluster or the target environment. This typically involves installing the control plane components and injecting the sidecar proxies into the application pods.
- Enabling mTLS Globally (Istio): In Istio, you can enable mTLS globally for all services within the mesh. This is typically done by applying a `PeerAuthentication` resource with a `mode` set to `STRICT`. This forces all services to use mTLS for communication.
- Enabling mTLS Globally (Linkerd): Linkerd enables mTLS by default. When a service is injected with the Linkerd proxy, it automatically starts using mTLS for communication with other services in the mesh. No specific configuration is typically needed to enable mTLS in Linkerd.
- Configuring TLS Certificates: The service mesh handles the generation and distribution of TLS certificates. The control plane automatically issues certificates to the sidecar proxies. This simplifies certificate management and rotation.
- Verifying mTLS: After enabling mTLS, it is crucial to verify that communication between services is indeed encrypted. This can be done by examining the logs of the services or by using the service mesh’s monitoring tools.
- Fine-tuning Policies: Both Istio and Linkerd allow you to fine-tune mTLS policies. You can define which services require mTLS, which certificates are trusted, and other security-related configurations. This allows for granular control over service communication.
Generating and Managing Certificates
Certificate management is a critical aspect of mTLS. Securely generating, distributing, and rotating certificates is essential to maintaining a secure environment.
- Choosing a Certificate Authority (CA): Decide on a Certificate Authority (CA). This can be a public CA, a private CA, or the service mesh’s built-in CA. The CA is responsible for issuing and signing the certificates.
- Generating Certificate Signing Requests (CSRs): Services typically generate Certificate Signing Requests (CSRs). These CSRs contain information about the service and are used to request a certificate from the CA.
- Issuing Certificates: The CA validates the CSRs and issues corresponding certificates. The certificates are then provided to the services.
- Distributing Certificates: The certificates need to be securely distributed to the services. Service meshes automate this process by injecting certificates into the sidecar proxies.
- Rotating Certificates: Certificates have an expiration date. It is important to rotate certificates periodically to maintain security. Service meshes automate certificate rotation.
- Revoking Certificates: If a certificate is compromised, it must be revoked. This prevents the compromised certificate from being used for unauthorized access.
Comparison of mTLS Implementation Methods
Each mTLS implementation method has its own set of pros and cons, influencing the decision-making process. The table below provides a comparison of the different approaches.
| Implementation Method | Pros | Cons | Use Cases |
|---|---|---|---|
| Service Mesh | Simplified mTLS configuration, centralized control, automated certificate management, policy enforcement. | Increased complexity of initial setup, overhead of sidecar proxies, potential performance impact. | Large-scale microservices architectures, complex service-to-service communication patterns. |
| API Gateway | Centralized security policy management, simplifies client-side configuration, integrates with existing infrastructure. | Single point of failure, potential performance bottleneck, increased latency. | Exposing services to external clients, securing APIs, managing authentication and authorization. |
| Direct Integration | Fine-grained control, no external dependencies, can be optimized for specific services. | Increased development effort, complex certificate management, difficult to scale. | Small-scale deployments, services with specific security requirements, when other methods are not feasible. |
| Sidecar Proxy | Decouples security from application code, supports various service architectures, improved security. | Increased resource consumption, complexity in managing sidecar deployments, potential for operational overhead. | Architectures requiring a clear separation of concerns, when the application code is not easily modified. |
Common Challenges and Troubleshooting mTLS
Implementing mutual TLS (mTLS) can significantly enhance the security of service-to-service communication. However, it also introduces complexities that require careful planning and proactive troubleshooting. This section Artikels common challenges encountered during mTLS implementation and provides guidance on addressing them.
Certificate Management Challenges
Managing certificates is a central aspect of mTLS, and several challenges can arise. The proper handling of certificates is crucial for maintaining a secure and functional mTLS environment.
- Certificate Generation and Issuance: Generating and issuing certificates, especially for a large number of services, can be complex. Organizations need robust Certificate Authorities (CAs) and processes to ensure the validity and trustworthiness of certificates. Automating certificate issuance and renewal is often necessary to avoid manual errors and ensure timely updates.
- Certificate Storage and Security: Securely storing private keys is paramount. Compromised keys can lead to unauthorized access and data breaches. Solutions like hardware security modules (HSMs) or secure key management systems are essential for protecting private keys.
- Certificate Revocation: Handling certificate revocation is critical in case of key compromise or other security incidents. Implementing a robust Certificate Revocation List (CRL) or Online Certificate Status Protocol (OCSP) infrastructure allows for the timely revocation of compromised certificates.
- Certificate Renewal: Certificates have expiration dates, and failure to renew them can disrupt service communication. Automating the renewal process and monitoring certificate expiration dates are essential to prevent outages.
Key Rotation Challenges
Regular key rotation is a security best practice, but it can be challenging to implement in an mTLS environment. Proper key rotation ensures that even if a key is compromised, its impact is limited.
- Coordination Across Services: Coordinating key rotation across multiple services requires careful planning and execution. All services must be updated with the new certificate and key pair before the old ones are revoked.
- Downtime and Service Interruptions: Key rotation can potentially lead to downtime or service interruptions if not handled carefully. Implementing a phased rollout and providing mechanisms for graceful degradation is crucial.
- Compatibility Issues: Ensure that all services and clients support the cryptographic algorithms and key lengths used in the new certificates. Older systems might require updates or configuration changes to maintain compatibility.
Compatibility Issues
mTLS implementation can expose compatibility issues between services. These issues can manifest in various ways, disrupting communication and requiring troubleshooting.
- Protocol Support: Ensure that all services support the required TLS versions and cipher suites. Older services might require upgrades or configuration changes to support modern TLS protocols.
- Cipher Suite Mismatches: Mismatched cipher suites can prevent services from establishing a secure connection. Ensure that all services use compatible cipher suites.
- Firewall and Network Configuration: Firewalls and network configurations must allow traffic on the required ports for mTLS communication. Misconfigured firewalls can block mTLS traffic.
- Client Library Compatibility: Ensure that client libraries used by services support mTLS and are correctly configured to use the appropriate certificates and keys.
Troubleshooting Connection Failures
Connection failures are common during mTLS implementation. Identifying and resolving these issues requires a systematic approach.
- Certificate Validation Errors: Verify that certificates are valid, not expired, and issued by a trusted CA. Check the certificate chain and ensure that the root CA is trusted by all communicating parties.
- Hostname Verification Issues: Ensure that the hostname in the certificate matches the hostname used by the service. Incorrect hostname verification can lead to connection failures.
- Cipher Suite Negotiation Failures: Analyze the TLS handshake logs to identify cipher suite negotiation failures. Ensure that services support compatible cipher suites.
- Network Connectivity Problems: Verify network connectivity between services. Check for firewall rules that might be blocking mTLS traffic. Use network diagnostic tools like `ping`, `traceroute`, and `tcpdump` to identify connectivity issues.
- Client Configuration Errors: Review the client-side configuration to ensure that the correct certificates and keys are being used. Verify that the client is configured to present its certificate to the server.
Monitoring and Logging mTLS Connections
Effective monitoring and logging are crucial for detecting and addressing potential problems in an mTLS environment. This allows for proactive issue identification and resolution.
- Enable TLS Handshake Logging: Enable detailed TLS handshake logging on both the client and server sides. This will provide valuable information about connection attempts, certificate validation, and cipher suite negotiation.
- Monitor Certificate Expiration Dates: Implement monitoring to track certificate expiration dates and proactively renew certificates before they expire. Set up alerts to notify administrators of upcoming expirations.
- Collect and Analyze Logs: Centralize logs from all services and analyze them for errors, warnings, and suspicious activity. Use log aggregation tools to facilitate analysis.
- Implement Metrics and Dashboards: Create metrics and dashboards to monitor the health and performance of mTLS connections. Track metrics such as connection success rates, error rates, and latency.
- Use Security Information and Event Management (SIEM) Systems: Integrate mTLS logs with a SIEM system to correlate events, detect security threats, and generate alerts.
mTLS vs. Other Security Protocols
Choosing the right security protocol is crucial for protecting service-to-service communication. Understanding the differences between mTLS and other security measures, such as TLS/HTTPS, API keys, and OAuth, allows for informed decisions about which method best suits specific security requirements and use cases. This section compares mTLS with alternative security protocols, outlining their strengths, weaknesses, and ideal applications.
mTLS Compared to TLS and HTTPS
TLS (Transport Layer Security) and its more common implementation, HTTPS (HTTP Secure), are widely used for securing communication between a client and a server. While mTLS builds upon TLS, there are key distinctions in how they operate and the level of security they provide.TLS/HTTPS, in its standard configuration, typically authenticates the server to the client. The client verifies the server’s identity using a certificate issued by a trusted Certificate Authority (CA).
The communication is then encrypted, protecting data in transit from eavesdropping and tampering. However, the client’s identity is not always verified, making the system vulnerable to impersonation attacks where a malicious actor could potentially masquerade as a legitimate client.mTLS, on the other hand, provides mutual authentication. Both the client and the server present certificates to each other, verifying their identities.
This ensures that both parties are who they claim to be before any data exchange occurs.Here’s a comparison table:
| Feature | TLS/HTTPS | mTLS |
|---|---|---|
| Authentication | Server-side only (typically) | Mutual (client and server) |
| Client Identity Verification | Often not verified; relies on IP addresses or headers | Verified via client-side certificates |
| Security Level | Protects data in transit; prevents eavesdropping | Provides stronger security; prevents impersonation attacks |
| Complexity | Relatively simpler to implement | More complex to implement and manage |
| Use Cases | Securing web browsing, protecting data transmission | Securing service-to-service communication, API access control, and high-security environments |
In essence, while TLS/HTTPS focuses on securing the communication channel, mTLS provides a more robust authentication mechanism, ensuring that only authorized parties can communicate. This is especially crucial in environments where the identity of the client is as important as the confidentiality of the data. For example, in a financial services application, where sensitive transactions occur between microservices, mTLS is a superior choice due to the mutual authentication capabilities.
mTLS Compared to API Keys and OAuth
API keys and OAuth are alternative authentication methods commonly used for securing API access. Each method offers different security profiles and is suitable for different scenarios.API keys are simple, unique identifiers that clients include in their API requests. The server validates the API key to grant access. While straightforward to implement, API keys are vulnerable to several risks. If compromised, an attacker gains complete access to the associated resources.
They also don’t provide granular control over access permissions or support for complex authorization flows.OAuth (Open Authorization) is a more sophisticated protocol that allows a client to access resources on behalf of a user without sharing the user’s credentials. It involves a process of authorization, where the user grants the client permission to access their data. OAuth supports delegation and provides a more secure way to manage access to resources.Here’s a comparison table:
| Feature | API Keys | OAuth | mTLS |
|---|---|---|---|
| Authentication Method | Unique, secret string | Delegated access through authorization grants | Client and server certificates |
| Security Level | Lower; vulnerable to key compromise | Higher; provides delegated access and supports granular permissions | Highest; mutual authentication, prevents impersonation |
| Complexity | Simple to implement | More complex to implement and manage | More complex to implement and manage |
| Granular Access Control | Limited | Supports fine-grained permissions | Supports fine-grained permissions via certificate-based authorization |
| Use Cases | Simple API access control; less sensitive data | Accessing user data on behalf of the user; third-party integrations | Securing service-to-service communication, highly sensitive environments |
mTLS provides the strongest security posture. By verifying the identity of both the client and the server through certificates, it mitigates risks associated with key compromise or unauthorized access. While API keys are suitable for basic access control, and OAuth is designed for delegated access, mTLS excels in securing internal service communication, particularly where the integrity and authenticity of both the sender and receiver are critical.
When mTLS is the Preferred Choice
mTLS is the preferred choice in scenarios where the highest level of security is required for service-to-service communication. This typically includes the following:
- High-Security Environments: In industries like finance, healthcare, and government, where data breaches can have severe consequences, mTLS provides a robust security layer to protect sensitive data and transactions.
- Internal Service Communication: Within a microservices architecture, where services need to communicate securely and reliably, mTLS ensures that only authorized services can access each other. This prevents unauthorized access and helps maintain the integrity of the system.
- API Access Control: When securing APIs that handle sensitive data, mTLS can be used to authenticate client applications, preventing unauthorized access and data breaches.
- Compliance Requirements: In regulated industries, compliance mandates may require the use of mTLS to meet specific security standards and regulations.
- Preventing Impersonation Attacks: mTLS prevents attackers from impersonating legitimate clients or services, a critical security feature in environments where trust is paramount.
Consider a financial institution using a microservices architecture to process transactions. Each service (e.g., order processing, payment gateway, fraud detection) needs to communicate securely. If a malicious actor were to compromise a service, they could potentially access sensitive financial data. With mTLS, the institution can ensure that only authorized services can communicate, even if one service is compromised. The certificates verify the identities of both services, preventing unauthorized access and protecting the integrity of the entire system.
mTLS and Service Mesh Architectures
Service meshes and mTLS are a powerful combination for securing microservices communication. A service mesh simplifies the complexities of implementing and managing mTLS, making it easier to secure traffic within a distributed application environment. This section explores the synergy between mTLS and service meshes, highlighting the benefits and operational advantages they provide.
Role of Service Meshes in Simplifying and Automating mTLS Implementation
Service meshes are designed to manage the complexities of microservices communication, and mTLS is a key component of that. They act as a dedicated infrastructure layer, providing features that simplify and automate the implementation of mTLS across a distributed application.
Handling Certificate Management, Key Rotation, and Traffic Encryption for mTLS
Service meshes handle several crucial aspects of mTLS, including certificate management, key rotation, and traffic encryption, often without requiring code changes to the application itself. This centralized management simplifies operations and reduces the burden on individual service teams.
- Certificate Management: Service meshes typically include a built-in certificate authority (CA) or integrate with existing CAs to issue and manage TLS certificates for each service. This automation eliminates the manual process of generating, distributing, and renewing certificates. For instance, Istio, a popular service mesh, uses its own CA to automatically provision and rotate certificates.
- Key Rotation: Secure key rotation is essential for maintaining the security of mTLS. Service meshes automate this process, regularly rotating private keys to prevent compromise. This ensures that even if a key is somehow compromised, its impact is limited by its lifespan. The frequency of key rotation is often configurable, allowing organizations to balance security and operational overhead.
- Traffic Encryption: Service meshes transparently encrypt all traffic between services within the mesh. This ensures that data in transit is protected from eavesdropping. The service mesh intercepts and decrypts traffic at the ingress and egress points of each service, applying mTLS encryption based on the configured policies.
Advantages of Using a Service Mesh for mTLS in a Microservices Environment
Integrating a service mesh with mTLS offers significant advantages in a microservices environment, contributing to enhanced security, simplified operations, and improved observability.
- Simplified Implementation: Service meshes abstract away the complexities of mTLS configuration, allowing developers to focus on application logic rather than security protocols.
- Centralized Management: A service mesh provides a centralized control plane for managing mTLS policies, certificate lifecycles, and key rotation, making it easier to enforce consistent security across all services.
- Automated Certificate Provisioning and Rotation: Service meshes automate the entire certificate lifecycle, reducing the operational overhead associated with manual certificate management.
- Improved Security Posture: By enforcing mTLS by default, service meshes enhance the overall security posture of the microservices environment, protecting against man-in-the-middle attacks and unauthorized access.
- Enhanced Observability: Service meshes provide visibility into the mTLS implementation, including metrics on encryption rates, certificate expiration, and connection failures, allowing for proactive monitoring and troubleshooting.
- Reduced Operational Overhead: Automating mTLS tasks like certificate issuance and key rotation reduces the operational burden on DevOps teams, freeing them to focus on other critical tasks.
Best Practices for mTLS Implementation
Implementing mTLS effectively requires careful planning and execution. Following best practices ensures that your service-to-service communication is secure, reliable, and maintainable. This section Artikels key recommendations for a successful mTLS deployment.
Securing Certificates and Private Keys
The security of your certificates and private keys is paramount to the integrity of your mTLS implementation. Compromise of these assets can lead to a complete system breach. Strict adherence to these practices is essential.
- Use Hardware Security Modules (HSMs): HSMs provide a secure, tamper-resistant environment for storing and managing private keys. They offer cryptographic operations, key generation, and key storage within a hardened device, significantly reducing the risk of key compromise. This is particularly critical for production environments.
- Implement Strong Key Management Practices: Employ robust key rotation policies, where certificates and keys are regularly renewed. This limits the impact of a compromised key. Utilize a Certificate Authority (CA) that supports automated renewal processes. Consider using short-lived certificates where feasible to further minimize the window of exposure.
- Secure Certificate Storage: Protect certificate stores with strong access controls. Restrict access to only authorized personnel and systems. Regularly audit access logs to identify and address any unauthorized attempts. Consider using secrets management systems to store and manage certificates securely.
- Enforce Key Length and Algorithm Best Practices: Use strong cryptographic algorithms and sufficiently long key lengths. Avoid deprecated algorithms like SHA-1. For example, RSA keys should be at least 2048 bits, and elliptic curve cryptography (ECC) keys should use appropriate curves such as secp256r1. This is crucial for protecting against cryptanalytic attacks.
- Regularly Audit and Review Certificate Inventory: Maintain an up-to-date inventory of all certificates, including their expiration dates, owners, and associated services. Conduct regular audits to ensure that certificates are valid, and that expired or revoked certificates are promptly removed. Use automated tools to track certificate lifecycles and send timely renewal reminders.
Monitoring and Auditing mTLS Configurations
Effective monitoring and auditing are essential for maintaining the security and performance of your mTLS implementation. Proactive monitoring allows for the identification and resolution of issues before they impact your services. Regular auditing ensures compliance with security policies and identifies potential vulnerabilities.
- Implement Comprehensive Logging: Enable detailed logging of all mTLS-related events, including certificate validation failures, connection attempts, and TLS handshake errors. Log the source and destination IPs, the certificate presented, and the outcome of the connection attempt (success or failure). Centralize these logs for easier analysis and correlation.
- Monitor Key Metrics: Track key performance indicators (KPIs) related to mTLS, such as the number of successful and failed mTLS connections, certificate expiration dates, and the latency of TLS handshakes. Use these metrics to identify performance bottlenecks and security incidents. Set up alerts to notify administrators of anomalies or deviations from baseline performance.
- Regular Security Audits: Conduct periodic security audits of your mTLS configurations. These audits should include reviews of certificate management practices, key storage security, and access controls. Ensure that the audit process covers all aspects of the mTLS implementation, from certificate issuance to service communication.
- Automated Alerting and Incident Response: Configure automated alerts to notify administrators of critical events, such as certificate expiration, failed connection attempts, and suspicious activity. Develop and document an incident response plan to address security incidents promptly and effectively. This plan should Artikel the steps to be taken in the event of a security breach, including containment, eradication, and recovery.
- Use a Centralized Management System: Utilize a centralized system for managing certificates, keys, and mTLS configurations. This simplifies the process of monitoring, auditing, and making changes to your mTLS implementation. This system should provide a single pane of glass for managing all aspects of mTLS, from certificate issuance to connection monitoring.
Designing an mTLS Strategy for a Specific Use Case
Designing an effective mTLS strategy requires careful consideration of your specific use case, the environment, and security requirements. This involves understanding the trade-offs between security, performance, and operational complexity. The following points should guide the design process.
- Identify the Scope and Requirements: Clearly define the scope of the mTLS implementation. Determine which services require mTLS protection and identify the specific security requirements, such as compliance with industry regulations (e.g., HIPAA, PCI DSS). Consider the sensitivity of the data being transmitted and the potential impact of a security breach.
- Choose the Right Implementation Method: Select the mTLS implementation method that best suits your needs. Consider the available infrastructure, the level of control required, and the operational overhead. Options include using service meshes (e.g., Istio, Linkerd), API gateways, or client-side libraries. Each approach has its own strengths and weaknesses.
- Define Certificate Authority (CA) Strategy: Decide whether to use a public CA, a private CA, or a combination of both. Public CAs provide trust and ease of use, but private CAs offer greater control and customization. Consider the lifecycle of your certificates, and ensure you have a plan for renewal and revocation.
- Assess Performance Implications: Evaluate the potential performance impact of mTLS. TLS handshakes and encryption/decryption operations can introduce latency. Optimize your configuration to minimize this impact. For example, use TLS session resumption and hardware acceleration where possible.
- Plan for Operational Complexity: Consider the operational complexity of implementing and managing mTLS. Automate as many processes as possible, such as certificate issuance, renewal, and revocation. Ensure that your team has the necessary skills and knowledge to manage the mTLS infrastructure.
- Develop a Rollback Plan: Have a plan to roll back the mTLS implementation if issues arise. This should include steps to revert to the previous configuration and troubleshoot the problem. Test your rollback plan before deploying mTLS in a production environment.
- Conduct Regular Testing and Validation: Regularly test your mTLS implementation to ensure that it is functioning correctly and that your security policies are being enforced. Perform penetration testing and vulnerability assessments to identify and address potential weaknesses.
Future Trends and Developments in mTLS
The landscape of mTLS is dynamic, constantly evolving to meet the demands of increasingly complex and distributed application architectures. Several trends are shaping the future of mTLS, promising enhanced security, simplified management, and broader adoption across various platforms and environments. This section explores these emerging trends and potential developments.
Advancements in Certificate Management
Certificate management is a critical aspect of mTLS, and advancements in this area are crucial for its widespread adoption and efficient operation. Automated certificate management systems are becoming increasingly sophisticated, simplifying the lifecycle of certificates.
- Automated Key Rotation: Automated key rotation is a key feature. It involves the automatic generation, deployment, and revocation of cryptographic keys. This significantly reduces the risk associated with compromised keys. Tools and platforms, such as HashiCorp Vault and cert-manager (for Kubernetes), offer robust capabilities for automating key rotation, minimizing manual intervention and human error. For example, a financial institution can automate key rotation for its internal microservices, reducing the window of vulnerability if a key is accidentally exposed.
- Certificate Automation Platforms: Platforms like Let’s Encrypt and commercial Certificate Authorities (CAs) provide APIs and automation tools that streamline certificate issuance, renewal, and revocation. These platforms integrate seamlessly with various infrastructure components, allowing organizations to automate certificate lifecycle management at scale.
- Integration with Infrastructure-as-Code (IaC): mTLS is increasingly integrated with IaC tools like Terraform and Ansible. This integration allows organizations to define and manage mTLS configurations as code, ensuring consistency, repeatability, and version control. This approach enables automated provisioning of certificates and configuration of mTLS across various environments.
Emerging Trends in mTLS Technology
The technology underpinning mTLS is also evolving, with several trends poised to impact its future.
- Zero-Trust Architectures: mTLS plays a central role in zero-trust security models. These models assume that no user or device is inherently trustworthy, and all access requests must be verified. mTLS enables the implementation of zero-trust principles by providing strong authentication and encryption for all service-to-service communications.
- Integration with Service Meshes: Service meshes like Istio and Linkerd have become popular for managing microservices architectures. They simplify the deployment and management of mTLS by providing built-in support for certificate management, key rotation, and traffic encryption. These meshes automatically handle the complexities of mTLS configuration, making it easier for developers to secure their applications.
- Hardware Security Modules (HSMs): HSMs provide a secure and tamper-proof environment for storing cryptographic keys. Organizations can integrate HSMs with their mTLS implementations to enhance security. Using an HSM for key storage and management adds an extra layer of protection against key compromise.
Evolving Role of mTLS in Securing Cloud-Native Applications
Cloud-native applications, built on microservices and containerization, are increasingly adopting mTLS for secure communication.
- Container Orchestration Platforms: Platforms like Kubernetes provide native support for mTLS, simplifying the deployment and management of certificates within containerized environments. Kubernetes Secrets can store certificates and keys securely.
- Microservices Security: mTLS is a critical component of microservices security, providing authentication, authorization, and encryption for inter-service communication. In a typical e-commerce platform, mTLS can be used to secure communications between the order processing service, the payment gateway service, and the inventory management service.
- Serverless Architectures: As serverless computing becomes more prevalent, mTLS is adapting to secure communication between serverless functions and other services. Solutions are emerging that provide mTLS support for serverless environments, ensuring secure communication within these dynamic and scalable architectures.
Ultimate Conclusion
In conclusion, mutual TLS (mTLS) emerges as a critical security measure for service-to-service communication, offering a strong foundation for secure and trustworthy interactions. By understanding its core components, implementation strategies, and best practices, you can confidently deploy mTLS to safeguard your microservices environment. As the digital landscape evolves, mTLS will continue to be a vital tool in protecting sensitive data and ensuring the resilience of modern applications.
Embrace the power of mTLS and fortify your service-to-service communication against potential threats.
Clarifying Questions
What is the primary difference between TLS and mTLS?
TLS (Transport Layer Security) primarily encrypts data in transit and authenticates the server to the client. mTLS (mutual TLS) goes a step further by requiring both the client and server to authenticate each other using digital certificates, ensuring a higher level of security.
How does mTLS enhance security compared to API keys?
mTLS provides stronger security than API keys because it relies on digital certificates and mutual authentication, which are more difficult to compromise. API keys can be stolen or leaked, whereas mTLS certificates have built-in mechanisms for revocation and are bound to specific identities.
What are the resource requirements for implementing mTLS?
Implementing mTLS requires managing digital certificates, which may involve a Certificate Authority (CA). This can introduce additional overhead for certificate generation, storage, and rotation. Additionally, there’s a slight performance impact due to the cryptographic operations involved in the handshake process, although this is usually minimal.
Is mTLS suitable for all types of service-to-service communication?
While mTLS is highly recommended for securing sensitive data and high-trust interactions, it might not be necessary for all types of communication. For example, internal services handling non-sensitive data may use other security methods. The choice depends on the specific security requirements and the sensitivity of the data being exchanged.